Enhancing Web Application Security
- 15 Pages
- Published On: 13-12-2023
Introduction
The research methodology is one of the most important parts of the paper and comprises a systemic and theoretical project study of adaptation models or theories. The aim of the project is a web application FIREWALL security measure with a protection from SQL injection ,XXS scripting Cookies etc given the fact that conventional firewalls are not good enough therefore a WAF is used as first layer then a Web application honeypot as SECOND layer to WAF because some attacks can escape the WAF layer. For students seeking engineering dissertation help, understanding all these layers of security is critical for developing comprehensive protection strategies.
Web application for protection from SQL and XSS
SQL Attacks are the expensive and important attacks on web application, allowing an attacker to get unlimited access to database and possibly sensitive information including usernames, passwords, e-mail ids, credit card details. Different methods for addressing the SQL attack issue have been suggested, including defense coding, identification and prevention, as well as intrusion detection. Most of these approaches have however one or more drawbacks, such as code change requirements for restricted attack types and web-based apps. Honey pots in this design are designed and deployed in virtual environment Linux environments. Honey pots are then targeted by using open source scanning tools to simulate various exploitations and then evaluate experimental outcomes (Akbar, & Ridha, 2018).
Honeypot
A honeypot is a computer system or device designed to mimic likely cyber-attack targets. It can be used to detect or remove attacks from a valid target. You will also learn how cyber criminals function.

Cross-site scripting (XSS)
Cross site scripting (XSS) is injected into an existing approved program when an attacker adds or injects their own code. These can either directly jeopardize a single site or break a third-party script that accesses all the pages on the site at once (Babiker et al., 2018). These attacks can cause malicious code to be sent to others, and malware that displays their sensitive information can infect customers (Akbar & Ridha, 2018). DOM-based XSS attacks are the worst, since the vulnerability is not server-side code but clients, so that it can never be seen in the server (Latha, and Prakash, 2017).
SQL injection
SQL is a method used to inject SQL query into input fields and process them in the SQL database below, by attackers (Babiker et al., 2018). These vulnerabilities can be exploited when entry forms enable SQL statements provided by users to directly query the database. Take a user and email field as well as a password field to give you an example scenario. The SQL query is merged on your Web server after you receive the login information. The command in PHP is written as follows:
It is sent to the server to check if a correct username has been provided with an applicable password. This command would result in a username "james" with the password "1111":
However, the question will look like that when you put something like "james;—"
However, if you put "james' something;— The intruder uses SQL comment syntax in this example. The rest of the code will not be executed after the twin-dash sequence.
Design of DShield web application honey pot
DShield is one of the honey pots used and configured in CentOS 6.4 Linux Server with the low-interaction web application. Honey-pot will include the PHP-based scripting engine-in-the-engine PHP web server. This deployment of a sweet pot would include "testing" pages and no real web site implementation (Ross et al., 2018). This device is a zombie program for testing the capacity of the honey pots. Then this sweet pot system will be targeted using software and tools from third parties (using BackTrack Linux) to behave as end users and simulate various behaviors on this sweet pot system (Latha, and Prakash, 2017)
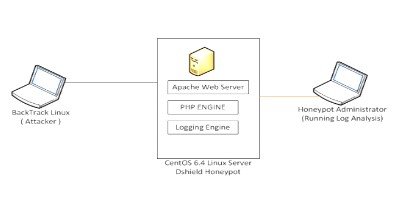
The Dshield device test demonstration that will be checked is shown in Figure-1. This system would also record the logs created by the logging engine that the system administrator would examine. This is the high-level approach to build a DShield "test system."
Design of Glastopf web application honey pot
Glastopf is a honey pot that emulates a wide range of web-application attacks, including SQL injection. This sweet pot has been deployed and installed on an Ubuntu 12.04 Linux server. It operates with a PHP sandbox that also has the ion Linux server installed, on the top of the python scripting engine. Glastopf is able to log extensively and can log all the aspects of the attacker interaction (Negi et al., 2020). Since it is a honey pot of low interaction, it is difficult to compromise, and therefore very healthy. The website that the glastopf serves is made with Python code and is shown to the attacker as a PHP application (Ng et al., 2018).
