Impact of Cyber Breaches on Oil Industry
CHAPTER 1: INTRODUCTION
1.1 Background
The origin of cyber breaches is demonstrated by research, which indicates that the attacks gained much attention as business operations increasingly started relying on cloud computing, workforce mobility, and digital data (De Groot, 2019). Sensitive business information started being stored on machines on cloud servers and enterprise databases, allowing hackers to access restricted networks (De Groot, 2019). Saudi Arabia’s energy sector involves the production of natural gas, petroleum, exports, and consumption, as well as electricity production. This Kingdom is the globe’s largest producer and exporter of oil. Its economy is mainly petroleum-based, with oil making up 90% of its exports and about 75% of the nation’s revenue. This sector alone produces 45% of its Gross Domestic Product. Therefore, the Kingdom’s economy largely depends on oil (Matar et al., 2017). Research has demonstrated that there are vulnerabilities linked to cybersecurity in companies and organisations including the gas and oil industry (Cyber Security, 2018). Following WannaCry, NotPetya, and Mirai cyberattacks, which caused significant damage across numerous industries in the past, there has been a need to safeguard the gas and oil sector. That is especially because such attacks in this industry might result in plant shutdown, undetected spills, a violation of safety measures and equipment damage which may cause injury and death. After some high-profile cyber-attacks such as the Saudi Aramco (2012) attack that unleashed a computer virus, which affected more about 30,000 workstations, gas and oil firms have developed prevention procedures and unique protocols. In 2012 August 15, during the Aramco attack, a staff member who had privileged access in the organisation opened an email from the spam box and, in the process, let a scam email into the company’s computer system. The investigation into the cyber-attack led them to conclude that the act was intended to sabotage the company because the release of the computer virus, which infected their computers, was planned and intentional (Cyber Security, 2018). The virus, self-replicating, infected more than 35,000 machines, which are Windows-based linked to the gas and oil company (Bronk and Tikk-Ringas, 2013). Practically, all the organisation’s systems that were computer-based were infected and destroyed in several hours. This virus, which causes substantial disruption to the world’s largest producer of oil, was determined to be Shamoon. The virus intended to create a total or indiscriminate deletion of information and data from the hard drives of the company’s computers. Although this attack did not produce oil explosions, oil spills, and other significant disruptions of the company’s operation, it affected different business processes, causing a loss of significant production and drilling data. The attack also affected their online payment system rendering the company unable to supply the world its usual 10%. The company had to rely on the use of faxes and typewriters to keep its essential functions running. After about five months, the organisation brought its system back in operation, but the hackers have never been found. The attack led to some crucial findings concerning cybersecurity. First, it was revealed that low awareness about cybersecurity among staff members can lead to such attacks, which can be catastrophic to the operation of companies. Additionally, among other essential highlights, it was revealed that the collapse of computerised system is much faster as compared to the necessary action and only takes some minutes for the network or system to be entirely infected (Bronk and Tikk-Ringas, 2013). Unfortunately, other attacks in different organisations demonstrate that the lessons from the Aramco attack were not given serious consideration. For instance, in 2014, about 50 Norwegian energy and oil organisations were also hacked by anonymous attackers, as stated by the security authority of the government of Norway (Leyden, 2014). The same Shamoon virus which attacked Aramco also infected a company in Qatar known as RasGas, some weeks after the Saudi Aramco incident. Even though the RasGas attack was not as intense as that of Aramco, the Qatar Company showed much pro-activeness by creating a government organisation to deter more potential attacks by not only detecting but also analysing, as well as, monitoring possible threats to cybersecurity. As a result, Qatar became a model country concerning obtaining and developing a national agreement on the best strategy of cybersecurity, which can be used to protect organisations from cybercrime (Onyeji, Bazilian and Bronk, 2014).
Although incidences of cybersecurity are few or rare, many of the attacks are not detected and go unreported as numerous companies do not realise that their systems have been attacked (Wilson, 2013). Research shows that the first area to be attacked is usually the offices of many companies including in the gas and oil sector, working through to the process and production control and the safety systems (Dancy and Dancy, 2016). Research by Daugherty (2013) highlights how the landscape of cyber threat is always expanding and evolving and, as such, needs businesses to act promptly in taking the necessary preventive measures. These individuals say that it is not just the emerging and new threats which individuals and organisations should know, but they should also understand that some of the conventional methods of mitigation also present significant risks and that no organisation is immune to or shielded from data breaches. Interviews (2019) indicates that awareness of cybersecurity provides organisations with an ample opportunity to re-evaluate their practices about safety to find their external and internal weak points. The author asserts that awareness on cybersecurity is the best chance for companies to create more awareness linked to the risks which expose them to attacks. Through this awareness, the organisations will be able to protect themselves from attacks because all employees will understand the landscape of the threats faced by their firms and the sophisticated nature of the hackers. Awareness will help everyone to recognise vulnerabilities in the companies’ IT infrastructure and determine high value data and assets. They will thus be able to develop appropriate protective measures and policies which can be implemented to mitigate potential attacks. According to Unwala (2017), information sharing and strong partnerships are some essential elements considered by the cybersecurity authority of Saudi Arabia. According to this author, the cybersecurity authority of Saudi Arabia is an important step towards meeting the goals of the Kingdom’s Vision 2030. However, Unwala (2017) claims that it will be difficult for the nation to reach this goal without a better sharing of information, private-public partnerships, and legal frameworks concerning data privacy and security. According to Unwala (2017), the authority targets building a good relationship and corporation with the private industry, similar to the Cyber Strategy adopted by Dubai in 2017, a plan which depends on collaboration between the private, the public and international stakeholders to develop robust cybersecurity standards and laws which are implementable universally. However, Unwala (2017) says that there are some obstacles to achieving this collaboration. For instance, for the nation and many other neighbouring states, sharing information might expose the oil companies to internal cyber vulnerabilities and breaches as this might signal the companies’ weakness to attackers. Therefore, awareness of cybersecurity is also limited.
1.2 Problem Statement
Even though Saudi Arabia is among the most technologically advanced countries in the MENA region, it is, daily, faced with the most cases of cyber-attacks, especially in critical government and private sectors like the energy sector. That is highly likely to cripple the economy if the attackers achieve their goal. Furthermore, even with advanced firewalls, and other technological steps taken against hackers, cases like WannaCry, NotPetya, and Mirai have been witnessed before. Given the continued cyber-attack threats, as has been observed in 2019 and early 2020, technological barriers are certainly not enough and, thus, there is the need to address the human factors. Given these circumstances, as explained here, this dissertation investigates the people factors to cyber breaches, particularly in the energy sector.
1.2.1 Purpose
This investigation is focussed on determining the people factors to cyber breaches in the energy sector in Saudi Arabia. It intends to find out how the business risks of cyber breaches can be mitigated due to inadequate corporate cyber awareness programmes in Saudi Arabia’s Energy Sector. This research will help the Kingdom to better plan their training and cyber awareness programs to prevent future cyber-breaches in this sector.
1.2.2 Decision Problems
The Saudi Arabia Government needs to come up with enforceable policies on cyber awareness and training of all employees in the energy sector to reduce the risks of cyber-attacks on its companies.
1.3 Aim of the Study
This dissertation aims to find out the state of cybersecurity in the oil and gas sector in Saudi Arabia.
Objectives of the Study
The objectives of this study are to:
To critically determine the people factors to cyber breaches in this sector
To critically evaluate how business risks to cyber breaches can be mitigated
To appraise how training and awareness can be used to reduce cyber breaches in this sector
1.5 Research Question
Does the inadequacy of corporate cyber awareness programs in Saudi Arabia's energy sector hamper the mitigation of the business risks of cyber breaches?
Can training and awareness be used to reduce cyber breaches in the energy sector in Saudi Arabia?
1.6 Research Approach/Philosophy and Method
The research approach or philosophy to be followed is one that can be described as ‘epistemology’ or one that answers the questions, ‘what is’ and or ‘what should be.’ The stance to be followed will be one referred to as interpretivism, where the researcher plays a critical role in making sense of the gathered information through a qualitative study.
1.6.1 Research Methodology
1.6.1.1 Secondary Research
Internal secondary research will be conducted, including the annual reports by the energy companies in Saudi Arabia on the state of cybersecurity in the firms. External secondary research will include trade journals, internet documents, and industry journals about cybersecurity in the energy industries.
1.6.1.2 Primary Research
Using questionnaires, primary data will be collected, and will later on be analysed later through statistical data analysis. This approach will help obtain real opinions from people on the subject matter in actual situations.
1.7 Significance of the Research
This research will be important for industries in the energy sector, particularly those planning to improve their cybersecurity. This research will be informative to these organisations, who are at increased risk of attacks by competitors or cyber criminals. It will also be important for Information Technology experts who will understand that besides installing machines and software to protect their organisations from cybersecurity breaches, there is a need to focus on the human factors in the company. It will inform both the leaders in the energy-producing companies and the information technology professionals the importance of cyber-security awareness and how training on cybersecurity can help protect them from breaches. This research will also shed some more light on this inadequately researched field of business risk imposed due to inadequate corporate cyber awareness programmes within energy. It will act as an important stepping stone for further research in this area, where scholars and future researchers can get some critical information that will allow them to successfully conduct their studies on awareness concerning cybersecurity and how the lack of this can result in corporate cybersecurity breaches. This study is essential to organisations or companies operating in the energy sector around the world. It is also important for all the other firms whose data or information breaches can result in severe financial losses or harm to various stakeholders. This research will also be critical for the information and technology professionals, as they will understand how to avoid cyber-attacks further.
