Firewall Bypass with VPN Technology
Introduction
Like some countries which have banned access to some internet content such as website and social media platforms, institutions as well as Internet Service Providers limit employees and users respectively from accessing some of their sites content driven such reasons enhance productivity, and limit distraction during work mostly done through access to social media platforms through their networks. However, there are instances where these firewalls are bypassed, whereby certain products or services are all over the Internet are applied to do so. The most common used technology used to bypass firewalls is the Virtual Private Network (VPN).

Specifically, VPN is largely used by mobile device users that are affected by egress filtering and are inform of applications used in Apple and Android Operating systems and other of the similar kind that can be used to bypass vented firewalls. In this report, the focus is to provide detailed on how to set up a Virtual Private Network (VPN) to bypass firewalls.

Virtual Machine Setup
Two machines are required within the firewall and another outside it, whose purpose is to assist in the communication from the inside to the outside of the blocked firewall sites. These machines are labeled VM1 and VM2 that are linked with Internet provider by routers. It can be made simple by use of Local Area Network (LAN) to mimic the connection of the Internet, but would require a NAT Network Adapter to basically link VM1 to VM2. Below is the setup of virtual machines VM1 and VM2;

Setting Up of Firewall
When setting up of a firewall, there is need to block the access of a target website on VM1 and ensure that the Internet Protocol address of the target web site is either in a fixed range or it is fixed. It is meant to curb blockage of the website. Therefore, a super-user privilege is needed to set up the firewall on VM1, as well as the setting up of VPN tunnel. The purpose is to avoid developing another VM in the lab environs, but then configuration of the firewall is inaccessible with super-user privilege, but with VPN, chances are more in bypassing the firewall. Firewall is set up to block packets, but leave out packets meant to support virtual interface meant to be applied by the VPN. So, routing is set up before the firewall rule that also is not set up on the virtual interface. Consequently, the firewall rule is set on the VM’s actual network interface, so that it does not affect the packets that go the virtual interface. Below is figure 2 showing the setting up of VPN server program TUN network interface that appears in the framework depicted as “ifconfig –a” command;

Bypassing Firewall using VPN
In this lab task, a VPN tunnel is established between VM1; VPN client VM and VM2; VPN Server VM. A user in VM1 attempts to access the sites, they are blocked, and they will not go through a network adapter due to blockage. In lieu, the packets to the blocked site from VM1 will be sent along a path to the VPN tunnel and gets to VM2. On arrival, VM2 will direct them to the last stop. When the reply packets are directed back, it will get to VM2, which consequently redirect the packets to the VPN tunnel, and finally direct the packet back to VM1, thus aiding VPN to bypass the firewalls. A developed sample of VPN program as well as a client program depicted as (vpnclient) not leaving out a server program; vpnserver, where these two programs can be downloaded from website and it is meant to establish a simple VPN tunnel between the server and the client, and does not encrypt the traffic in the tunnel. The VPN server is shown below.
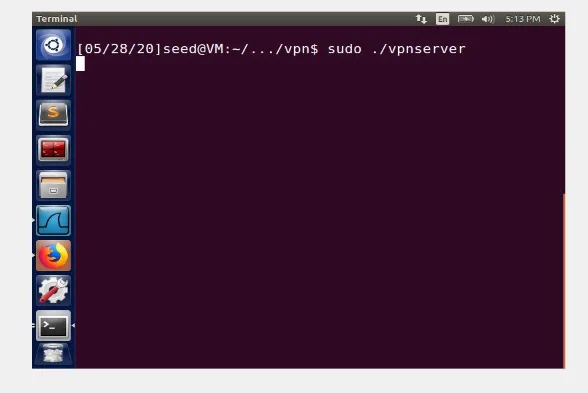
These two programs; vpnclient and vpnserver are the two ends of the VPN tunnel, and communicate between themselves by use of User Datagram Protocol (UDP) or Transmission Control Protocol (TCP) through sockets, but UDP is the most preferred due to its simplicity in establishing low-latency and loss-tolerating linkages between apps on the Internet. The VPN server and client programs link to the hosting framework through a TUN interface; a software loopback mechanism than can be loosely described as the network interface analog of the pty (4), via which two things are done shown on the figure 4 below;
These include; (i) acquire IP packets from the hosting framework, so the packets are directed to the tunnel, (ii) acquire IP packets from the tunnel, then push them to the hosting framework, which will forward the packet to the last destination as show in figure 5 below;