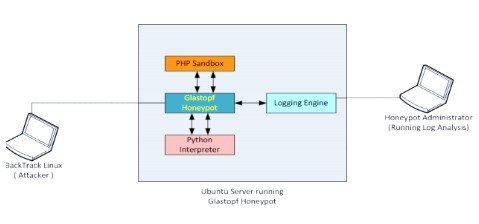
Figure-2 demonstrates the test demonstration for the Dshield device that will be tested. The honey pot framework can then be probed and targeted using open source web-security software that come pre-installed with Backtrack Linux or can be downloaded freely from the internet (Eliot et al., 2018). Malicious, the PHP code that the attacker is injecting is run by the honeypot in the PHP sandbox, which results in the attacker being seen (Ross, 2018). This ensures that the attackers can see what they want, i.e. the actual performance produced by a successful attack. Those protection instruments will allow the honey pot device attacker to simulate various attacks. The system administrator would then analyze the logs which were created during the attack (Nadeem et al., 2017). This is the high level approach to build Glastopf's "test system."
Continue your journey with our comprehensive guide to Methodology and Approach to the Research.
Simulation attacks on honey pot frameworks for web applications.
Different types of attacks are simulated on honey pots on the web application. All attacks would be replicated with third-party software and the honey pot systems would also be tested if manually required (Rahman et al., 2017). This simulation of attacks will be carried out during the project's experimental stage.
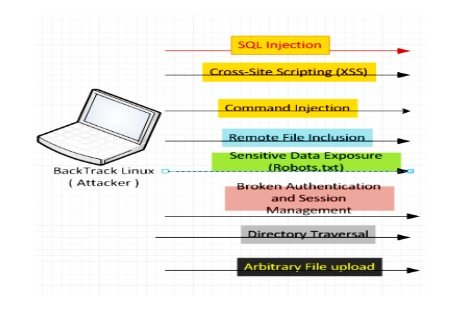
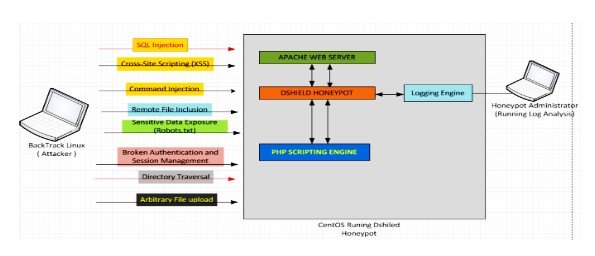
In this method, different logs will be recorded according to the attacks simulated using different tools and software for penetration testing. The DShield honeypot is supposed to respond to the attacking machine (user), and the logging system connected with the DShield honeypot system captures all this data. These logs can later be analyzed using the 'Apache Scalp' log analysis tool for verification of attack patterns.
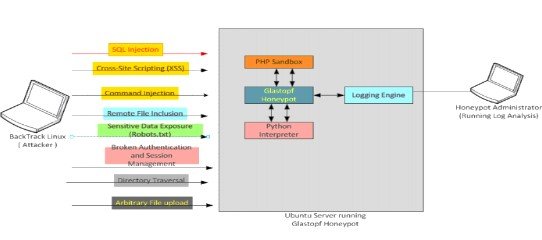
In this method, different logs will be recorded according to the attacks simulated using different tools and software for penetration testing. Glastopf honey pot is supposed to return to the attacker and the logging system that is attached to the Glastopf honey pot system will then collect all of this information (Baykara & Das, 2018). These logs will subsequently be reviewed so that the attack patterns are checked and the outcomes are captured.
Web application firewalls in use today
Microsoft Azure Web Application
In the technology industry, Microsoft is one of the pioneers and has extensively developed knowledge of security. In terms of technology, they are the world's leading brands. Who might have more faith in our company than Microsoft? Microsoft Azure Web Application Firewall has a variety of security features that defend against malicious virus attacks, which are growing rapidly because of the current boom over web-based applications due to the Covid 19 crisis (Cernica & Popescu, 2018). The Azure Web application Fire wall can be used by various approaches, as discussed below.
Azure Application Gateway 2. Azure Front Door Azure ContentWe went a little further on with the azure front door, which was the best for us. The request and the requirement may be susceptible. Every Azure WAF has a limited output that plays an important role in selecting the one that you should be using. When it comes to this aspect, it is very versatile. Both Azure front door support WAF (Web application Firewall) HTTPS, IPv6 and IPv4. One of the best parts of this WAF is its deployment period of just five minutes or even less, so that several failure times during deployment are not affected (Raj et al., 2020). We as a company are satisfied that the product is performing and that the customers are responding greatly (Kindy, & Pathan, 2012). The migration of data is a concern of the organization and data protection is essential to our clients. What’s more reassuring for a consumer if he knows that our application is just one of the world leaders in the IT Industry (Hu et al., 2020).