1.8 Overview of the Dissertation Structure
The dissertation is divided into six chapters, as follows:
Chapter 1: This is the introductory chapter, which will provide the background to the study, aims, and objectives as well as the research questions. Furthermore, the research problem, significance, and methodological overview will be given in this chapter as well.
Chapter 2: This is the literature review section, which will provide a critical analysis of previous studies on the topic and provide the gaps to be filled through conducting this study. The second chapter will be focused on those studies that are linked to this study’s specific objectives, and not only in the context of Saudi Arabia, but also global.
Chapter 3: This is the research methods chapter that will provide a step by step process of how data was collected and analysed to come up with the research findings and conclusions, respectively. This chapter will also provide a detailed discussion of the research philosophy and approach taken to fulfil the goal of conducting this research.
Chapter 4: This section will present the results of the study in a manner that is described in the third chapter. Consequently, the results will be interpreted but not discussed in this chapter.
Chapter 5: This chapter is the analysis of results and will also discuss those results and link to the literature review and the research objectives to ensure that the research objectives are achieved and questions answered extensively.
Chapter 6: This is the conclusion and recommendations chapter, which is a summary of the whole dissertation, on what was found, and further provide recommendations as regards how people factors can be effectively manipulated to significantly reduce cyber breaches in the Saudi Arabia’s energy sector.

CHAPTER TWO: LITERATURE REVIEW
2.1 Introduction
This chapter provides a review of different literary materials written by different authors in the past.
2.2 The need for Cyber Security in Organisations
Cybersecurity (or computer or information technology security) is a broad body of technologies, practices, and processes implemented with the aim of safeguarding devices, networks, data, servers, and programs from theft, damage, attack or access by unauthorised persons (Abomhara, 2015; Jang-Jaccard & Nepal, 2015; Von Solms & Van Niekerk, 2013). The oil and gas sector has, over the years, become a high-value target for adversaries (ranging from military to cyber attackers) bent on disrupting its production, accessing confidential and sensitive data, and crippling a nation’s and the world’s economy. Several previous cyber-attacks targeted at the oil and gas sector have made stakeholders and organizations value the importance of risk management and having an effective cybersecurity policy. Previously the sector used isolated and proprietary networks to manage its processes, equipment, and control systems (Singer and Friedman, 2014). In most cases, the automation and control systems were distinct and separate from the information and network systems, but this has now changed (Rao, Chakravarthi, and Jawahar, 2017). The development of technology, as well as the need to remotely operate and maintain equipment, transfer production data to the information systems, and for efficiency, it became unviable and practically impossible to keep all these processes and systems separated, thus the need for integration (Black, 2018). The increased automation within the industry was also necessitated by the need to manage costs, attain the highest value from the organizations’ current assets and to increase output as well as up-time. However, despite digitization having numerous benefits, it could also have its ill-effects that might increase the organizations’ risk to cyber-attacks. Digitization has often resulted in the use of open and shared networks, which have limited bandwidth, whose vulnerabilities expose the sector’s equipment. The operations of the oil and gas companies in locations that are far-flung and in which they may have little choice of networks, forcing them to make do with what is available may lead to them leaving their communications unencrypted (Liu at al., 2012). Unencrypted information, when processed through and stored in unstable cloud sources, raises security and privacy issues (Domingo-Ferre, Ricci, and Domingo-Enrich, 2018). Since most of the sector’s activities, systems, and processes are digitized and automated (Black, 2018) and therefore dependent on modern technologies, which are commercially available rather than proprietary, hackers could exploit the known vulnerabilities and inadequacy of such commercial systems and technologies. Organizations, therefore, need to protect their intellectual property adequately since the loss of such property, due to a cyber breach, will affect the organizations’ revenues and finances, endanger lives and damage the environment. According to Macaulay and Singer (2012), industry control systems, or ICS in cyber-security is a growing trend in both global and national security. That means that factories, industries, firms, and organisations have to acclaim these technologies in securing their internet-of-things and other systems that rely on information technology infrastructure. Ernst & Young (2007) say that risk to a company’s Operational Technologies (OT) poses a threat to the firm’s business and affects its financial wellbeing, its environment, regulatory and contractual requirements, and reputation. If these systems and automated or mechanical processes are compromised, they could disrupt the normal operations and processes of the organization resulting in serious downtime or even forcing the plants and production to be shut down, both of which occasion massive loss in revenue (Liu et al., 2012). The oil and gas sector systems, when compromised, could also result in; environmental effects due to ruptures, fires, explosions, and spills, the damage of equipment and oil spills and gas leaks going undetected which could bring about serious (even fatal) accidents, utilities being interrupted, products of poor or inappropriate quality being produced and various (unintentional) violations of safety measures.
The oil and gas sector relies on various digital communication systems and methods to enable it to produce and distribute energy. The sector’s adoption of digital systems and dependence on electrification or power from the shores make it susceptible and also expose it to various digital vulnerabilities within these power systems (Yan et al., 2012). Electricity is a necessary, critical, and complex infrastructure that is depended on by many other sectors; it is estimated that the oil and gas sector alone produced over 35 percent of the Kingdom of Saudi Arabia’s electricity as of the year 2018 (Yan et al., 2012). A more considerable bulk of man’s existence and living is dependent on the energy that the oil and gas sector generates. Therefore, the industry should thus ensure that they develop a resilient and secure electric grid (Wang and Lu, 2013) that cannot be attacked by cybercriminals. That is because even the slightest cyber-attack could significantly disrupt oil and gas generation and pose other serious cyber risks. According to Stouffer (2015), the various organisational or industry platforms are exposed to cyber-attacks, vulnerabilities, and threats. In support of this argument, Amin and Sastry (2015) say that basic functions of systems in the organisations, like hardware control, sensor measurements, maintenance utilities, and remote diagnostics have to be secured from any kind of interferences. Understanding the value of a comprehensive layered information security approach, oil and gas organizations are now going for superior and well-integrated Industrial Internet of Things (IIoT) to safeguard their systems (Baudoin, 2016). Young (2012) posits that cybersecurity breaches, besides causing information loss financial assets loss, tainted reputation, and disruption of operations, also poses imminent safety threats to employees due to possible failure of mechanical and operational systems. Companies should, therefore, approach issues of cybersecurity as a matter of human and company assets safety priority, and should design, install, operate and maintain systems that are resilient to and able to survive a cyber-attack, while being able to sustain its critical operations ( Ten, Manimaran and Liu, 2010; Badie and Lashkari, 2012). As seen above, a cyber attack on the systems of an oil and gas organization’s control systems could bring about severe consequences to the company, its employees, and the environment. As such, it is imperative that organizations fully implement strict and effective cybersecurity measures. However, this has not always been the case for the longest time. Aldawood & Skinner (2019) argue that the implementation of cybersecurity awareness programs is more of a marathon and not a sprint. It is required that awareness programs and campaigns are designed in such a way that they are continuous so that they can be able to drive messages home and further reach more employees (Beautement et al. 2016). Significant resources- money and time- are required for the creation of programs, the setting of goals, and even the execution of training sessions and the subsequent progress measurement. That points out to the need for organisations to pull adequate financial resources before embarking on cyber awareness programmes.
El-Haddadeh, Tsohou & Karyda (2012) point out that the introduction of cyber awareness programs in no way guarantees behaviour changes, and even when changes in behaviour happen, there is never a guarantee that the changes are positive. Thus, ongoing education is required when real change is sought together with hands-on-training and the setting of measurable objectives.
2.3 Cyber Breaches in the Energy Sector in Saudi Arabia and Business Risk
The sector’s industrial control systems, the fact that the sector has a number of critical vulnerablilities that have not been (adequately) protected, the failure to implement effective cybersecurity measures and the potential “benefits” hackers could potentially reap have made the sector a valuable target and led to it being exposed to an increasing number of cyber criminals and attackers seeking to take advantage of these factors. Digital risks and vulnerabilities are increasingly threatening the sector (Al Neami & Lutaaya, 2015; Alpi, 2017). The results of a previous survey study showed that 87% of senior oil and gas sector executives reported their organizations as having experienced or been affected by cyber-attacks or incidents within the last year. In comparison, 82% of the oil and gas respondents surveyed said that the number of successful cyber-attacks targeted at their organizations had significantly increased in the recent past (Alelyani and Kumar, 2018). In comparison, 53% reported an increase of 50-100% in the monthly cyber-attack attempts, of which the 46% that occurred on operational technologies (OTs) went undetected or were detected late (Dimensional Research, 2015). With the oil and gas sector the most vulnerable, cybersecurity intelligence shows and warns that these threats, both intentional and unintentional, are bound to even increase further as a result of the increasingly sophisticated and innovative techniques employed by malicious attackers. Several very significant cybersecurity issues have been experienced within the oil and gas sector in Saudi Arabia. The Aramco network attack occurred in 2012 on August 15th, damaging more than 30,000 computer hard drives belonging to the company, preventing them from conducting their normal operations (Bronk & Tikk-Ringas, 2013). Andrew (2014) says that the organisation found no evidence concerning the attempts that the hackers made to steal substantial information. Besides, no other devices in the network were disrupted, and the production of oil or was not affected. This researcher says that only one group of anonymous hackers claimed responsibility for the attack, providing some political explanations. In response to this attack, the organisation disengaged its company system from the internet. The organisation also shut down some of the internet servers, and even though the cyber-attack caused significant destruction to the company, the attackers failed to reach their objective of stopping energy production in the company. According to Holden (2012), although the cyber breach on this company, which supplies about a tenth of the global oil requirements, failed to interfere with the process of production, it significantly affected the firm’s business. The attack, which used employed a computer virus called Shamoon made the organisation to stop critical internal networks for about a month. Rid (2013) says that the Kingdom of Saudi Arabia is mostly reliant on oil production, and the export of fossil fuel adds to about 90% of the Kingdom’s total revenue and over 40% of its gross domestic product. The spread of the virus into the company’s computer system wiped out a lot of information that affected its technical operations leading to significant financial losses.
