Cloud Computing: Growth and Impact
CHAPTER 1: INTRODUCTION
Background Information
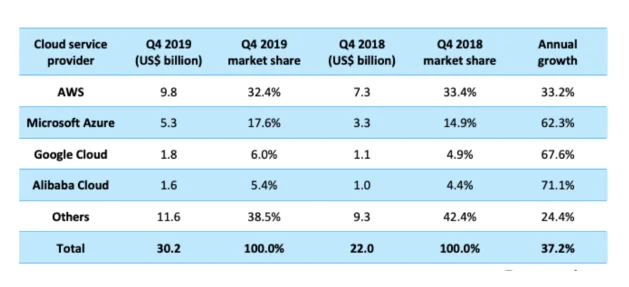
In the last decade, popularity of the cloud computing has grown and continues to spread at both business and individual levels. As pointed by Arora and Gupta (2012), organizations have shifted their operations from a traditional on site to digitalised approaches characterised by storing data and servers off site that can be accessed by employees and other shareholders anywhere, anytime, and on any device. Industry analysts highlighted that the revenue generated by cloud computing services reached $182.2 billion in 2018 and estimated to return approximately $331.2 billion by the end of 2022 (Gartner, 2019). Compared to overall IT market grown, the cloud services indicated a seven times growth rate as well as attaining 12.6% compounded annual growth rate. According to Columbus (2019), by 2021, more that 50% of the IT capabilities would by cloud dependent and delivered via cloud services such as business intelligence, enterprise resource planning, storage, and project and portfolio management.

Mohammed et al. (2016) pointed to such factors as strive for increasing productivity, need for higher consumer experiences, seeking quick time to market approach, and cutting operation cost as well as security as core driving forces in migration to the services by organizations. The increasing reliance on the remote over-the-internet services by organizations has seen a huge entry by both big and small business entities to offer the services. As such, the top cloud services providers measured by market share and revenue generated available across the globe Amazon (AWS), Microsoft, Google, and IBM facilitating the services over the cloud and the tools to move the applications effectively to the cloud system (Rouse, 2020).
Broadly, cloud migration is the process which involves the transmission of applications, data or additional business elements to the cloud computing environment. Numerous studies have highlighted benefits of using cloud-based services pointed to capability of hosting data and applications in an effective manner within the IT environment grounded on factors like cost, performance, scalability, flexibility and security (Aljabre, 2012; Bhardwaj et al., 2010; Hsu et al., 2014). Cloud computing support such services as data storage, analysis, and networking through available on demand databases and resources (data analytics software, project management platforms, and analytics offered over the internet, virtually. Recent the concept of working from home where employees can access organization’s infrastructure, software, applications, and other resources from remotely, from home, then work on the respective tasks. Notably, as pointed by Novet (2020), working remotely is not limited to accessing central infrastructure but goes beyond a shared working environment that include resource among other employees and organizations and establishing a platform that eases coordination, communication, and monitoring tasks and processes.

The approach eventually releases an initiative IT group from the liability of the management of the time. Migrating data to the cloud facilitates flexibility of resources, economies of scale, and fasten productivity and innovation in a manner that people and to that extension organizations are not limited to their resources hence allowing growth (Davidi 2013). The migration of data and resources to the cloud facilitates flexible working environment as well as reliability supported by such approaches as on-demand services, broader network access, resource pooling, and rapid elasticity with demand (Chang et al., 2015; Gholami et al., 2016). Largely, these virtually offered services can be categorized depending on user needs such as infrastructure (hardware and servers), platform providing development environment, software offering a centrally licensed and hosted software, network enabling connectivity and bandwidth, and functions where users can built, run, and secure application (Menzel, and Ranjan, 2012). More so, these cloud-based services can be deployed within public, private, community, or in combination of private and public (hybrid format). Public cloud provides scalability via pay-per-usage model, while private cloud provides us with extra control and increased security level and hybrid model provides us with the benefits of both and the best though the performance and connectivity may suffer.
