Computer and Mobile Forensics
Executive summary
In this report I used technology and normal methods to analyse the material required to answer the questions that was posted for investigations concerning Jean. After a in-depth analysis of the matter I came to realise that Jean created the data, but the evidence revealed that she was a victim of a spear-phishing assault. Her computer had not been hacked, but as the accused, she did not intentionally divulge the material. It was also obvious that no other staff members were actively involved in the infringement as the information obtained only covered to workers in the organisation. The findings show that jean and other employees are innocent of the crime however there are other issues such as malware that might have caused the issue to take place. This situation highlights the importance of seeking computer science dissertation help to understand the complexities of cybersecurity further.

The spreadsheet sent from Jane's computer (The M57.biz) to Alison@m57.biz was faked, resulting in the file being received by another email address with an hotmail.com domain. Because the email address does not contain the organization's end address M57.biz, it is possible that a spear-phishing attack occurred just as Jean sent the email; as a result, the company and Jean and Alison is both victims of spoofing. That means the company should implement some of the recommendations to secure its systems in order to avoid such misinterpretations.
Introduction
Case Background
According to the scenario presented, M57.biz is a web-based start-up that is creating a body art collection. The following are the facts that are associated with the company: $3 million in preliminary capital, with a $10 million round of funding on the way, two founders, and ten staff employed in the first year. Additionally, the company is made up of the following team members, President: Alison Smith, CFO: Jean and Programmers: Bob, Carole, David, Emmy, and Marketing: Gina, Harris, and BizDev: Indy. Knowing the team members is very much important for the investigations as it will help to prove whether Jean is guilty or not. On a competitor's website's tech support page, a table containing sensitive and personally identifiable data (PII) was submitted as an attachment. The table was taken from CFO Jean's PC. This report is purposely meant to look into the matter and figure out how the materials that were posted landed up to the competitor's website and who was involved as the current evidence points at CFO Jane.
The main objective of Alison Smith the president of the organisation is to find out who is leaking the company’s information to their competitors because this is a very sensitive issue that must be handled accordingly as the company risks being overtaken by their competitor in the business environment. Furthermore, the corporation wants to know who was in charge of carrying out the following actions:
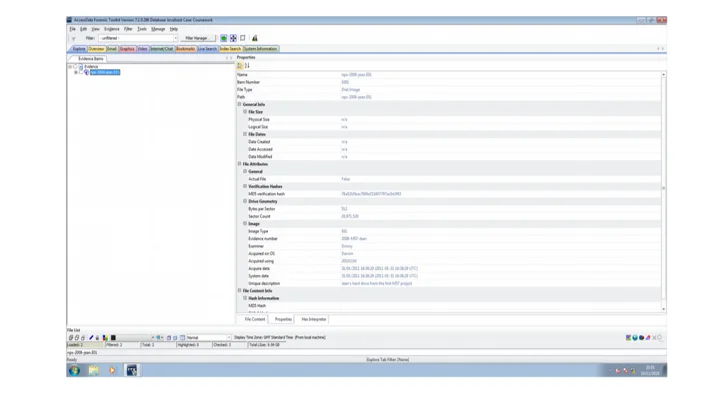
The first step is to validate Jean's hard drive's MD5 verification hash code.
the mirror image of a disc Second, validate Jean's computer's the hard disk, which comprises
Bytes per sector and the total number of sectors third, find out when Jean created the spreadsheet.
As well as how it got from her PC to the competitor's website finally, who else was there?
Involved in addition to Jean and Alison, as well as further computer misbehaviour
The toolkit that will be used throughout this inquiry is FTK7.1 in this case.
The table below shows a table containing suspicious email data from Jean to Alison. The table shows the details of the sender and the recipients and the Time the data was sent.
Computer Evidence analyse
The MD5 algorithm is a well-known hash function that produces a 128-bit hash output. Although MD5 was originally intended to be used as a cryptographic hash function, it has now been employed for a variety of different purposes. Numerous flaws have been determined to be vulnerable. Validation of data integrity is still feasible. Used as a checksum, but mostly to identify inadvertent fraud MD5, like other hash techniques, does not provide encryption or encoding. It is susceptible to hacking. assaulting by physical force and contains several flaws, as outlined in the section below Ronald Rivest designed MD5 in 1991 to replace an outdated MD4 hash algorithm. The RFC 1321 code that started it all grants an RSA license "by assignment." (Whytlaw, 2020) "However, MD5 was used by the Flame virus, and the CMU Software Engineering Institute MD5 has been cryptographically disabled and is hence inappropriate for future use" A drive picture might be changed or distorted because to faulty material, poor communication during image generation, or malicious manipulation (Kanta, Coisel, & Scanlon, 2020). This capability is only available for file types that save the hash within the disk image itself, such as EnCase (E01) and SMART (S01) " It is critical that it matches, or otherwise the evidence collected by this inquiry would be null and void, wasting a lot of time, effort, and money (Wallingford, Peshwa, & Kelly, 2019). The outcome, as seen in the figure above and the table below, demonstrates that both the computer hash and the MD5 verifications hash are the same, showing that we have a lot.