Bronk and Ringas (2013) say that Saudi Aramco let out some private data concerning the cyber-attack and details concerning the specific virus used in the attack. This researcher says that most security organisations reviewed a different virus also discovered during the period of the cyber breach in this company, a virus with equal capabilities to Shamoon. The security review highlighted more details concerning the particular virus used in the attack and realised that it could get control of one computer and find its way through the entire internal network of an organisation. The virus also could launch and control as well as command the whole centre. These researchers claim that that the organisation found difficulty in determining whether or not the hackers gained control of the firm’s computer. They say that this can usually be achieved with the help of an insider who can be used to initiate an attack quickly. Bronk and Ringas (2013) claim that the attack vectors in the Aramco cyber breach demonstrated higher success rates, and the hackers had significant control of a specific global computer, which they used to spread the virus from one command and control computer. The attackers were also able to take advantage of some administrative shares to over 30,000 Aramco desktops. The hackers triggered the virus to infect as many computers drives as possible within a short time. According to Kumar (2012), the main aim of the attack was not to steal information but to destroy the system. Kumar (2012) says that such destructive attacks do not usually happen frequently. According to Kumar (2012), network services have been used for a long time by politically motivated hackers. This author says that such attacks are usually in copycat attack forms that target organisations with new internal systems used to destroy or disrupt data. He adds that organisations must consider such kinds of cyber breaches and come up with quality management plans to mitigate these risks. This type of breach is often referred to as advanced persistent threat or APT, and starts at workstations where passwords are used to access the machines to gain further administrative power. APTs have been used to access high-level administration accounts and domains. This author says that it is crucial to identify that the Aramco hackers used this approach to access their system. However, as Bronk and Ringas (2013) state, the practical and greater control of the system by the company prevented the hackers from getting greater access. Rid (2013) says that the speed of response in such a situation is important, and organisations should initiate fixing the problem quickly. This researcher says that organisations need well-tested response approaches that can help save the restoration cost and which can help the organisation to resume its functions faster on relevant machine networks after the infection incident.
According to Andrew (2014), the exploration and production processes of oil during the Aramco attack were not affected because they worked in isolation, and it assured its stakeholders, partners, and customers that its system will function reliably again. Eventually, it was realised that the virus came from an outside source and that there was a possibility of future attacks. This researcher highlighted that the energy infrastructure in Saudi Arabia is still under the threat of cyber-attacks and that this can significantly disrupt energy supplies. Rid (2013) says that the vulnerability of the energy sector in the Gulf Region has been increasing from cyber-attacks. This researcher says that there has been growing tensions between Saudi Arabia and its rivals who have occasionally unleashed cyber-attacks against its energy infrastructure. This has affected the global energy market, seen through supply disruptions and increased price volatility in the oil and gas market. Rid (2013) and Bronk and Ringas (2013) say that the threat of cyber-attacks on Saudi Arabia’s energy sector has mostly been from Iran. These researchers claim that Iran has both the motive and capability to carry out such attacks even though no evidence has been found linking this country to the Aramco cybersecurity breach. According to Bronk and Ringas (2013), Saudi Arabia had been concerned concerning possible cybersecurity breaches even before Aramco was attacked. As a result, the Kingdom made plans to double its domestic expenditure on cybersecurity. The nation has paid more attention to securing its energy sector from possible cybercrime. The number of people using the internet in the United Arab Emirates has tremendously gone up with time (Martin, Martins and Naqvi, 2018). They add that the continued growth of users have attracted numerous online forms to conduct business activities in these regions with many firms moving many of their functions online (Alzahrani and Alomar, 2016), something that cybercriminals have tried to exploit. The UAE experienced the largest penetration of e-commerce with Saudi Arabia seeing a 10.7% penetration rate and the use of credit cards also increased in Saudi Arabia and the Middle East in general (Alshahrani, 2016). These researchers say that this increased internet users for business activities and financial transactions fuelled the growth of internet technology in this part of the world. The period between 2006 and 2008 saw increased online transactions, application of smart mobiles and electronic data, and this growth in the use of internet technology in business activities was also accompanied by high incidences of cybercrime (Alzahrani and Alomar, 2016).
According to Standard et al. (2013), cybercrime in the Middle East have increasingly and often targeted the United Arab Emirates energy sector and the residents, where besides the use of specific viruses like Shamoon, the hackers also applied phishing scams to harm oil and gas producing companies and other organisations like banks. Saudi Arabia put in place Cybercrime laws that impose imprisonment and a fine for people who steal information or commit cybercrime offense. Nonetheless, many cyber-attacks have continued undetected (Rowe and Goh, 2007).
2.4 People Factors which may lead to Cyber Breaches in the Saudi’s Energy Sector
Cyber criminals, who are becoming bolder, more sophisticated and stealthy in their techniques, have identified employees as the possibly weakest link (Huang, Rau and Salvendy, 2007), and whom they use (albeit without the victim employees’ knowledge) to access the organizations’ systems. Organizations should therefore train and enlighten their employees on how to conduct their activities without compromising the information systems and networks, failure to which they will engage in ways and activities that would expose them and the organizations to cyber-attacks. For example, an employee may open an email attachment, charge a phone, insert hard drives or connect their phones and laptops to critical system networks, or be tricked into revealing passwords: all these actions may provide a cybercriminal with the opportunity to gain access to the systems and effectively spread malicious software and codes which result into tremendous consequences (Ferguson, 2005). Organizations should therefore not only pay attention to the technical dimensions of cybersecurity systems, but also how employees interact with their OT systems, since a majority of breaches in information systems are brought about by various human factors or errors, some of which Huang, Rau and Salvendy (2007) have identified: breaches can occur due to human omission where employees forget to perform an important activity such as changing the system’s password regularly; an act of commission where people do things incorrectly like writing a password down where someone else can find and use it to access the system; extraneous acts including doing unnecessary things; or sequential errors whereby an employee can do something in the wrong manner or without following the right procedure (Evans et al. 2016). Mirashe and Kalyankar (2010) and Knowles et al. (2015) who say that cyber incidents and attacks against the control mechanisms of industries have increased and that they have also been accompanied by a change in terms of targeted vectors of breaches. Although many firms have now invested heavily on cybersecurity technology, the hackers have also side-tracked with their attacks focusing more on people or the human assets rather than on technology (Ben-Asher and Gonzalez, 2015), because users often interact with the installed technology to start and implement or control organisational or industrial processes. According to Hershberger (2014), the human aspect of organisations can be exploited easily thus making them the weakest link in the interaction loop within the system. He says, for example, that an assessment of the data breach which occurred in 2013, that affected Target Corporation, demonstrated that the organisation’s technology for cybersecurity had the capacity to protect the firm from attacks by detecting possible breaches, although the employees and leaders, who were supposed to take relevant measures to control the breach, lacked the critical knowledge and skills. As a result, Target lost over 148 million USD. Other financial firms also lost nearly 200 million USD. Hershberger (2014) says that had the firm been proactive in evaluating its capabilities concerning cybersecurity, particularly of its labour force, and had it known the potential risks earlier enough, it would have improved its cybersecurity abilities by empowering its employees through awareness, organisational preservation, self-protection, incident response and a conscious and cultured attitude. The absence of employees’ skills and knowledge on cybersecurity should be considered a high risk human factor and probable contributor to a successful cyber-attack or system breach (Adams and Makramalla, 2015). A survey by IRM (2015) show that about 20% of the worst security breaches that took place in 2015 occurred because of inappropriate or decisive misuse of assets or infrastructure in organisations while 31% happened thanks to human error.