Research problem
In today’s era informed by technology- and information-dependence, change happens at astronomical pace evident by growth in the technologies and supporting infrastructure in addition to organization shifting to adopt approaches aimed at addressing consumer’ need, enhance productivity, and addressing problems faced like security and coordination more efficiently. Any operating business firms or organizations needs to be updated with modern technologies and infrastructures. Those organizations should also be updated about the latest ongoing changes with the system, networks and optimum availability of the storage for their data and resources. Its other computing resources should also be managed and updated based upon the requirement of the organizations. Managing and controlling all those computing services by an organization can be extremely difficult and challenging. So, the cloud system develops the easier and most prominent ways to keep updated and regular maintenance and up-gradation of the system with the facilities of the scalability within the reliable cost for those services (Arora et al., 2013). To resolve all these problems faced by the business organization in today’s era cloud system allows the facilities of the flexibility, performance, cost and scalability which allow updating the system with the optimum storage of their data and higher security to those stored data of any business firms. However, several available services providers, services types, and deployment models, rises the questions of what model to adopt, and which cloud service is applicable for your new model, IaaS, PaaS, SaaS?
Research aims
The main aim of this project is to determine the cloud development environment and the overall migration process model involved in it. It is also focused on development of the cloud environment with the various strategies and methods used for the successful completion of the migration process. It is grounded on the types of services and securities provided by the cloud system in its environment to execute the task or perform any task.
Research objectives
This research is built around the following objectives:
To identify the benefits obtained from the cloud migration.
To critically explore the process of cloud development and cloud migration process.
To examine different types of cloud providers and migration partners.
To examine different types of services and security provided by cloud-based environment.
To recommend the strategies of improving effectiveness of cloud computing system for the users.
Research questions
Following are research questions driving this research project:
What are the major benefits of cloud migration?
What are different types of services and security provided by cloud-based environment?
What are the major companies which provide cloud migration services?
What is your proposed migration process model?
What strategies can be recommended for improving effectiveness of cloud computing system for the users?
CHAPTER 2: LITERATURE REVIEW
Chapter Introduction
The main purpose of literature review section is to review literature and already published information from different sources such as books, journals, articles, websites and academic scholars. In this chapter, the collected information from different sources is analyzed critically to gain in-depth knowledge about the research issue.
Cloud computing
In the words of Armbrust et al., 2010, cloud computing can be defined from a variety of perspectives at the exploratory stage. The National Institute of Standards and Technology has developed general ideas about cloud computing and has been generally accepted by the public. The cloud can be defined as a model that allows various computing resources to be shared as services to different customers. With this need in mind, customers can easily modify or adjust their services in this model. Along with this, Dillon et al., (2010) have stated that cloud computing is a service provided with applications and software systems in the data center, and it pays special attention to the meaning of services related to cloud computing. The cloud involves software and hardware that can be used and accessed by virtualized resources, and illustrates changes in cloud computing and other paradigms.
Cloud Computing Architecture
Cito et al., (2015) have demonstrated that cloud development involving integrated and enhanced environments, all aspects of application lifecycle management, such as quality testing and management, source code, configuration management and continuous delivery applications, and security test applications. In addition, Lim and Hong (2010) have depicted that the process of effective business interaction in a cloud environment. The integrated ontology integrates service providers, as cloud customers and business processes are required. Figure 2.1 below show relation of components and subcomponents capturing the frontend platforms and backend platforms as well as connecting platform. The frontend consists of cloud clients consisting of fat client and thin client, servers, and mobile devices, and backend made up of the traffic control mechanism and security for the cloud consumers as well as providing middleware for connectivity and communication of devices (Furht, and Escalante, 2010; Khmelevsky, and Voytenko, 2010). The computing resources are servers, data, middleware, O/S, runtime, virtualization, network, applications, and storage (Fowley and Pahl, 2016).

