Information Systems in Accounting and Finance
Part A
Introduction
Transaction processing system or TPS is an advanced type of information system that enables companies to track and manage transactions globally. including data analysis dissertation help. It is a sophisticated revenue management system that produces desired performance forms by reporting and summarizing the inputs provided, including cash messages, customer orders, invoices, etc. It is an information management system that captures and processes every single transaction in the company. These transactions involve collecting, recapturing, modifying, and all other activities, leading to the recovery of all transactions. A transaction processing system is highly accurate, consistent, and effective. Transaction processing systems can also be known as processing systems in real-time. Processing transactions are also contrasted with batch processing (Wang& Kogan, 2018). These two processing systems are radically different and vary in their speed, processing, and accuracy. Since TPS is a real-time processing device, no delay can occur immediately in any event or transaction within or through the system. It is one of the most widely used technologies in all online transactions and is known as online transaction processing (OLTP). One of the most significant benefits of using a transaction processing system is that it manages an enterprise's essential transactions with a highly efficient system. Since the revenue structure is fully TPS-based, every company must operate seamlessly (Mahato & Singh, 2017).
SMEs and MNCs are at the heart of any country right now because they manage to maintain a countries economy mostly now during the pandemic session. SMEs and MNCs are the major victims and are the major ones that cyber-attacks target. In the last ten years, cybercrime has become a highly interesting problem and is now considered one of the world's most significant challenges in a business (Wang & Kogan, 2018). Therefore, we are going to asses some of the risks of using (a) online expenditure processing activities (b) online revenue cycle activities and (d) online conversion cycle activities within Smith brothers contracting business in the United Kingdom. Smith brothers has been doing tremendously good in the business market .Every aspect of everyday life is highly computerized, both private and work-related. The MNCs and SMEs all use the same basic infrastructure, using the same software, hardware, and standards via the transaction processing system - using devices connected (Mahato & Singh, 2017). According to a recent World Economic Forum (WEF) study, cyberspace threats are considered the biggest perceived potential and impact risks. In other words, Smith brothers risk facing cyber threat issues while using the Transaction processing system over the internet.

Without the development or rapid establishment of proper security policy and frameworks for protecting their systems, most cyber-attacks will occur on these systems. They would cause a lot of losses for Smith brothers (O'Leary, 2017). Theft of confidential and reliable TPS data is also a major hazard for Smith brothers. Know-how and intellectual property are the most important assets of a company. These are the incorporeal assets that arise from human creativity (HORIUCHI, 2020). They are located within MNCs and SMEs, and the company itself is invented and comprises architectural schemes, industrial inventions, utility models, product designs, labels, and recipes. The economic importance of these assets is increasing, especially at present due to the present economic crisis (Hasan, 2018). The stealing of an architectural contract could seriously damage a business. The theft of sensitive information concerns both domestic information (production of products, technologies, staff, financial information, etc.) and consumer and provider data (personal identity, credit card numbers or bank accounts, login credentials to the service offered by the victim company, email accounts, passwords, etc.) (Yan et al., 2018). These are the risks associated to (a) online expenditure processing activities (b) online revenue cycle activities and (d) online conversion cycle activities .The top ten pieces of data stolen in 2011 were, according to Symantec, personal information, date of birth, identification cards, personal addresses, physical data, telephone numbers, money, email addresses, usernames & passwords, and insurance data (Sulianta et al., 2019). Such attacks have a huge impact on a business.
With internal data theft, production may also stop or decrease (Ayub & Ali, 2018). When external information is robbed (e.g., Consumer information), sales can decrease owing to a loss of customer confidence and possible legal damages due to failure to maintain sensitive data. This represents, by far, the biggest risk for MNCs Smith brothers when the damage resulting from a loss of the brand or product catalog is difficult to fix. They also risk sabotage threats (Abualloush et al., 2017). These entrepreneurs Sabotage is a measure to delay or block Smith brothers enterprise activity, using means such as destroying valuable materials or equipment employed by the victim organization, by impediment to regular operations. In the meantime, there are many methodologies of the same players, targets, and means as a spy, both social and technical. In this situation, the TPS is the main substance that cybercrime can destroy (Lee et al., 2020).