Methodology on Microsoft Azure Web Application
In a use-based usage model, Cloud Computing is the collection of technologies and infrastructure capabilities. Microsoft cloud computing provides Microsoft Azure to support its customers in the benefit of cloud computing, which is known previously as Windows Azure (Kindy, & Pathan, 2012).
Application and Development
The most common code for Azure applications is installed locally on a developer's machine during the application development stage. Microsoft recently introduced Azure Apps called Azure Functions with additional services. They reflect 'server less' computing and enable developers to directly create application code using references to several Azure resources via the Azure portal. There are two stages of the application development process: Build + test, and Deploy + monitor (Raj et al., 2020).
Construct and Test
A Windows Azure application is integrated into Visual Studio IDE during development and testing (2010 or above). Developers that use Azure services in non-Microsoft applications can do so with their current development platform. Community-built libraries are available and make it possible, such as Eclipse Plugins, Java SDKs, PHP or Ruby (Hu, 2017). Visual Studio Code is a platform designed to better support developers and understand their needs for lighter yet highly configurable tools as part of Microsoft's initiative. For Windows, Mac, and Linux, this source code editor is now open. Its JavaScript, TypeScript and Node.js are supplied with built-in. The ecosystem is also rich in extension and runtimes for other languages including C++, C#, Python, PHP and Go (Akbar, & Ridha, 2018). Visual Studio and Azure SDK provide Azure project infrastructure and code creation and deployment from the IDE directly. The web host, website, and database for an application can be defined by a developer, and deployed with the code without Visual Studio ever being abandoned (Hu, 2017).
Azure App Service
Web apps: websites or applications written in .NET, Java, PHP, Node.js and Python Web applications
Mobile Apps: mobile application support projects that enable social providers and the Azure Active Directory to authenticate (Azure AD); Projects that have backend storage and integrate with push notification hubs
Swagger Apps: Securely exposed cloud APIs so that clients figure out quickly how to use them API Apps
Logical applications: strong integration solutions that can be easily developed using the many connectors — customized or out-of-box connectors may be installed. When you're out of the box, you're prepared, anywhere—on site or in the cloud-with data and computers. Salesforce, Office 365, Twitter, Dropbox, Google Services and more are some of the currently available SaaS and cloud connectors.
With continuous integration and distribution in mind, Azure Web Apps are developed. They support various tools such as GitHub Webhooks, Jenkins, TeamCity, etc.
Summary
In this methodology, the honeypot used was DShield as it is one of the best methods used to protect websites. Dshield is a honeypot at the production stage, recommended for the web application detection, log- search and attack, along with existing web servers, in the DMZ (Li et al., 2019). Dshield is only a PHP-based program with minimal interaction to an attacker and unable to simulate advanced vulnerabilities, such as SQL injection (Babiker et al, 2018). The gold of the DShield Web App is to collect quantitative data against web applications measuring the operation of automated or semi-automated samples. It is therefore possible to see that Dshield honeypot is generated to log common attacker’s information and IP addresses. This information is then shared with other group members who can block the attackers in the firewall (Hu, 2017). Moreover, this methodology also did not show practical screenshots of the attack and prevention scenario this is because, Azure has a series of security features built into its firewall by default: service protection denial, access control lists (Azure calls them NSGs), simple traffic monitoring. Advanced features like IPS/IDS or advanced traffic and filtering also require a specific firewall.
In addition, we selected Microsoft Azure as one of the best firewall used today to protect web pages. Microsot Azuri was selected because, Azure makes it easier and faster to build, deploy, and manage applications without having to purchase and/or maintain the basic infrastructure. The integrated cloud capabilities of Azure meet all of your security and enforcement criteria and can easily be adapted to the specific needs of an organization. This study aim to implement a WAF-like server that will serve as a proxy to any main server in this project. The activity of attacks performed on any main server is monitored using WAF. Through examining the type of attacks, the system designers will upgrade the system to protect all the system loopholes. Glastopf is best used in the network alongside production web servers or in a separate firewall/IDPS-protected DMZ (intrusion detection and prevention system). The glastopf-generated logs can detect attacks on web applications on production network web servers and help collect information on these attacks including an IP address, resources, and techniques. This knowledge can be used to protect web application servers further and can detect web server co-ordinate attacks as well.