Cloud Migration
Jamshidi et al., (2013) pointed out that cloud migration is related to the process of transferring data, applications and other business elements through the on-site computers of the business organization to the migration from one cloud environment to another. In the word of Gholami et al., (2016), cloud migration is a method of heart-rending digital business operations into the cloud. Cloud could be defined as the servers which are accessible via the internet only, and it also permits the various software and database to run over those servers (Armbrust et al., 2010; Dillon et al., 2010; Rittinghouse, and Ransome, 2016). Cloud servers are situated in data centers across the globe. Cloud migration is a kind of physical move besides moving data, applications and IT procedures from some data centers in spite of packing the physical goods. It is quite similar to the migration of the office from the smaller workspace to the larger workspace beside the difference that migration towards the cloud environment requires lots of advance level work with the possible benefits like scalability, flexibility, cost saving and many more (Armbrust et al., 2010). Along with this, Ahmad and Babar (2014) have depicted that cloud migration is migration from on-premises to the cloud environment, and it could also be applied for the migration of the overall stored database and software from one cloud system to another cloud system. Most of the cloud migration process involves the transfer of the data and running application from the on-premises of any business firm to the cloud environment (Pahl et al., 2013). Depending upon the business needs and requirements, migration of the overall system from the on-premises to the cloud environment differs. Thus, the cloud migration process is a way of moving digital business operations into cloud. Some of the company directly migrates to the cloud environment else follows the legacy system to back up their data or prefers hybrid cloud distribution. Cloud computing migration may include data transfer or other business elements in a cloud environment, these elements are called cloud-to-cloud migration. Along with this, Gholami et al., (2016) have demonstrated that cloud migration requires security to ensure confidentiality. Like various active attacks, the migration can be performed powerfully and effectively without data loss. There are multiple ways to ensure cloud migration. Various organization have willingness to move their existing legacy application for the cloud environment due to facing various kinds of issues while adopting new technologies, platforms and standards. The problems may include less agility, longer time for market, maintenance cost, challenges in integration and challenges in upgrading. According to Shiraz and Gani (2014), key elements pushing shifting operations into cloud-based has always been scalability and availability of resources. In mobile cloud computing (MCC), according to, has leverage application processing services in a manner that users seek to offload intensive applications (storage and memory demanding applications). Therefore, many mobile device owner, for instance, seek the service of cloud computing when in use of resource-intensive mechanism. Wei and Blake (2010) argued that as an extension to the service-oriented computing (SOC) shared environment and distribution of application among multiple components gives benefit from cloud services such as pay-per-use pricing models. However, although largely migration is depended on the models and types, decisions are mostly guided by portion of the application stack and the process to follow guaranteeing acceptance of the service. Moreover, other consideration in migration are security and integration issues (Dillon et al., 2010; Petrenko, 2014). Kaisler and Money (2011) contended that to that migration are guided by acquisition, implementation, and security. In a study exploring the factors influencing adoption of cloud migration conducted by Rai et al. (2015) found a five-phase stage in migration and implementation, as follows: feasibility study, analysis of requirement and migration planning, execution of migration, testing and migration validation, and monitoring and maintenance. Nevertheless, research by West (2014) suggest that migration is a subject to trust on cloud services providers coupled by cost advantage, sensing capabilities, and application complexity. Alharthi et al. (2017) on the critical factors for success implementation of cloud migration pointed that identifying enablers within a given application. As such, one can argue that migration is subject to services and resources available, and goals for adopting cloud-based services.
Process Model
There are several types of cloud-based services but three types are most prominent and widely used. These are: Infrastructure as a Service (IaaS), Platforms as a Service (PaaS) and Software as a Service (SaaS). There are various computing resources to be handled and controlled while handling the software. In the model named “On-premises,” all the computing resources need to be handled by own self where the company itself has its own server and control all the computing resources involved in it.
Infrastructure-as-a-Service (IaaS)
In Infrastructure-as-a-Service model, data, applications, middleware, runtime and O/S needs to be managed by the user while the remaining section is managed by the service provider (cloud). In the words of Pahl and Xiong (2013), IaaS model allows to control and monitor applications, data, runtime, middleware and O/S computing resources of the system while the remaining section is controlled by the vendors. This system implication allows the data security as it allows managing the data and applications used in this system by the company itself.
Provides Computing architecture and Infrastructure.
Vendors will handle Data storage, Virtualization, Servers, and Networking.
System administrators will use this service.