Dig deeper into Accounting and Finance with our selection of articles.
Proposed solution
The technology is evolving continuously to offer greater and stronger characteristics. In parallel, like all technological advances, newer threats are revealed. More advanced computers provide fresher ways and endpoints for hacking and cracking (Sulianta et al., 2019). New technology creates new vulnerabilities and breaches to multinational companies' networks and processes and small and medium-sized enterprises (Lu et al., 2019). Advanced technological solutions can now build and produce various data types (for example, customer behavior, etc.) to give a hacker new motivation to break and collect the data. It looks like there can never be a time to build and deploy a perfect, impenetrable system before hackers detect vulnerable nodes (Sulianta et al., 2019). However, some steps can be taken by MNCs and SMEs to safeguard and protect the vulnerable network, data, and resources that form the backbone of activities in this information age. These factors include;
Security in system architecture
In relation to MNCs and SMEs or the TPS system architecture, their protection must be a fundamental necessity. Instead of being patched later, the device needs to be constructed with integrated safety. Safe coding standards must be practiced and protection incorporated in business processes during the construction of the system. To manage the data security of the organization, a separate position for information security officers must be established. The security approach is made complicated by the addition of security aspects after the company's architecture or structure is developed and implemented.
Strong password policy
Brute force assaults are common cyber assaults. Multiple character combinations are attempted to break into the system with such an attack. The system is weak because it is relatively simple to guess, using regular terms and names as passwords. It is impossible to destroy by brute force attack since a complex mixture of alphanumeric and special characteristics. Likewise, the longer the password, the better its protection. In reality, the brute forces needed to break in are doubled by each added character (Yan et al., 2018). Deactivating the login id means that brute force hackers don't get the possibility of trying all possible combinations after the predefined number of failed attempts. MNCs and SMEs, since this is the first line of protection against all attacks, these institutions need a strict password policy (Sulianta et al., 2019).
Strong Internet protection suites such as a firewall and a powerful antivirus
a) Firewall
The web traffic monitoring or even traffic between 2 internal networks enables an irregular and dangerous detection and control. It will help MNCs and SMEs block all unwanted traffic for their corporate needs. In addition to limiting unprofitable traffic, an active firewall strategy often stops traffic from all malicious sites protecting the company and its data network. Although several firewall solutions are available, choose the one suitable for your organization. The required protective depth and width will shape the main firewall selection parameters (Yan et al., 2018).
b) Powerful antivirus
It is a no-brainer; even though it costs a little more, MNCs and SMEs must choose the best antivirus they can afford. The main criteria for selecting the ideal antivirus program for their organizational needs are various parameters such as the geographical distribution of the workforce, movement of persons both within and outside the network (e.g., remote working), networking environment (in house, cloud, or third-party hosting) (Sulianta et al., 2019). Although most suppliers cover a broad range of viruses, malware, ransomware security, MNCs and SMEs can choose their software based on their response depth and pace. MNCs and SMEs need a fast response time for a vital mission system like healthcare, for example, but MNCs and SMEs need a solution that is ironclad for a high data volume market (Sulianta et al., 2019).
Part B
COSO is the acronym used for a model used for internal management and process testing and evaluation. In 1992, the Tread way Commission Sponsoring Organizations Committee developed guidelines for measuring the efficacy of internal inspections within a specific organization. The framework of COSO was named after the COSO Framework. This program was called COSO and offered a concept and insight into best practices for a brand's operations. The COSO structure is a model which outlines what internal control is, a continuous process controlled and affected by the management and the Board of Directors of the brand. Internal control, properly used, can contribute to operational performance, improve efficiency and even assist an entity to remain in line with regulations and legislation. COSO is divided into five different areas to make implementation simpler and ensure that nothing is missing (Thabit, 2019, April).