2.5 Mitigating CyberSecurity Threats
Employee and corporate awareness remains an important aspect in cybersecurity, given that human error or lack of awareness and training has been associated with a majority of cybersecurity incidents within the sector. Increasing digitization have made the cybersecurity landscape broader and more complex, which worried organizations, although most of the attacks experienced could be as a result of employee unawareness (McCrohan, Engel and Harvey, 2010). Previous study findings show that most organizations (78%) attributed the most probable cause of a cyber-attack to a careless employee, and lack of end-user or employee awareness- which was exploited by cybercriminals through phishing- accounted for nearly 43% of global significant cyber breaches. Cloudmark (2016) highlights that stolen information or credentials by phishing makes up 80% of all cyber-attacks and that this method has topped the security concerns for many businesses and organisations, leading to about 1.6 billion USD lost through the breaches, resulting in loss of nearly 43% of productivity in employees, and 32% financial losses, 29% reputation damage on the organisations, 27% brand reputation damage and 25% stolen intellectual property. Employees must therefore be adequately informed about the numerous cybersecurity risks that exist and be trained on what to do and how to minimize such risks or vulnerabilities. Companies should also replace old information equipment and systems, separate (where possible) networks, and adopt robust cybersecurity systems and technical solutions that promote the safety continuity and reliability of operations while also preventing leakage, thereby protecting the data within the industrial control systems and maintaining network confidentiality. However, the oil and gas sector is still grappling with cybersecurity threats despite various measures they have already adopted due to a wider lack of awareness, skills or knowledge, and the organizations’ failure to train them on how to protect and defend the systems from cyber-attacks (Ashford, 2016). A system is only as good as the employees operating it since no matter how good the organization’s information security system is, it may prove porous or penetrable if the employees are not well trained or have no clue what to do in certain situations that may arise. Therefore, organizations should ensure that they sufficiently train and prepare their cybersecurity teams to enable them better address and tackle possible cybersecurity threats so as to sufficiently defend and protect their organizational systems and infrastructure. This way the organizations will be managing and minimizing cybersecurity risks while also reducing the attack surface. The value of a firm’s main security asset rely on its human constituents more than on the regulations, laws, and technologies, because the human aspect is often the weakest link used by hackers (Navarro, 2007). This argument is supported by the PA Consulting Group (2015) which says that for a cyber-security venture to succeed, the organisation, business or industry must invest and depend on its human elements as they are the important resource which also creates a major risk to its cybersecurity. This is also the argument by Russell (2007) who claim that an organisation’s or system’s weakness lies on its weakest spot or link. According to Robert (2015), the weaknesses are featured by the personnel who are in charge of controlling the system, the corporate users, the experts, technicians and operators; and these individuals are often unfamiliar with the concepts of digital security and are usually not very keen concerning the significance of the practices and trends of cybersecurity but understand the trends of operational performance. Lack of awareness or skills and education in cybersecurity has eased the manner in which cyber criminals perpetrate their crimes (Srinivas and Umar, 2013). Training and creating awareness among the cyber teams and other employees will prepare and provide them with the right skills that will enable them effectively detect, prevent and defend against cyber-attacks. Organizations should also regularly refresh and update their employees’ knowledge and training, as the cybersecurity landscape is constantly evolving, to include new methods and techniques that could effectively address the latest and emerging cybersecurity threats within the oil and gas sector. Through trainings, the organizations will also be fostering their employees’ collaboration and communication skills, and these- coupled with the targeted cybersecurity knowledge they will also acquire- will significantly help them in attaining their cybersecurity objectives. Srinivas & Umar (2013) suggest that user training and education is vital in fighting against security threats to cyber information. While creation of awareness among employees, training them and establishing clear organizational cybersecurity policy is cumbersome and takes a great effort to achieve (Geers, 2011), their potential results and benefits should drive the organization to achieve them.
Research by McIlwraith (2006) shows that awareness concerning cyber-security, particularly in the energy sector in Saudi Arabia is at its lowest or even lacking in some instances, and that the country has not paid more attention to creating awareness concerning OT systems. Additionally, he says that the nation’s energy industry has put in little effort in creating awareness about Data Acquisition and Supervisory Control and Distribution control systems and that many firms view installing OT systems as a cost instead of a worthy investment. Operational Technology (OT) and information technology security is an emerging trend in the energy sector, which is affected by the lack of awareness and proper implementation (Ernst and Young, 2007). They further say that many companies in the sector lack awareness and have little or no interest in this area which exposes the firms to great risks of cyber-attack. According to Siponen and Vance (2010), only some Middle Eastern states have created laws on cyber-security awareness, with the United Arab Emirates being the first to introduce a law illegalising cybercrime in 2006 January. For instance, those found culpable of cybercrime would be fined about 100,000 Dirhams in the UAE and or not less than 15 years of prison time. Saudi Arabia followed suit when it introduced a federal law against cybercrime in 2006 October. In this study, it is noted that these laws helped low the cases of cyber-security breaches but failed to completely wipe them out in this region. The authors say that the reason behind the continued cyber-attacks in this Middle-East region was because of the lack of sufficient enforcement of the laws, and the lack of enough knowledge or awareness concerning cybercrime and how to prevent attacks. According to Xiang, Wong and Liao (2008), firms should start awareness programs in order to reduce cyber-attacks, detect potential attacks and prevent the possibility of becoming victims. Yang and Shieh (1999) say that most of the campaigns involved different communication formats like posters, in-class training, emails, games and seminars. Chan and Cheng (2001) found that while these campaigns can help firms meet the requirements of compliance and security standards set by the government and the organisations themselves, these programs’ effectiveness regarding their ability to protect the organisations from attacks are questionable. For instance, offering educational campaigns is still limited in ability to reduce attacks because only the individuals who underwent the training can be safe while those who have not gone through the program are at risk. These researchers also say that many of the awareness programs do not identify the effect of their sessions or the usefulness of the programs in protecting people or organisations from attacks, that is, whether or not the programs are helpful. Many organisations have continued to expand their application of sophisticated secure technologies to protect their businesses from hackers (Spears and Barki, 2010), and attackers are also working on breaking into the firms through the weakest links, mainly associated with uneducated user of the computer or those who have not been made aware about the risks of cyber-attacks. Therefore, according to McFadzean, Ezingeard and Birchall (2007), mistakes by the computer user pose the biggest threats to the organisation’s cybersecurity and so it is important that awareness concerning cybersecurity is created among users. They further claim that creating awareness about cyber-security is important to both the individual and the organisation because through such programs, people are trained on how they can protect wireless, linked systems with numerous access points which can be breached without detection, adding that those who have undergone awareness training programs can also know the weak links in the firm and how to enhance their protection.
Training employees and making them aware places the power of cybersecurity in their hands and will consequently improve their and the organization’s ability to effectively detect, prevent and stop cyber-attacks, breaches and anomalous cyber behaviours that could have tremendous negative impacts. Detecting and preventing such attacks in time will in turn enable the organizations lessen the impacts and lower the overall business risks that the organization could have otherwise suffered. The review of literature has highlighted the various factors that facilitate cyber attackers’ intrusion into organizations’ systems as well as the business risks these intrusions cause and how organizations can use training and creation awareness to mitigate these risks. However, most organizations have yet to appreciate the significance of investing in the development of an effective cybersecurity policy and training of their employees on cybersecurity, but instead view these areas as costs they would rather avoid, and this has in most cases worked against them. Therefore, to effectively mitigate against cybersecurity threats, oil and gas sector organizations in Saudi Arabia should not only concentrate on installing and using superior systems, but also focus on training and creating awareness among employees on the various human factors and errors likely to facilitate system intrusions and enhancing their ability to effectively safeguard the systems as well as handle any potential or attempted system intrusions. Training employees and creating awareness, if done accurately and decisively, will see to a significant reduction in the number of successful cyber-attacks experienced by these organizations.
CHAPTER THREE: RESEARCH METHODOLOGY
3.1 Introduction
Depending on the type of study, its depth, the objectives or aims that the study seeks to achieve and to ensure its effectiveness, researchers are compelled to adopt and implement the most appropriate research methods and techniques that are best suited to the study and that will promote the realization of the study’s general purpose. The research procedures chosen will also be influenced by the available time and the environment in which the study is conductet (Quigley and Notarantonio, 2015). As such, a researcher should understand the different research methods and appreciate the uniqueness and suitability of each strategy to the various study types and also that not all methods can be effectively employed to every research. In order to effectively examine the business risks posed to or that could arise to the oil and gas sector of the Kingdom of Saudi Arabia as a result of cyber-attacks or cybersecurity threats/ breaches, and to determine the human factors among company employees that potentially facilitate cybercriminals as well as the extent to which the incorporation of employee trainings and awareness on cybersecurity could mitigate cybersecurity breaches; the systematic approach will be used in the conduction of this study. The reason for choosing this approach is grounded on its transparency in the manner in which they lead to the generation of the study’s conclusions. This transparency is brought about by a clear evaluation of the quality and relevance of the used literature and body of knowledge and thus, is crucial in that it minimizes or even eliminates the possibilities of readers (or researchers themselves) misinterpreting or not being clear about the knowledge base (Wahyuni, 2012) highlighted by the study. The systematic approach also ensures that the steps taken in conducting the research are clear; this results in the likely distortions or inaccuracies that would arise from the use of a less suitable method, and therefore contributes to the study’s findings being improved, strengthened and even looked at with confidence (Faux, 2010). The systematic approach of the study also makes it rather explicit and allows the readers some ability to appraise it, determine and decide for themselves whether or not the researcher was thorough in his conduction of the study and if they effectively achieved their objective for carrying out the research.
3.2 Research Philosophy
Of crucial importance to any research is the research philosophy. The type of research philosophy adopted by the researcher usually has a significant impact on the quality of the key data that is collected and necessary for conducting the research (Mackey and Gass, 2015). It is therefore incumbent on the researcher to identify and adopt a research philosophy that best suits his type of study as it will influence and determine the study’s general nature and quality. Generally, most research papers employ one of the three most common research philosophies; positivism, interpretivism and realism (Wahyuni, 2012). He also adds that each type of research philosophy tends to be advantageous or disadvantageous depending on the type of research on which it is employed. With a view to meeting his objectives for conducting this study, the researcher determined positivism as the best approach to adopt. The rationale for this choice is that positivism has, without any doubt, been proven over and over again to inhibit or eliminate any bias on the researcher’s part as he collects the data he will use, making him objective (Verschuren, Doorewaard and Mellion, 2010). This objectivity will consequently minimize the likely error margins (that would otherwise be greater if the researcher was biased) in the research’s findings. The greater consequence of this is that the study will highlight the true position and picture of the oil and gas sector in Saudi Arabia in relation to cybersecurity threats.
3.3 Research Approach
Research approach refers to the plan or process that entails the study’s general assumptions and in-depth methods used by the researcher to collect and analyse data and present the results so as to achieve the study’s objectives (Sekaran and Bougie, 2016). The two majorly recognized research approaches are; the inductive research approach and the deductive research approach (Mantere and Ketokivi, 2013). Consideration must be given to the type of research being conducted as well as the extent to which data crucial to the study is accessible before a research approach can be chosen. Deductive approach is best suited for those studies for which the key data is readily available and can be easily accessed, while in cases where the necessary data is limited or not easy to access, the inductive approach is preferred. In the case of this study, the researcher will use the large knowledge body and review multiple literature sources that are already available on the topic and use the resulting findings to draw conclusions that satisfy the set objectives. Using the deductive approach, given its support for the use of diverse literature sources, contributes to an improvement in the study’s overall quality (Rahi, 2017).