Reference
Akbar, M., & Ridha, M. A. F. (2018). SQL Injection and Cross Site Scripting Prevention using OWASP ModSecurity Web Application Firewall. JOIV: International Journal on Informatics Visualization, 2(4), 286-292.
Babiker, M., Karaarslan, E., & Hoscan, Y. (2018, March). Web application attack detection and forensics: A survey. In 2018 6th International Symposium on Digital Forensic and Security (ISDFS) (pp. 1-6). Ieee.
Baykara, M., & Das, R. (2018). A novel honeypot based security approach for real-time intrusion detection and prevention systems. Journal of Information Security and Applications, 41, 103-116.
Bhagwani, H., Negi, R., Dutta, A. K., Handa, A., Kumar, N., & Shukla, S. K. (2019, December). Automated classification of web-application attacks for intrusion detection. In International Conference on Security, Privacy, and Applied Cryptography Engineering (pp. 123-141). Springer, Cham.
Negi, P. S., Garg, A., & Lal, R. (2020, January). Intrusion detection and prevention using honeypot network for cloud security. In 2020 10th International Conference on Cloud Computing, Data Science & Engineering (Confluence) (pp. 129-132). IEEE.
Caesarano, A. R., & Riadi, I. (2018). Network forensics for detecting SQL injection attacks using NIST method. Int. J. Cyber-Security Digit. Forensics, 7(4), 436-443.
Eliot, N., Kendall, D., & Brockway, M. (2018). A flexible laboratory environment supporting honeypot deployment for teaching real-world cybersecurity skills. IEEE Access, 6, 34884-34895.
Hu, H. (2017). Research on the technology of detecting the SQL injection attack and non-intrusive prevention in WEB system. In AIP Conference Proceedings (Vol. 1839, No. 1, p. 020205). AIP Publishing LLC.
Hu, J., Zhao, W., & Cui, Y. (2020). A Survey on SQL Injection Attacks, Detection and Prevention. In Proceedings of the 2020 12th International Conference on Machine Learning and Computing (pp. 483-488).
Kindy, D. A., & Pathan, A. S. K. (2012). A detailed survey on various aspects of SQL Injection: vulnerabilities, innovative attacks, and remedies. Information Journal.
Latha, S. and Prakash, S.J. (2017). A survey on network attacks and Intrusion detection systems. In 2017 4th International Conference on Advanced Computing and Communication Systems (ICACCS) (pp. 1-7). IEEE.
Li, Q., Li, W., Wang, J., & Cheng, M. (2019). A SQL injection detection method based on adaptive deep forest. IEEE Access, 7, 145385-145394.
Nadeem, R. M., Saleem, R. M., Bashir, R., & Habib, S. (2017). Detection and prevention of SQL injection attack by dynamic analyzer and testing model. International Journal of Advanced Computer Science and Applications, 8(8), 209-214.
Ng, C.K., Pan, L. and Xiang, Y., 2018. Honeypot frameworks and their applications: a new framework. Springer Singapore.
Rahman, T. F. A., Buja, A. G., Abd, K., & Ali, F. M. (2017). SQL Injection Attack Scanner Using Boyer-Moore String Matching Algorithm. JCP, 12(2), 183-189.
Raj, R. J. S., Prakash, M. V., Prince, T., Shankar, K., Varadarajan, V., & Nonyelu, F. (2020). Web Based Database Security in Internet of Things Using Fully Homomorphic Encryption and Discrete Bee Colony Optimization. Malaysian Journal of Computer Science, 1-14.
Ross, K., Moh, M., Moh, T. S., & Yao, J. (2018). Multi-source data analysis and evaluation of machine learning techniques for SQL injection detection. In Proceedings of the ACMSE 2018 Conference (pp. 1-8).
Vetterl, A. and Clayton, R., 2019, November. Honware: A virtual honeypot framework for capturing CPE and IoT zero days. In 2019 APWG Symposium on Electronic Crime Research (eCrime) (pp. 1-13). IEEE.
Looking for further insights on Employee Engagement and Retention at Philips Trust Corporation? Click here.
- 24/7 Customer Support
- 100% Customer Satisfaction
- No Privacy Violation
- Quick Services
- Subject Experts