The five-key component in the COSO
The Control Environment
This part includes management, mission, objectives, and desired results. This is an important component of an organization's ethical policies and dedication to honesty, professionalism, and the structure of its hierarchy. Depending on the organization, its management and board of directors, the HR department, and their working relations with the staff and internal policies are part of your control environment. The company will operate more effectively with fewer struggles and risks if your control environment is safe. For this important COSO Framework aspect, the right people in the right position are essential to success (Anderson, 2017).
Risk Assessment and Management
What are the brand's challenges? This critical COSO aspect specifically targets and understands the organization's threats and weaknesses. Risk management involves a profound dive into the business's goals and, most importantly, how and how systems operate. The organization may face risks from external sources, from cyber-attacks and data theft to loss of ownership knowledge, formulas, and processes depending on the company and industry model (Prewett & Terry, 2018). The organization would also have to face major compliance and regulatory risks; healthcare, production, and growth brands are all exposed to industry risks. Risk discovery is only the beginning; studies, solutions, and improvements that reduce risk and avoid losses are part of this aspect. To better the organization, the more competitive you are, recognized and tackle risks (Karanja, 2017).
Control Activities
The COSO Framework Element discusses organization strategies, procedures, the implementation of the organization's safety, and your plans for continuity management. A comprehensive business continuity plan combined with proactive security and upgrade strategy in an emergency ensures that organization control operations are aligned with their objectives. The more successful your strategies are when it comes to outlining rules and goals, the more successful an organization can be (Fox, 2018).
Outsourcing
How well these external resources are handled, and what variables, duties, and tasks do you outsource? The knowledge and organization communication and the way they transmit it greatly impact their ability to outsource critical projects and activities efficiently and appropriately. Evaluation of how well they communicate and how well their expectations are met means that the organization's money is invested intelligently and that you get the best outsourcing return (Lanz, 2018).
Monitoring
It is a good start to create the environments under which an organization wants to work and the policies that their team wants to apply, but they cannot keep up with changes unless they track and review the processes. Continuous monitoring will help an organization identify inefficiencies and shortcomings, encourage a firm to act and control the organization (Chan et al., 2020). The five internal control components work together to build an efficient internal control system. To build a culture of enforcement within a company, they need a controlled environment. Upon supporting and influencing management, a risk evaluation mechanism may be developed to identify and handle threats that impede the achievement of internal control aims. They can then carry out control tasks that fulfill their internal control goals and use good communication within an organization. A company will concentrate on achieving internal control goals through a continuous monitoring program (Schmidt, 2020).
Application of COSO in Curve
Curve is an SME Fintech firm that links all existing debit and credit cards to its standalone contactless card. This means that a user must only have a card to buy, although they have many different cards and can monitor their spending patterns through the Curve's platform (Rae et al. 2019). This is why we will address how COSO will reduce employee and business fraud in this small business. COSO is the most powerful tool to prevent and detect fraud and to control fraud internally. COSO is nevertheless acknowledged as a leading system for internal control conception, implementation and behavior, and internal controls assessment (Shad et al., 2019).

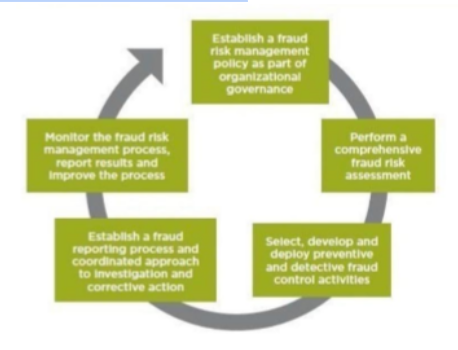
Using COSO Curve, can set strategies, create goals and develop plans to accomplish a mission and vision. Targets may be set for a whole organization or individual entity activities. The model can help the organization identify and evaluate risks and develop appropriate responses, focusing more on counter-fraud measures and removing inefficient and redundant controls that offer the organization little value. The Anti-fraud Guide is building on the 2013 COSO Internal Control-Integrated Framework, which increased the possibility of fraud to achieve the organization's goals (Trautman & Kimbell, 2018). A full evaluation of fraud risks, distinguished from the risks of internal control errors, is recommended in the Anti-fraud Guide. Curve may also set up a robust fraud risk management program in the Anti-fraud Guide (Thabit, 2019, April). The Anti-fraud Guide provides the information and instruments required to perform a fraud risk assessment, develop an anti-fraud strategy, and develop a robust anti-fraud program in order to support this recommendation.