Example: House, Amazon Elastic Compute service and Google Compute Engine.
The owner will give house with few items like bed and table to the end user to use these facilities and pay the rent, so user can setup the house as user likes. The owner was given Infrastructure to the end user in the form of service. It is free to choose the architecture that user wants and more flexible, it supports dynamic workloads (Bhoyar and Chopde, 2013). This service is basic underline structure. Furthermore, this service is much expensive than the PaaS and SaaS services.
Platform-as-a-Service (PaaS) model
The Platform-as-a-Service is a model in which the applications and data are managed by the business company owner and the remaining computing resources are managed by the service provider (cloud). In the words of Rani and Ranjan (2014) PaaS system manages only applications and data remaining computing resources are controlled by the vendors itself. The platform as given to the developers in the form of a service, it gives complete platform for applications development, deployment, and testing. It is highly scalable and cost effective. It simplifies the development process that minimizes the organizational costs. Along with this, Doelitzscher et al., (2011) have determined that PaaS service is faster for developers because the vendor will provide all computing resources like server-side components, they can use existed resources to build an application in a much better way along with it is easy to deployment of web applications. PaaS is also offering different flexible pricing plans for different kinds of businesses. It supports multi programming language as well as private and public cloud deployment. The cloud provider will give a platform with certain restricted languages only defined by vendor. Example: Google App Engine and AWS Elastic Beanstalk.
Software-as-a-Service (SaaS) Model
In the model, all the computing resources are controlled by the service provider (cloud) only. The cloud provider will give complete software in the form of a service. Freet et al., (2015) have stated that all the computing resources are controlled and managed by the vendor itself in SaaS modeling. If any system fails, then the business company could easily claim with the vendor to resolve it. But in this SaaS system, there is no data security of the company data and contracts as all the data are transparent to the vendors. The best model preferred across the globe is SaaS modeling process as it provides on demand service. In addition, it is an independent platform and not necessary to install on PC. It is universally accessible from any platform, user no need think about which operating system is using whether windows, Mac, etc. Vendor will provide modest software tools for the users can access. It allows multi tenancy. This service ideal choice for small business also. For example: Gmail (Process of sending an email), Google Docs, and Microsoft Office 365 are used by the organizations to manage their business operations in efficient manner. The table below presenting comparison between On-premises, IaaS, PaaS and SaaS services. The table outlines activities as managed from the users’ end of service provider’s. In the on premises model, the user owners the server all the activities that include storage are the responsibility of the user whereas SaaS activities are purely managed by service providers. In IaaS model, management of virtualization, servers, storage, and networking is done by service providers while the rest (applications, data, runtime, OS, and middleware) is managed. With Paas, the service providers is responsible for all activities except for data and application.


Benefits over Cloud Migration
There are several benefits of cloud migration for the users. In this way, Jamshidi et al., (2013) have stated that cloud migration has features of scalability. It is the intrinsic feature of appropriate server resources. Due to this feature of the cloud services many applications which requires discrete level of the server resources, choose for the scalability options provided by the cloud service provider. Along with this, Banerjee (2012) has depicted that cloud migration is a cost effective solution for the organizations. As per the massive growth in the technological infrastructures, the competition among Business Company has increased progressively so all the business companies are searching for the cost-effective solutions. Cloud service provides the service “Pay-As-You-Go billing model” which is profitable and cost effective for the organization as they need to pay for the resources consumed by its server. In the words of Bhattacherjee and Park (2014) cloud migration has feature of mobility as the users can access data anywhere across the world, which provides the ease environment to the users. The facility of the IP white listing assures the authorization to the user to access from anywhere across the globe. This feature is mostly available in every PaaS cloud services. Along with this, Rai et al., (2015) the feature of automation has improved the effectiveness of cloud migration for the users. The major problem of the cloud service provider is to cling to the backend server API’s updated. But one of the services provided by the cloud service providers “managed cloud migration” this application management will automatically update the overall system and API. Automation allows the cloud services providers to implement and test the applications quickly over the cloud. The complete implementation task could be carried out via the automated implemented process instead of the manually operating process without any performance and compatibility problems during execution. Rashmi and Sahoo (2012) have determined that there is a secure storage option, which improves the significance of cloud migration for the users. Organizations generally prefer to migrate towards the cloud environment because of the secured storage with reasonable and profitable operational cost. Similarly, depending upon the utilization of the resources and requirement the space availability can be increased or decreased without hindering the performance of the application and their uses. Along with this, Zhao and Zhou (2014) have argued that cloud providers have provided support and guidance to the business organizations in order to set up their migration process. The basic cloud migration process helps an organization to focus on the measures which would help in the determining successful migration if possible (Hardy, 2019). It helps the organization to judge whether the migration to the cloud environment is fit for its organization or not. Cloud security needs a discrete approach as compared to that of the on-premises security environment. It requires the deployment of the cloud firewall or web application firewall for the protection against threats and vulnerabilities.