The geometry of the drive dictates how and where data is stored on each disc surface, as well as the drive's total storage capacity. The Disc Geometry property, comprising Bytes per sector and sector count, is illustrated in the figure above. When did Jean construct her spreadsheet, and how did it go from her PC to the competitor's website? The spreadsheet, as seen in the image above, has all of the sensitive information, including social security numbers, for all of the company's employees. If you look at the property, as shown in the image below, you will find that the data created and the data saved are identical, even the second, which is impossible. For example, if I build a decumbent and save it, it should be different in seconds; as a result, Alison created this piece of the document two months ago.
M57.biz property viewed
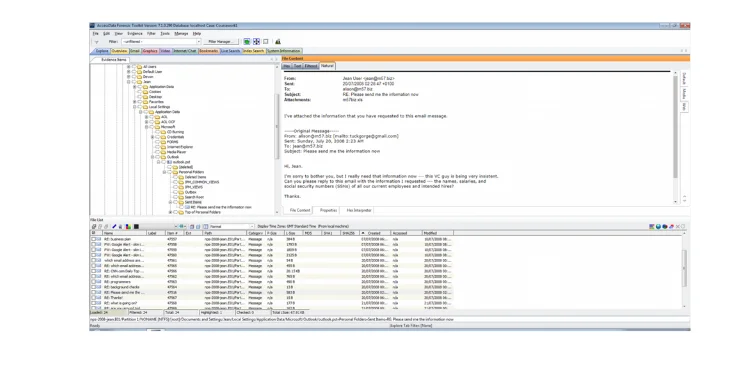
This case concerns communication that occurred on Jean's receiving and sending emails, resulting in sensitive information concerning workers' salaries and social security numbers being sent in the form of a spreadsheet to an external email (tuckgorge@gmail.com). As a result, I'll be concentrating on Jean's pertinent emails by keeping email records. Jean's email program is Microsoft Outlook Express, and her email address is jean@m57.biz. Jean's email address is "exclusive to the firm, used solely by its employees, and maintained in line with its business standards, which typically include tight security and permitted usage limitations." M57.biz is an internal email address. "The email server is normally part of the local network, and the administrator is in control of the server and its services,” are according to the instructions given from the server.
Microsoft Outlook emails are saved as post files, which may be exported to read outlook from Windows. Emails from Microsoft Outlook may be imported into Notepad by copying and pasting them. You may quickly examine the email headers, but I'll focus on the email headers that can be read by FTK 7.1. An internet email message header provides technical information about the message, such as who sent it, what software was used to produce it, and which email servers it passed through on its way to the recipient. Most of the time, the administrator only needs to look through internet headers to determine if there is a message.
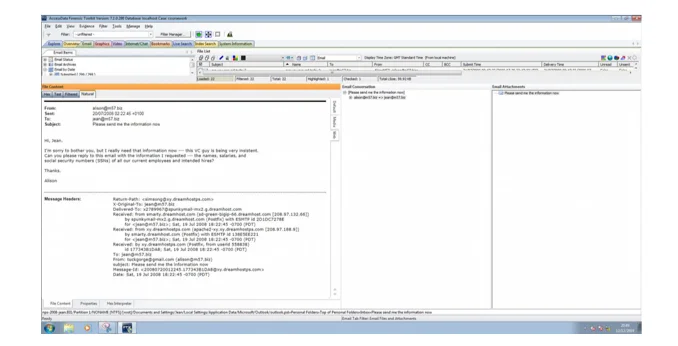
As demonstrated in the two photographs above, when Alison asked Jean to give the information that he requested, it was 20/07/2008 at 2:22, as indicated in the property screenshot. Also, the system information graphic reveals that on 20/07/2008 at 2:26 a USB flash was installed on the machine, which was 4 minutes after he sent the email to Jean. Furthermore, if you carefully examine the email's header, you will find Alison used an external email address, which is a faked email address. That means that the header email is not the organisations email address. It must have been that the system had been in cooperated with the email even before jean sent the email. As a result, it is evident that Alison is the guilty party, as he remotely controlled Jean's computer to perform the crime and Jean just did what Alison directed her to do. As the boss Jean had to follow orders without knowing that there was something fishy going on with Alison’s request.
Data examination
In order to ascertain some proof in this case data was examined using the dictionary attack using and the NTLM hash in both users’ accounts. Based on the results from the analysis will give a clear indication and supporting evidence of the issues that transpired that day. Tracing all the mails was very important because it could lead the investigations to the truth. After all, Jean was being blamed for the incident that happened and maybe she wasn't part of the scheme.