The principles of fraud will help an organization address fraud risk management by establishing an ethical (not merely compliant) conduct basis and a "corporate management program, directly relevant to the risk of fraud." The Guide on fraud control notes that the ultimate role of fraud risk management is "essential to the performance of a fraud risk management program for the one executive member to be appointed to the board and to report to it regularly (Anderson, 2017). By using fraud risk assessment to define particular schemes, assess their probability and possible impact, and assess the company controls' efficacy, they may assist their organization in assessing fraud risk (Prewett & Terry, 2018). Risk tolerance is a vital factor, as recognized under the Anti-fraud Guide; Curve should invest in managing the most crucial risks. This Anti-fraud Manual outlines the anti-fraud practices in human resources, including background inspections, incentives, responsibilities and employee surveys, exit interviews, and the method of confidential reporting or whistleblower. The Anti-fraud Guide also highlighted the controller's issue override of management and stated that executive officials had committed a few disastrous frauds in the past (Karanja, 2017).

Data analysis is a COSO tool that Curve can use to evaluate risk management of fraud. Increasingly regulators are using data analytics to detect professional advice on fraud needs auditors to use analytics to determine fraud risk. Data analysis tools may help isolate possible fraud transactions or patterns," can "continue to investigate anomalous trends rather than enforce expensive or invasive controls to deter every fraudulent transaction" and can encourage investigations and control remedies (Fox, 2018).
Constitution
It is recommended that Curve should form a team made up of members from various departments and businesses with various perspectives on the company. They should then look at the latest fraud risk evaluations of the organization and see whether they provide an accurate view of the enterprise's vulnerabilities and the sound groundwork for management decisions on resource deployment. Clients are turned into a timely and skillful EY Fraud Investigation & Dispute Services (FIDS) practice while confronting fraud, government investigations, administrative investigations, major litigations, or transactional disputes. In collaboration with our client's legal advisors, internal audit teams and regulatory agencies, FIDS' forensic accounts and other industry experts are involved in studying and assessing challenging problems and building hands-on solutions to operational challenges. The transaction processing system (TPS) and Supply Chain Management (SCM) have a specific role to ensure an enterprise can successfully and efficiently achieve its goals. This information system is very useful for the business organization's activities.
Reference
Abualloush, S., Bataineh, K., & Aladwan, A. S. (2017). Impact of information systems on innovation (product innovation, process innovation)-field study on the housing bank in Jordon. International Journal of Business Administration, 8(1), 95-105.
Anderson, D. (2017). COSO ERM: Getting risk management right: Strategy and organizational performance are the heart of the updated framework. Internal Auditor, 74(5), 38-43.
Ayub, M. B., & Ali, N. (2018). Performance comparison of in-memory and disk-based databases using transaction processing performance council (TPC) benchmarking. Journal of Internet and Information Systems, 8(1), 1-8.
Chan, K. C., Chen, Y., & Liu, B. (2020). The linear and non-linear effects of internal control and its five components on corporate innovation: Evidence from Chinese firms using the COSO framework. European Accounting Review, 1-33.
Fox, C. (2018). Understanding the New ISO and COSO Updates. Risk Management, 65(6), 4-7.