Cloud computing Service providers
There are various companies which are providing cloud services and have a better performance which is found to be improving on a daily basis. The services provided by the cloud service providers are IaaS, PaaS and SaaS. Some of the cloud service providers are Amazon Web Services (AWS), Microsoft Azure, Google cloud platform, IBM cloud services, Adobe creative cloud, VMware, Red Hat, Salesforce, SAP, Oracle cloud, Navisite, Dropbox (Kachele et al., 2013). The good comparison among any four cloud service providers are shown in the below table:


These companies provide services like compute power, database storage, along with the facilities, which helps to integrate the business. Amazon introduced new tool which is Amazon web services (AWS) in the year of 2006. It provides services that enable end users to create and deploy application over the cloud. The services provided by the AWS are scalable, reliable and better. It provides better services to the customer as it charges for those facilities only which customers use in its cloud environment (Sala-Zarate and Colombo-Mendoza, 2012). It has a highly durable storage and highly effective and better performance database. It also provides all the three models services as discussed earlier like IaaS, PaaS and SaaS. It is one of the leading service provider companies. In order to get a better understanding about the migration process, the sections below discusses the migration processes and models adopted by different companies:
Cloud migration process: Amazon
Amazon’s subsidiary the Amazon Web Services (AWS) provide application programming interface (APIs) and on-demand cloud computing platforms under three service models: IaaS, PaaS, and SaaS. As part of the larger cloud computing services offered by the company under AWS is Amazon Elastic Compute Cloud (Amazon EC2), a cloud computing platform built around allowing users to rent virtual resources such as computers, servers, and software to run their own computers applications. Therefore, amazon EC2 services are based on infrastructure (IaaS) offered. The services allows the users to scale the applications by configuring virtual machine with instance availability of needed software as a resource. Therefore, allowing a user to instantly create, deploy and terminate services needed as well as increasing resources (storage and memory) as one’s demand increases, and paying for the services offered as needed in a pay-per-use model. Additionally, under Amazon Simple Storage Service (Amazon S3), the AWS offers scalable infrastructure object storage.

There are six phases of the migration process involved in the overall migration process of AWS. These phases are cloud assessment phase, proof of concept phase, data migration phase, application migration phase, leveraging the cloud phase and optimize phase. The cloud assessment phase includes the assessment cost, assess architecture and asses security. In addition, proof of concept phase includes learning of AWS, build a pilot and build support with organization and data migration phase includes leverage different storage options and migrate. Application migration phase includes forklift migration and hybrid migration strategy, leverage the cloud phase includes auto scaling, automation, elasticity and high availability. Optimize phase includes utilization, monitoring, efficiency, performance and re-engineering. In the words of Balalaie et al., (2016), the users need to establish a new process to ensure that they are migrating the appropriate projects. First, there should be a process of asking for information. If data leaks to the Internet, it will cause problems. Data that falls into this category should not go into the public cloud and can be transferred to the organization's private cloud. These phases provide the user to successfully migrate their data to the cloud environment of the AWS in a proper and secured manner. Similarly, while Microsoft is the private as well as the public cloud system which is generally used for the creating, testing, implementing and managing the application successfully. It provides the easiest platform to the developers and IT professionals to manage and organize their application and services to its environment.