3.4 Research Design
The research design is a reflection of how the research is conducted and the appropriate actions or processes the researcher undertakes to answer the questions that the study seeks to address (Creswell and Poth, 2017). After, carefully considering the research type, a researcher can choose to adopt one or a combination of the following options; explanatory, descriptive or exploratory research design (Eastwood, Jalaludin and Kemp, 2014), among other designs. To adequately and effectively examine the business risks that cybersecurity breaches pose to the oil and gas companies in Saudi Arabia, the human/ people factor that contribute to the ease of cyber-attacks and the significance of trainings and awareness creation among company employees as a way of mitigating cybersecurity threats, this study chose to use the descriptive survey and cross-sectional research designs in combination. Descriptive survey research design helps determine and describe people’s attitudes, thoughts, behaviours, characteristics and values associated with the topic being researched (Gray, 2019), and because it has been proven to enhance the accuracy and adequacy of the interpretations of the results obtained by a study, it is deemed the most suitable for this research- which is a fact-finding one. The researcher also chose to adopt the cross-sectional research design which involves collecting the needed data within a single time period, as opposed to the longitudinal research design that is best suited for research that is conducted at different time points and over extended lengths of time, even several years (Sekaran and Bougie, 2016). These two research designs have been identified to improve the study’s overall accuracy and quality, given that it enables both primary and secondary sources of data and enhances the study’s validity (Rahi, 2017).
3.5 Data Collected and the Methods of Data Collection Used
The type of data or information collected and its availability are crucial aspects of a research as they have a bearing on how effectively the goals of the study are achieved and the research questions addressed. This study employed the use of both primary and secondary data, with primary data being the major type. Primary data is that which is being collected at the moment by the research being undertaken (Norris et al., 2015), whereas secondary data refers to data or information (from previous research studies) that is already available for the researcher’s reference, review and analysis of the various themes that recur and revolve around the research topic (Driscoll, 2011). Primary data usually brings to the for exploratory and specific information (Norris et al., 2015), and the specificity nature of this data will be the focus of this research as it is precise and will focus on answering the study’s research questions. The major data collection method used to collect data is the questionnaire, which can be found in the appendices section. The questionnaire included both open and close-ended questions. This method was chosen given its effectiveness in collecting a wide range of data from large sample sizes relatively quickly, with ease and convenience as well as its cost effectiveness (Testa & Simonson, 2017), as opposed to other methods such as interviews which would have proved more time-consuming and costly (Pozzo, Borgobello & Pierella, 2019) and surveys whose reliability is largely affected by the researcher’s interpretation of responses (Quinlan et al., 2019), which could be wrong. Questionnaires minimize the risk of the investigators’ wrong interpretation of responses and findings. However, questionnaires also lack the personal interactions between researchers and their respondents, making them lack in depth and intense analysis of the respondent’s feelings or values (Gray, 2019). In recognition of this shortcoming and for purposes of strengthening the findings of the questionnaires, the researcher also endeavoured to collect secondary data.
Secondary data was collected from secondary data sources such as articles, journals, books, magazines, reports and previous studies, were also used.
3.6 The Target Population
A target population is a very important aspect of any research study. Target population refers to the people the researchers will gather the primary data they use for their studies from. Uprichard (2013) asserts that it is important for a researcher to adopt the best sampling technique that will give him/her the most appropriate sample size that includes the right quality and number of the study’s respondents. The sampling techniques that researchers use can be broadly categorised as either probability or non-probability sampling techniques. This study employed the non-probability sampling strategy. In line with its focus, the study used the purposive or convenience sampling method that enabled it to identify and recruit valid respondents from the oil and gas sector companies, as opposed to other sampling methods such as random sampling or probability sampling that would have seen anybody able to participate in the study (Faux, 2010). The study drew a sample size of 200 respondents from the oil and gas sector, as they were the focus and target population of this study.
3.7 Data Analysis and Presentation
Since the study relies on the use of data that is both descriptive and qualitative in nature, the descriptive statistical analysis technique, aided by Microsoft excel, will be used to analyze the collected data. After analysis, the findings will be presented using tables, bar graphs and charts.
3.8 The Research Reliability and Validity
The emphasis of this study was on sampling validity which the researcher used with the intention of deriving the desired outcomes. Through sampling validity, the researcher was able to do an exploration of different issues that would come about from energy sector organizations in Saudi Arabia failing to effect adequate cyber awareness programs. Validity is achieved in those instances where after the piloting and testing of questionnaires, the produced data is meaningful to the extent that it is consistent with the outcomes that the researcher had (Drost, 2011; Pandey, 2014). To facilitate test-retest reliability, the researcher relied on the piloting and pre-testing samples. This was done in conditions that were similar to check for the similarity of results obtained in subsequent administration of questionnaires.
3.9 Ethical Considerations
A respondent had to give their consent before they could be allowed to participate in the study. The researcher sent different emails to the individuals who had been selected to participate with emails which contained the content form that was to be filled. The consent form contained the purpose of the study and also its objectives. Those individuals who responded to the emails with the filled consent forms were recognised having consented to taking part to the study, while those emails that were not responded to, the researcher assumed that the people did not consent to taking part in the study. Respondents were assured that their responses would be used in no other way, besides the research and that only the research team could access their responses. The researcher had to explain to potential participants the objective and relevance of the study, and allowed them to seek clarifications on various areas in order to be clear about whether or not they felt comfortable taking part in the research. Respondent consent can be obtained in different ways. In this study, for example, participants signed consent forms, while in other instances such as online surveys, an individual’s completion of the survey implied their consent (Connelly, 2014). The respondents were also assured of their anonymity and confidentiality of their personal details and responses. This assurance made them comfortable and confident to honestly and accurately respond to the questionnaires without fear, bias or prejudice (Sekaran and Bougie, 2016).
CHAPTER FOUR: FINDINGS AND DISCUSSIONS
4.0 Introduction
This chapter highlights the findings attained by the researcher after a thorough analysis of the data that was obtained from the questionnaires. To present the findings more elaborately, charts, graphs and tables are used.
4.1 Response Rate
Of the total 200 questionnaires sent out by the researcher, 160 of them were returned duly completed. 30 were also returned but were incomplete, while the remaining 10 were not returned. This represents a response rate of 80%. These findings are as illustrated in figure 4.1.

4.2 Participants’ Demographics
4.2.1 Participants’ Gender
102 (63.73%) of the 160 respondents were male, whereas the remaining 58 (36.25%) were female.
4.2.2 Respondents’ Ages
Of the 160 respondents who took part in the research, 30 (18.75%) were aged between 18 and 25 years, 34 (21.25%) of them 26-35 years, 40 respondents (25%) were aged between 36 and 45 years, 28 (17.5%) were between 46 and 55 years of age, and another 28 (17.5%) were over 55 years of age. These findings are illustrated in figure 4.2 below:

These findings show the inclusion and involvement of people of all age groups within the oil and gas sector industry in Saudi Arabia.
4.2.3 Highest Academic Levels Attained by the Respondents
On the highest academic qualifications held by the respondents, findings illustrated that 27 (16.875%) had attained a high school qualification, 35 (21.875%) of the respondents had a college certificate, 45 (28.125%) a college diploma, 29 (18.125%) had obtained an undergraduate degree from the university and the remaining 24 (15%) of the respondents had a post-graduate qualification. These findings can be said to portray the true picture of the industry, as it contains employees with various academic qualifications, and thus skill levels, depending on their roles and responsibilities in the organizations. These findings are shown in the table in figure 4.3. Information on the respondents’ academic qualifications is crucial since it helps to learn, with certainty, their job skills and competencies, and also their ability to correctly and accurately complete the questionnaires as required. The respondents’ attainment of at least a high school diploma points to their having the basic education, and therefore the capacity to duly complete the questionnaire.

4.2.4 Work Experience
On how long they had held their jobs or positions, 43 (26.875%) said that they had less than 5 years of work-related experience, 48 (28.75%) had between 5 and 15 years of work experience, 37 (23.125%) of the respondents responded that they had been on the job for between 16 and 30 years, while 32 (20%) of the respondents had worked for more than 30 years. These findings are as illustrated in figure 4.4.

Determining how long the oil and gas sector employees had been on the job is important since it helps underscore their experiences with cybersecurity. It would be expected that those who had been on the job longer would have more cybersecurity awareness and trainings that would influence their interactions with the organizations’ cyber systems and networks (Kennedy, 2016).
4.3 Organizational Cybersecurity Policy
On the question of whether or not their organizations had any form of cybersecurity, 120 respondents (75%) responded in the affirmative, while the remaining 40 respondents (25%) said their organizations did not have a cybersecurity policy. A clear and effective cybersecurity policy serves to guide the organization on the necessary measures it needs to take in order to prevent cyber-attacks or countermeasures to defend itself against arising cyber threats. As a result, companies and organizations should create and adopt comprehensive cybersecurity policies that would guide their training of employees and ensure that cyber regulations and guidelines are complied with always (Shackelford, 2016).