Hasan, F. F. (2018). A Review Study of Information Systems. International Journal of Computer Applications, 179(18), 15-19.
HORIUCHI, S. (2020). DEVELOPING A PROCESS MODEL OF BUSINESS TRANSACTION WITH DEMO. DAAAM International Scientific Book.
Karanja, E. (2017). Does the hiring of chief risk officers align with the COSO/ISO enterprise risk management frameworks?. International Journal of Accounting & Information Management.
Lanz, J. (2018). Enterprise Technology Risk in a New COSO ERM World: Eight Challenges Facing Management. The CPA Journal, 88(6), 6-10.
Lee, J., Kim, K. H., Lee, H., Andrei, M., Ko, S., Keller, F., & Han, W. S. (2020). Asymmetric-partition replication for highly scalable distributed transaction processing in practice. Proceedings of the VLDB Endowment, 13(12), 3112-3124.
Lu, Y., Wang, X., Wei, R., Gao, Y., Huang, Z., & Xie, Y. (2019, December). Design of Transaction System for Remote Sensing Cloud Service based on Blockchain. In Proceedings of the 2019 2nd International Conference on Blockchain Technology and Applications (pp. 81-85).
Mahato, D. P., & Singh, R. S. (2017). Balanced task allocation in the on‐demand computing‐based transaction processing system using social spider optimization. Concurrency and Computation: Practice and Experience, 29(18), e4214.
O'Leary, D. E. (2017). Configuring blockchain architectures for transaction information in blockchain consortiums: The case of accounting and supply chain systems. Intelligent Systems in Accounting, Finance and Management, 24(4), 138-147.
Prewett, K., & Terry, A. (2018). COSO's Updated Enterprise Risk Management Framework—A Quest For Depth And Clarity. Journal of Corporate Accounting & Finance, 29(3), 16-23.
Rae, K., Sands, J., & Subramaniam, N. (2017). Associations among the five components within COSO internal control-integrated framework as the underpinning of quality corporate governance. Australasian Accounting, Business and Finance Journal, 11(1), 28-54.
Saleem, K. S. A., Zraqat, O. M., & Okour, S. M. (2019). The Effect of Internal Audit Quality (IAQ) on Enterprise Risk Management (ERM) in Accordance to COSO Framework.
Schmidt, C. (2020). Why risk management frameworks fail to prevent wrongdoing. The Learning Organization.
Shad, M. K., Lai, F. W., Fatt, C. L., Klemeš, J. J., & Bokhari, A. (2019). Integrating sustainability reporting into enterprise risk management and its relationship with business performance: A conceptual framework. Journal of Cleaner production, 208, 415-425.
Sulianta, F., Rosita, A., Zulpratita, U. S., Heryono, H., Laksana, E. A., & Yuliani, S. (2019). Different Kinds of Modern Technique to Develop Various Information Systems. International Journal of Advanced Science and Technology, 28(6), 68-75.
Thabit, T. (2019, April). Determining the effectiveness of internal controls in enterprise risk management based on COSO recommendations. In International Conference on Accounting, Business Economics and Politics.
Trautman, L. J., & Kimbell, J. (2018). Bribery and Corruption: The COSO Framework, FCPA, and UK Bribery Act. Fla. J. Int'l L., 30, 191.
Wang, Y., & Kogan, A. (2018). Designing confidentiality-preserving Blockchain-based transaction processing systems. International Journal of Accounting Information Systems, 30, 1-18.
Yan, X., Yang, L., Zhang, H., Lin, X. C., Wong, B., Salem, K., & Brecht, T. (2018, May). Carousel: Low-latency transaction processing for globally-distributed data. In Proceedings of the 2018 International Conference on Management of Data (pp. 231-243).
Take a deeper dive into Implications For Borac Plcs Subsidiary with our additional resources.
- 24/7 Customer Support
- 100% Customer Satisfaction
- No Privacy Violation
- Quick Services
- Subject Experts