Analysis of the issue
The file was created and submitted in good faith by Jane, but Alison’s objective was to make it appear as though Jean is the organization's mole and that she is the one who supplied the organization's sensitive material to their competitors. She was the victim of a spear-phishing attack. Spear phishing is a targeted email attack that uses information that the email recipient already has. In this scenario, Jean was aware that they were working with investors, and it seemed normal that the new investors would want some salary information. Alison, the CEO's communications, appeared to arrive. If Jean had paid greater attention to the email header information she received, she could have seen that something was awry, especially when she responded. The SSNs are provided under the guise of conducting background checks on employees. The hacker was knowledgeable enough about the company to request information through email from Alison to Jean. I also assumed Alison was working on a finance round. No one else was engaged in the file transfer within M57. Alison and Jean both received news notifications on their work pages, and one of them may have been compromised in the process. Following Jane's transmission, the intruder posted the data on the competitor's technical support website that is after Jean had sent the document that was requested by Alison.
Facts that might lead to pieces of evidence of the act
Here is some information that may be useful in gathering further evidence:
The first step is to conduct a thorough audit of everyone who works for the organization, particularly the key personnel who are passionate about their profession. Second, each of them should be checked on their electronic communication as well as their laptop, as well as who they had in conduct for 6 months from the criminal data. Further investigation of both machines' internet histories is required to discover whether either had clicked on a compromised link in an email. Specific recommendations for their cyber security rules and phishing email training might be provided to the organization. There was a data loss somewhere along the route that led to the attack, and the following mismanagement of sensitive data resulted in the leak of salary and SSN information.
Legal issue
When dealing with digital evidence, legal authority, constitutional law, and evidence integrity were all taken into account. To have legal power, forensic investigators must obtain search warrants or consent to examine digital data. We acquired a warrant from the company to check Jean's computer in order to determine why she could have been hacked or if she was hacked by someone else.
Recommendation
Using the report as a reference from now, M57.biz should recommend holding standard cyber security training sessions and enlisting a cyber-security mentor to come in and talk about almost anything new that their staff should be aware of in terms of cyber security. The employees needs to be trained in order for them to safe guard themselves and the organization data against malicious attacks. They should also enlist experts who regularly screen their frameworks to avoid malicious from within or outside the organization's environment. Because the company is virtual, they may have a group conference call where a cyber-security master fair reminds every one of the importance of staying safe online, as well as what to be cautious of and what's going on in the news. This research would also suggest that the worker of the organization should perform all of their work at home on their private network and that if they chose to work at a coffee shop or a hotel, they utilize a personal hotspot while accessing the internet to eliminate any risk of a cyber-attack. It is also critical for the company to include in their policy that passwords for email accounts and file-sharing accounts be updated on a regular basis, such as quarterly, to assist prevent a hacker from breaking their accounts. Finally, users should install anti-virus/malware software that identifies phishing emails, viruses, and ransomware threats. They should also make some private information files from M57.biz encrypted so that even if a private file is supplied to a hacker, the hacker cannot just post it without first determining how to decode the file. We believe that by taking these precautions, M57.biz will be able to develop a stronger security plan and avoid such assaults in the near future.

Conclusion
From our analysis, it is evident that Jean was not guilty in this incident that happened and that Alison could have been the guilty one. At some point, we thought that this could be Alison's doing and maybe he ought to have worked with some external hackers in order to get information from the company to their competitors. However, on handling the matter carefully, it must have been that Alison's system was the one that got hacked, maybe when he clicked on some link that could have been from the phishing email that was sent by Jean. This appears to be legit dependent on their meeting reactions, as Jean had received an email from Alison's programmer behaving like her, training her to produce this dominate sheet and communicate it to them. Jean didn't research the email's return way and, thus, produced and sent this record. This would likewise clarify why Alison felt she never requested this data and never requested that Jean produce an email dominate sheet since she was hacked and didn't understand the programmer was sending messages to Jean behaving like her. Finally, neither Jean nor Alison submitted this confidential information to the firm's rival, but Alison was the one who was hacked and he is the one that should be investigated.
Reference
Kanta, A., Coisel, I., & Scanlon, M. (2020). A survey exploring open source Intelligence for smarter password cracking. Forensic Science International: Digital Investigation, 35, 301075.
Wallingford, J., Peshwa, M., & Kelly, D. (2019). Towards understanding the value of ethical hacking. In International Conference on Cyber Warfare and Security (pp. 639-XIV). Academic Conferences International Limited.
Whytlaw, R. (2020). Cyber Forensics Training for Judges Ryan Whytlaw, Christie Nelson, and Dennis Egan CCICADA Center, Rutgers University June 29, 2020.
Continue your exploration of Capabilities and Development of Alexa Skills with our related content.
- 24/7 Customer Support
- 100% Customer Satisfaction
- No Privacy Violation
- Quick Services
- Subject Experts