4.4 Effectiveness of the Organizational Cybersecurity Policies
Asked about how effective they thought their organizations’ cybersecurity policies to be, 30 respondents (25%) thought they were very effective, 35 (29.16%) of the respondents termed them effective, 20 respondents (16.67%) were neutral, another 20 (16.67%) deemed them to be ineffective, while the remaining 15 respondents (12.5%) thought of their organizations’ cybersecurity policies as very ineffective. These findings are shown in the table in figure 4.5 below:

Organizational cybersecurity policy plays a significant role in the prevention of and protection against likely cyber-attacks (Dehlawi and Abokhodair, 2013). Organizations are therefore advised to develop and implement sufficient cybersecurity policies as these would influence how effectively they manage their cybersecurity. Despite their relevance and importance to achieving cybersecurity goals and the numerous benefits they could bring about, most oil and gas sector organizations have tended to adopt defunct or ineffective cyber policies, while others totally lack any (Geers, 2011).
4.5 Employee Cybersecurity Awareness and/or training
The research also sought to examine whether or not the employees had some awareness and training on cybersecurity. 104 respondents (65%) claimed to have some form of cyber security awareness or training, while 56 (35%) responded in the negative. Previous research findings have shown that cybersecurity training and awareness are extremely low among employees, and even lacking in some instances, and most organizations are either unaware or uninterested and are putting in little effort towards this venture as they deem it as an unworthy investment (Caldwell, 2016). Lack of awareness and training among employees and their organizations’ disinterest or unwillingness to invest in changing the situation exposes them to increased cyber threats and risks (Bada, Sasse and Nurse, 2019). Employees who are not adequately aware or well-trained will be unable to undertake the necessary measures to protect the systems from cyber threats and to defend the system during attacks adequately.
4.6 Level of Cyber Security Awareness and Training
Merely having some knowledge or training on cybersecurity is not enough. Awareness and training should be sufficient enough to serve its intended purpose, which is to prevent and mitigate cyber threats. In this regard, the researcher sought to ascertain the respondents’ perceptions of their awareness and training levels. Of the 104 respondents who responded that they had cybersecurity awareness and training, 20 (19.23%) felt that their training and awareness were very sufficient, 24 (23.07%) believed them to be sufficient, 22 respondents (21.15%) were neutral, 17 (16.35%) of the respondents perceived their awareness and training as insufficient, while 21 (20.19%) thought of them as very insufficient. These findings are shown in figure 4.6. Employee awareness and training are critical dimensions of any organization’s cyber policy and regulations, and without them the organization could be badly hurt. Previous studies have found that a majority of the oil and gas sector employees have little to no cybersecurity training or knowledge- which could bear an insignificant impact on the prevention or mitigation of cyber threats, while only a few have what can be termed as adequate knowledge or training which could help them prevent and mitigate against cyber-attacks (Cain, Edwards and Still, 2018). Insufficient or total lack of awareness or training have been attributed to a majority of the cyber-attacks experienced by various organizations, with 78% of the organizations directly linking lack of employee awareness to 45% of the successful attacks. Organizations, in cognizance of the potential cyber threats they face, should rise up and create awareness and train their employees as a way of tackling cybersecurity issues. Since technology by itself is not the easy fix or the silver bullet that cybersecurity needs, an organization must not entirely depend on the “suitability and resilience’ of their systems; they should also invest in training their employees on what they ought to do since their cluelessness during a cyberattack could easily render the system- no matter how good- penetrable (Robert, 2015). Raising awareness, therefore, will significantly help the oil and gas sector in Saudi Arabia and other Middle East countries to boost its cybersecurity.

4.7 Cyber Breach Attempts and their Frequency
Asked if their organizations had experienced any cybersecurity breach attempts in the recent past, 154 respondents responded in the affirmative, while the other 6 responded no or were unaware of such attacks. These findings show the prevalence of cybersecurity attacks in the sector. On how frequently the cyber breach attempts occurred or were made by cybercriminals, 30 of the respondents said they occurred between 0 and 25 times, 44 responded that their organizations experienced 26 to 50 cyber breach attempts each month, 56 said the cyber breach attempts were made between 51 and 100 times each month, while 14 said their organizations’ cyber spaces were targeted in excess of 100 times monthly. This is shown in figure 4.7 below:

The increased digitization of processes, activities and systems in the gas and oil sector are increasingly exposing the sector to increased digital and cybersecurity threats, vulnerabilities and risks, and cybercriminals are increasing their stealth and sophistication in carrying out cyber-attacks (Alpi, 2017). That has led to them severally and continuously trying to gain access to various organizations’ cyberspaces (Al Neami & Lutaaya, 2015; Alpi, 2017; Bronk & Tink, 2013). A previous Symantec Study conducted in 2017 showed that the number of cyber-attacks targeted at the sector grew by at least 90 per cent compared to the year before, and these increased attacks also led to a 60% increase in the number of successful attempts.
4.8 Success of the Cyber Breach Attempts
On the question of if any of the attempts were successful, 76 responded yes, while the majority 78 no.
The number of successful cyber-attacks in the Kingdom of Saudi Arabia, and indeed globally, has, over the years, been increasing tremendously. Alelyani and Kumar (2018), in their previous studies, found that over 80% of the survey’s respondents reported their organizations as having experienced a significant increase in the number of successful cyber-attacks. The findings of a similar survey carried out by Dimensional Research in 2015 showed that 53% of the respondents said the cyber-attack attempts on their organizations increased by between 50 and 100 per cent (Dimension Research, 2015). A 2018 Symantec Study found that the success rate of cyber attack attempts increased by over 60 per cent in comparison to the previous year.
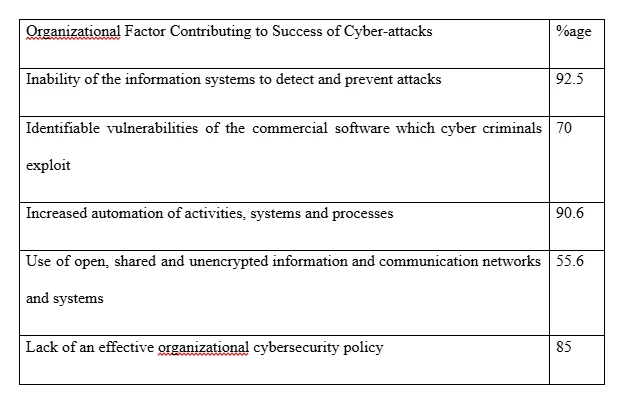
4.9 Organizational Factors that Contribute (d) to Success of Cyber-attacks
When it comes to the likely organizational factors that contributed to cyber-attack attempts by cyber criminals to succeed, 148 respondents (92.5%) attributed the success to the failure or inability of their organizations’ information systems to detect and prevent such attacks, 112 respondents (70%) claimed the commercial software, rather than the proprietary, which the organizations used, and which had certain vulnerabilities (that cyber criminals could identify and exploit in order to illegally enter the organizations’ systems) led to the success of certain cyber-attacks, the increased automation of oil and gas sector organizational activities, systems and processes was identified by 145 (90.6%) respondents as contributing to the success of cyber-attacks, only 89 respondents (55.6) attributed the success of cyber-attacks to their organizations’ usage of open, shared and unencrypted information and communication networks and systems, whereas 136 (85%) respondents identified their organizations’ lack of a comprehensive and useful cybersecurity policy as a contributing factor. These findings are illustrated in the table in figure 4.8 below.
As companies rise to protect and defend their systems from cyber intrusions and threats, the attackers are also evolving and finding even newer, more sophisticated ways of attacking. In the majority of the situations, organizations are usually at a disadvantage since the attackers have the advantage of surprise and can choose their target as well as the place and time of attack. That, among other factors, as identified, has seen a significant number of the globe’s largest oil and gas sector organizations fall victim to cyber-attacks since the year 2008 (Pepitone, 2011).
Despite their best efforts, some aspects of the organizations still leave them extremely exposed to cyber-attacks and breaches. The findings of this study on this question are in line with those of previous research works which also identified some of these factors including the inability or inadequacy of the organizations’ systems to detect and repel attacks (Henrie, 2013), the vulnerabilities of the commercial software used by the organizations that the hackers can identify and exploit, the increased digitization and integration of the OTs and IT networks or systems (Rosendahl and Hepso, 2013; Lamb, 2018) and the organizations’ lack of effective cybersecurity policies (Quigley, Burns and Stallard, 2015). It has also been found that the sector’s reliance on digitization and digital transmission of information has, in the recent years, made it even more vulnerable to cyber espionage whereby hackers intent on gathering national security or business intelligence covertly try to gain access to the organizations’ confidential and sensitive internal communications and data (Awad and Battah, 2011).
4.10 People Factors and Human Error as Causal Factors of Cyber Breaches
The information systems’ and network's technical sophistication, dimensions and abilities cannot be wholly relied upon in isolation to help protect and prevent against cyber breaches. In this regard, therefore, the researcher sort to examine to what extent the respondents agreed that the employees’ people factors and the errors they committed facilitated the increased number of cyber-attacks and breaches. An analysis of the responses found that 66 of the respondents strongly agreed, 55 agreed, 21 were neutral, 11 respondents disagreed, while the other 7 respondents strongly disagreed. Recent and previous studies have attributed close to 80 percent of all cybersecurity incidents that happen offshore to human error (Boyce et al., 2011). These human errors, it has been argued, are brought about by a lack of cybersecurity awareness and training among employees as well as the lack of a clear cybersecurity policy by the organization (Halevi, Lewis and Memon, 2013; Greitzer et al., 2014). A recent Symantec Study of 2018 showed that out of 392 emails, at least one contained phishing attacks that could quickly spread and infect the organizations’ systems and computers if accidentally opened (Taddeo, 2019).