Therefore, in summary, there are four steps unto which a VPN can bypass firewalls. They include;
Step 1: Running VPN Server- The initial step is to run the VPN server program TUN network interface will appear in the framework depicted as “ifconfig –a” command, and the name of this interface will be tun0 in several occasions, but then they can also be tunX, where X is a number), as depicted in figure 4. Below is figure 6 showing the use of ufw; a firewall configuration tool for iptables, and a cheat sheet-style guide that offers a quick reference to UFW commands that will develop iptables firewall rules;

Step 2: Running VPN client program on the client VM. The first command will link to the VPN server program running on 10.0.2.8. The command will block, thence, another window to configure the tun0 interface developed by the VPN client program. Below is figure 7 showing the use of ufw command meant to create iptables firewall rules;


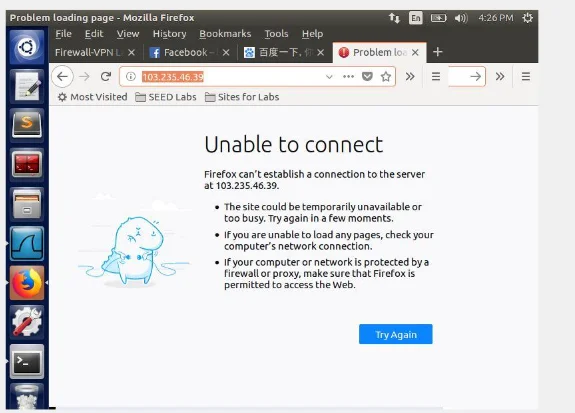

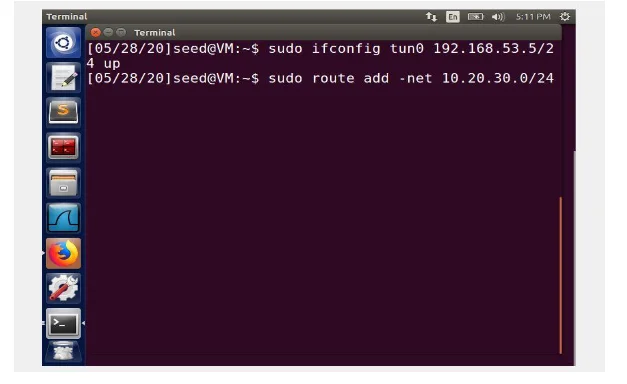
Step 3: A route is set up on Server and Client VMs to both machines to direct the intended traffic via a tunnel established. In this case a route command is added on the routing entries set up accordingly so that the traffics to the blocked sites will be routed towards the VPN. Step 4: In this final step, Network Address Translation (NAT) adapter is set up on Server VM, which translates Internet Protocol address applied in the network to a varying IP address known within another network. Packets are sent back to the users, these packets are sent to the VPN server’s NAT adapter first, since the source IPs of all the outgoing packets from the VM server are adjusted to the NAT’s external IP addresses, basically the host computer or mobile device IP address within the set up. In most cases, the NAT replaces the destination IP address with the IP dress of the official packet, and return to whoever possesses the IP address.
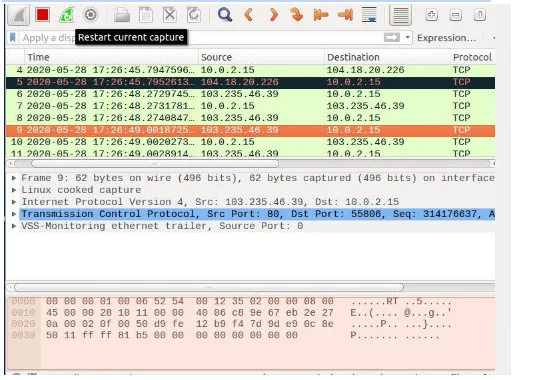
Conclusion
Following these steps correctly will enable one to bypass the firewall using VPN. One must show that he or she is capable of arriving the blocked web site from Client VM through the VPN. The same solution developed must also show that they are capable of working on other traffic not only on web traffic. Following the four steps of running VPN server program, then running VPN client program on the client VM for linkage with server, a later a route is developed in form of a tunnel, is capable of channeling packets back and forth.
Take a deeper dive into Introduction to VoIP Security Risks with our additional resources.
References
Fujikawa, H., Yamaki, H., Yamamoto, Y. and Tsuruta, S., 2016, July. Intelligent bypass method Exploiting VPN for stable offshore business on the Internet. In 2016 World Automation Congress (WAC) (pp. 1-7). IEEE.
Du Wenliang. (2018). Bypassing Firewalls using VPN. SEEDS Labs- Firewall EvasionLab:
- 24/7 Customer Support
- 100% Customer Satisfaction
- No Privacy Violation
- Quick Services
- Subject Experts