4.11 People Factors and Human Errors that Increase the Potential for Cyber Attack Success
The researcher also sought to investigate the various people factors and human errors among the oil and gas sector organizations’ employees that increased the likelihood of cyber breach attempts succeeding. 93.75 per cent (80) of the respondents identified their lack of or insufficient awareness or training on cybersecurity as the most outstanding people factor that facilitated the success of cyber attack attempts, 145 (90.625%) identified opening spam emails that contained and spread malicious software and codes among the organizations’ computers and systems, 123 (76.875%) of the respondents ticked against connecting mobile phones, hard drives and other personal electronic devices to critical organizational computer systems as the other human error that increased success chances of cyber breach attempts, 138 (86.25%) attributed this success to the employees’ conduction of personal, unnecessary and even unauthorized activities on the organizations’ cyber systems, 96 (60%) of the respondents said the success of such cyber breach attempts were facilitated through the employees’ writing, revealing or making the systems’ passwords known to unauthorized individuals, 125 respondents (78.125%) identified the employees’ failure or forgetting to carry out important and crucial system activities, for example updating and/or changing system passwords regularly as required to be the other human error that increased the possibility of cyber-attacks succeeding, while 109 (68.125%) attributed the increased success chances to the employees’ performing of system activities and process in the wrong manner or without following the laid down procedure. These findings are illustrated in the table in figure 4.9 below.
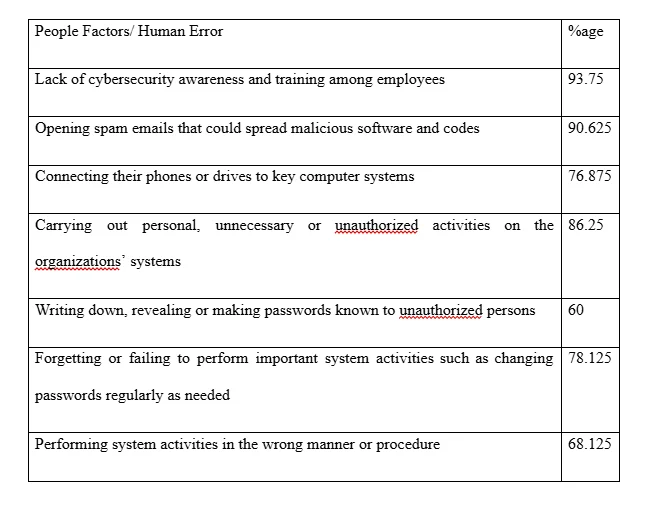
Various (a greater majority, in fact) of cyber-attacks have been facilitated by the people factors and human errors made by employees. The ease with which some of these attacks were and are carried out exposes the systems’ weaknesses in handling cyber threats and the need for increased awareness on matters cybersecurity among the employees (Lebek et al., 2013). For example, the Stuxnet, a malicious worm, that was used to attack various industrial control systems (ICSs) in 2010 including the computers that managed gas pipelines, oil refineries and power plants, and ended up damaging one fifth of nuclear centrifuges in Iran was delivered via a flash drive of one of the workers. Various acts of omission and commission by organization employees such as failing to regularly change passwords as required, opening dangerous emails, writing down passwords, connecting their phones, drives and laptops to the systems and conducting personal, unnecessary and unauthorized activities on the system all facilitate the possible success of cyber-attacks (Huang, Rau and Salvendy, 2007; Conteh and Schmick, 2016)
4.12 Business Risks Posed to Organizations by Successful Cyber-attacks
The researcher also sought to find out the various business risks that cyber-attacks and breaches posed to the oil and gas sector organizations in Saudi Arabia. The results showed that disruption of normal organizational and activities was identified as the most common and prevalent business risk posed to organizations by cyber breaches as 154 respondents (96.2%) ticked against it, the massive financial losses occasioned by this disruption of normal operations and processes was also identified by 152 (90%) of the respondents, a further 149 (93.125%) respondents said successful cyber-attacks resulted in the organizations losing or having their critical and confidential operational information stolen by the cyber criminals, 128 (80%) of the respondents said the failure of operating and mechanical equipment occasioned by successful attacks caused the employees working with the said equipment to suffer physical harm or injuries, while 70 (43.75%) of the respondents said such failure of operating and mechanical equipment, in some instances, resulted in fatalities among employees. 125 (78.125%) of the respondents also identified that cyber-attacks of a certain type, ransomware in particular, saw the organization having to pay ransoms to attackers in order to have them stop such attacks and to restore the organizations’ systems for them to continue operating normally, 145 (90.625%) of the respondents said such attacks often led to the organization losing or the attackers accessing and stealing the organizations’ proprietary and intellectual information, whereas 131 respondents said successful cyber-attacks made the organizations’ overall image and reputation to be tainted and affected negatively. These findings are shown in the table in figure 4.10 below:

These findings, put together with the ones above, portray two significantly clear trends with regard to cybersecurity in the oil and gas sector: cyber-attacks keep increasing; and these attacks are becoming more dangerous and their impacts are continuously increasing. Cyber attackers and criminals range from those attacking organizations in order to be paid ransom to those working on behalf of business rivals within and outside the sector and those sponsored by the state. Although all groups are dangerous, state-sponsored cyber criminals are well-funded and have a massive potential to cripple critical infrastructure. Successful cyber breaches have threatened the oil and gas industry and its global competitiveness in a number of ways. Previously, cyber breaches were mainly aimed at the theft of the sector’s intellectual property and business strategies (Simmons et al., 2014). However, in the recent years, the occurring cyber and malware attacks have qualitatively changed and bear the potential to physically disrupt the sector’s operations and global oil and gas supply chain (Agrafiotis et al., 2018). Shamoon which was unleashed on the National Oil Companies’ computers in August 2012 by an individual who enjoyed special access was found to have a significant damage as it ended up destroying (erasing) three quarters of the company’s computers, leading to its internal network being shut down (Perlroff, 2012). It is believed, however, that the physical damage could have been greater had the company’s internal communication network and oil production operations not been separate (Bronk and Tikk-Ringas, 2013). A cyber criminal with the right tools, knowledge and access who identifies the Supervisory Control and Data Acquisition systems (SCADA) and ICS connected to the internet and used to control critical infrastructure and processes. Once they gain access to the systems, they could, in theory, halt the flow of gas and oil through the pipelines, trigger an explosion or cause oil spillage, aceess the company’s trade secrets, steal or erase important confidential and critical intellectual and operating information, hijack operating systems. Such actions and threats cost the sector massive financial losses, information theft and loss, cause energy supply disruptions, damage the environment, cause physical injuries and even loss of human life (Genge, Kiss and Haller, 2015).
CHAPTER FIVE: CONCLUSION AND RECOMMENDATION
5.1 Introduction
Besides a significant number of the traditional physical and operational dangers that the oil and gas sector in the Kingdom of Saudi Arabia and world over, the sector also has to grapple with the ever evolving and escalating cybersecurity attacks that pose immense risks to it. Although different sources provide different figures and statistics, they are all in agreement with regard to two particular trends they highlight: that cyber-attacks continue to increase and their impacts are becoming even more pronounced.
5.2 Key Findings
The oil and gas sector is a particularly high-value target for the attackers given the all-important position it holds and the role it plays in the economy of Saudi Arabia and other Middle East countries. The increasing digitization witnessed in the sector over the years has in most cases been attributed to its increased vulnerability to cyber threats and attacks. Previously, the industry’s operating technology (OT) networks were not available on the internet (online) but this has changed in the recent years due to the sector’s need for efficiency, effectiveness and cost reduction. This need led to the integration of the OT with the IT and its availability on the internet, further leading to them using commercially available software, instead of proprietary software, which hackers could easily identify and exploit. Cyber criminals have, over the years, evolved and from the underfunded lone actors to state-sponsored hacker teams, and the cyber threats they unleash take numerous forms and have become more sophisticated. The increasing boldness, sophistication and stealth of cyber attackers have enabled them succeed in quite a number of their attempts, and these successful attacks have had numerous far reaching and negative impacts such as disruption of the sector’s processes and operations, loss or theft of critical and confidential operating information, theft of intellectual property, disruption of the global oil and gas supply chain, massive financial asset loss, damaged organizational reputation or image, spills, explosions and fires that damage the environment, physical harm and even loss of human life. A number of factors have been attributed to the success of the various attacks that have caused devastating impacts on the sector’s organizations and companies. Some of them are; lack of awareness and training on cybersecurity among employees, the organizations’ lack of effective and elaborate cybersecurity policies, and a number of human factors and errors by the employees that ease the attackers’ intrusion into the organizations’ systems and networks.
In light and recognition of these factors, organizations have moved to take steps and measures aimed at strengthening their cybersecurity. Among the measures they have adopted include; appreciating the importance of and developing effective cybersecurity policy(ies) that guide them and their employees in their interactions with the cyber systems, training and creating cybersecurity awareness among their employees- equipping them with the necessary skills needed to adequately detect, prevent and defend the systems against cyber-attacks, as well as adopting and using sophisticated equipment and systems with the technical abilities able to detect, repel and withstand attacks.
5.3 Recommendations
With these measures, however, the attackers have also been changing tact and becoming even more sophisticated in their attacks. This has caused the various measures taken by the oil and gas sector organizations not to have the necessary impacts they were intended to. It is, therefore the recommendation of this research paper that the oil and gas sector organizations should invest even more on their security and adopt holistic strategies that can wholesomely protect and defend their systems from dangerous attacks. Organizations should set out to develop and implement effective cybersecurity policies that would guide their interactions with the systems. These cybersecurity policies will also advocate for positive behavior change that helps reinforce cybersecurity. Through such policies, organizations will also develop frameworks for creating awareness among and training their employees on cybersecurity. As such, organizations should stop viewing the training and creation of awareness on cybersecurity among their employees as a cost but as an investment that will go a long way in boosting their cybersecurity and bear them great results, albeit not readily seen. In this regard, the research recommends that organizations should put more emphasis on their employees, rather than entirely on the technical strengths and capabilities of their systems when it comes to repelling cyber-attacks. This is because, regardless of the systems capabilities, they remain susceptible and highly exposed to attacks as long as the employees operating them are not aware or adequately trained on the right things to do to keep the systems secure and the actions to take to defend them against arising threats.
REFERENCES
Agrafiotis, I., Nurse, J.R., Goldsmith, M., Creese, S., and Upton, D., 2018. A taxonomy of cyber-harms: Defining the impacts of cyber-attacks and understanding how they propagate. Journal of Cybersecurity, 4(1), p.tyy006.
Alelyani, S. and Kumar, H., 2018. Overview of Cyberattack on Saudi Organizations.
Alshahrani, H.A., 2016. A brief history of the Internet in Saudi Arabia. TechTrends, 60(1), pp.19-20.
Alzahrani, A. and Alomar, K., 2016. Information security issues and threats in Saudi Arabia: A research survey. International Journal of Computer Science Issues (IJCSI), 13(6), p.129.
Amin, S. and Sastry, S., 2015. 1 Introduction 2 Analysis of the Secure Control Problem’, Control, pp. 1–14.
Awad, H.A. and Battah, F.M., 2011. Enhancing Information Systems Security in Educational Organizations in KSA through proposing security model. arXiv preprint arXiv:1111.6757.
Bada, M., Sasse, A.M. and Nurse, J.R., 2019. Cyber security awareness campaigns: Why do they fail to change behaviour?. arXiv preprint arXiv:1901.02672.
Badie, N. and Lashkari, A. H., 2012. A new Evaluation Criteria for Effective Security Awareness in Computer Risk Management based on AHP, Journal of Basic and Applied Scientific Research, 2(9), pp. 9331–9347.
Basamh, S.S., Qudaih, H.A. and Ibrahim, J.B., 2014. An Overview on cyber security awareness in Muslim countries. International Journal of Information and Communication Technology, 4(1).
Beautement, A. et al., 2016. Productive Security: A scalable methodology for analysing employee security behaviours, in Proceedings of the Symposium on Usable Privacy and Security (SOUPS). Ben-Asher, N. and Gonzalez, C., 2015. Effects of cyber security knowledge on attack detection, Computers in Human Behaviour. Elsevier Ltd, 48(June), pp. 51–61. Doi: 10.1016/j.chb.2015.01.039.
Black, P., 2018, September. Cyber Security, the Cloud, and Oil and Gas. In SPE Annual Technical Conference and Exhibition. Society of Petroleum Engineers.
Boyce, M.W., Duma, K.M., Hettinger, L.J., Malone, T.B., Wilson, D.P. and Lockett-Reynolds, J., 2011, September. Human performance in cybersecurity: A research agenda. In Proceedings of the Human Factors and Ergonomics Society annual meeting (Vol. 55, No. 1, pp. 1115-1119). Sage CA: Los Angeles, CA: SAGE Publications.
Buczak, A.L. and Guven, E., 2015. A survey of data mining and machine learning methods for cyber security intrusion detection. IEEE Communications surveys & tutorials, 18(2), pp.1153-1176.
Cain, A.A., Edwards, M.E. and Still, J.D., 2018. An exploratory study of cyber hygiene behaviors and knowledge. Journal of information security and applications, 42, pp.36-45.
Chan, C.K. and Cheng, L.M., 2001. Cryptanalysis of a timestamp-based password authentication scheme. Computers & Security, 21(1), pp.74-76.
Conteh, N.Y. and Schmick, P.J., 2016. Cybersecurity: risks, vulnerabilities and countermeasures to prevent social engineering attacks. International Journal of Advanced Computer Research, 6(23), p.31.
Dehlawi, Z. and Abokhodair, N., 2013, June. Saudi Arabia's response to cyber conflict: A case study of the Shamoon malware incident. In 2013 IEEE International Conference on Intelligence and Security Informatics (pp. 73-75). IEEE.
Domingo-Ferrer, J., Ricci, S. and Domingo-Enrich, C., 2018. Outsourcing scalar products and matrix products on privacy-protected unencrypted data stored in untrusted clouds. Information Sciences, 436, pp.320-342.
Eastwood, J.G., Jalaludin, B.B. and Kemp, L.A., 2014. Realist explanatory theory building method for social epidemiology: a protocol for a mixed method multilevel study of neighbourhood context and postnatal depression. SpringerPlus, 3(1), p.12.
Ernst & Young, 2007. 10th Annual Global Information Security Survey: Achieving a Balance of Risk and Performance. Ernst & Young.
Ferguson, A., 2005. Fostering e-mail security awareness: The West Point Carronade. Educause Quarterly, 28(1), 54-57.
Genge, B., Kiss, I. and Haller, P., 2015. A system dynamics approach for assessing the impact of cyber-attacks on critical infrastructures. International Journal of Critical Infrastructure Protection, 10, pp.3-17.
Greitzer, F.L., Strozer, J.R., Cohen, S., Moore, A.P., Mundie, D. and Cowley, J., 2014, May. Analysis of unintentional insider threats deriving from social engineering exploits. In 2014 IEEE Security and Privacy Workshops (pp. 236-250). IEEE.
Halevi, T., Lewis, J. and Memon, N., 2013, May. A pilot study of cyber security and privacy related behavior and personality traits. In Proceedings of the 22nd international conference on world wide web (pp. 737-744).
Huang, D., Rau, P.P. & Salvendy, G., 2007. A survey of factors influencing people’s perception of information security. In J. Jacko (Ed.). Human-Computer Interaction, Part IV. Heidelberg: Springer.
Knowles, W. et al., 2015. A survey of cyber security management in industrial control systems, International Journal of Critical Infrastructure Protection. Elsevier, 9, pp. 52–80
Lebek, B., Uffen, J., Breitner, M.H., Neumann, M. and Hohler, B., 2013, January. Employees' information security awareness and behavior: A literature review. In 2013 46th Hawaii International Conference on System Sciences (pp. 2978-2987). IEEE.
Li, L., He, W., Xu, L., Ash, I., Anwar, M. and Yuan, X., 2019. Investigating the impact of cybersecurity policy awareness on employees’ cybersecurity behavior. International Journal of Information Management, 45, pp.13-24.
Macaulay, T. and Singer, B.L., 2012. ICS vulnerabilities. Cybersecurity industrial control systems SCADA, DCS, PLC, HMI, SIS [Internet]. Boca Raton (FL): CRC PRESS: Taylor & Francis Group, pp.81-124.
Martin, J.D., Martins, R.J. and Naqvi, S., 2018. Media use predictors of online political efficacy among Internet users in five Arab countries. Information, Communication & Society, 21(1), pp.129-146.
McFadzean, E., Ezingeard, J.N. and Birchall, D., 2007. Perception of risk and the strategic impact of existing IT on information security strategy at board level. Online Information Review.
Norris, J. M., Plonsky, L., Ross, S. J., & Schoonen, R. (2015). Guidelines for reporting quantitative methods and results in primary research. Language Learning, 65(2), 470-476.
Pandey, S.C. and Patnaik, S., 2014. Establishing reliability and validity in qualitative inquiry: A critical examination. Jharkhand Journal of Development and Management Studies, 12(1), pp.5743-5753.
Pozzo, M. I., Borgobello, A., & Pierella, M. P. (2019). Using questionnaires in research on universities: analysis of experiences from a situated perspective. Revista d'Innovació i Recerca en Educació, 12(2), 1.
Quigley, K., Burns, C. and Stallard, K., 2015. ‘Cyber Gurus’: A rhetorical analysis of the language of cybersecurity specialists and the implications for security policy and critical infrastructure protection. Government Information Quarterly, 32(2), pp.108-117.
Rowe, N.C. and Goh, H.C., 2007, June. Thwarting cyber-attack reconnaissance with inconsistency and deception. In 2007 IEEE SMC Information Assurance and Security Workshop (pp. 151-158). IEEE.
Simmons, C., Ellis, C., Shiva, S., Dasgupta, D. and Wu, Q., 2014, June. AVOIDIT: A cyber attack taxonomy. In 9th Annual Symposium on Information Assurance (ASIA’14) (pp. 2-12).
Srinivas, V.B. and Umar, S., 2013. Spoofing Attacks in wireless Sensor Networks. International Journal of Computer Science Engineering & Technology, 3(6).
Standard, S., Greenlaw, R., Phillips, A., Stahl, D. and Schultz, J., 2013. Network reconnaissance, attack, and defence laboratories for an introductory cyber-security course. ACM Inroads, 4(3), pp.52-64.
Ten, C.W., Manimaran, G. and Liu, C.C., 2010. Cybersecurity for critical infrastructures: Attack and defense modeling. IEEE Transactions on Systems, Man, and Cybernetics-Part A: Systems and Humans, 40(4), pp.853-865.
Urciuoli, L., Mohanty, S., Hintsa, J. and Boekesteijn, E.G., 2014. The resilience of energy supply chains: a multiple case study approach on oil and gas supply chains to Europe. Supply Chain Management: An International Journal.
Wahyuni, D., 2012. The research design maze: Understanding paradigms, cases, methods and methodologies. Journal of Applied Management Accounting Research, 10(1), pp.69-80.
Yan, Y., Qian, Y., Sharif, H. and Tipper, D., 2012. A survey on cyber security for smart grid communications. IEEE Communications Surveys & Tutorials, 14(4), pp.998-1010.
- 24/7 Customer Support
- 100% Customer Satisfaction
- No Privacy Violation
- Quick Services
- Subject Experts