Cloud migration process: Microsoft
Under Microsoft Azure as umbrella of it cloud computing services, Microsoft offers three cloud computing services namely Microsoft private, Microsoft azure, and Microsoft office 365. The three models are built on different cloud services models; SaaS, PaaS, and IaaS providing such services as programming languages, tools, and framework (Wilder, 2012). Among the services offered by Microsoft are Azure Sphere (security and communication platform for internet-based devices), Azure Web Sites (a platform for building, hosting, and publishing web apps), storage services (SDK APIs and REST, Blob services), Azure Data Explorer providing data exploration and analytics (Kotas et al., 2018; Philip, and Shah, 2019). Microsoft introduced Azure Application in the year 2010 providing different services in the cloud environment. Examples of the services are used to build, manage, and deploy applications over the cloud with the help of frameworks and tools. Azure gives the flexibility to deploy and manage virtual environment inside the virtual network (Pahl and Xiong, 2013). The complete migration process involved in the Microsoft azure process is: Assess, migrate, optimize and finally secure and manage.

Cloud migration process: Google LLC
The company Google introduced Google Cloud Platform (GCP) in the year 2008, it provides applications development and integration services to the end users through virtual machines in order to run workloads on the cloud. The facilities provided by the Google services are data analysis, data storage and machine learning. Google cloud platform run on similar framework as that used by the company for internal end-user products such as Gmail, Google search, and YouTube. Google compute engine provides an Infrastructure-as-a-Service, administrators are responsibility to configure and monitor the systems. Google app engine is used by developers for hosting and building applications in google data centers, hence PaaS services. Software-as-a-Service (SaaS), it is highly flexible for end users because they do not need to install any software on their accessing platform or machine (Menzel and Ranjan, 2012). In addition to this end users can use cloud-based software. In this context, the company itself provides different applications including Google G-Suite product which contains all the Google products such as Gmail, Google Docs, Google Photos, and YouTube etc. Furthermore, it is easy to use service for deploying and scaling web applications and services develop with Java, Python, and etc. In overall, there are five different phases involved in the Google cloud migration, which are assessed, pilot, move data, move applications and finally optimize them (Barrett, 2016).

Cloud migration process: IBM Cloud
IBM services are provided to fulfill the requirement of the customer and satisfy them with the possibilities of the opportunity to grow and improve operational efficiency (Kochut et al., 2011). It is able to serve better with the discrete field involvement like medical supply business, retailer, etc. The company through IBM cloud offer cloud services categorized under IaaS and PaaS. Under IaaS model, the company provide databases server, computing, and servers. The IBM Bluemix is a PaaS service offered by the company supporting several services like IoT, Mobile, Blockchain, and IBM Watson platforms that include programming language such as Java, Go, PHP, and Ruby on Rails for development, testing, and deployment of applications.
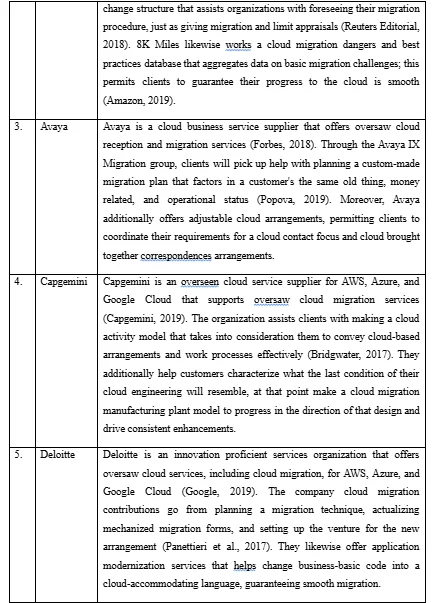
The migration process offered by the IBM services is mostly classified into four categories depending upon its types like based upon data migration, based upon network data migration, application-specific migration and real-time streaming ingest. In all these four aspects, it has defined the migration process and strategies in detail to help its customers. In summation, one can argue that the whole process of migrating the company’s operations to the cloud can be very challenging and demanding if the company is not prepared well for the same. As noted by Gholami et al. (2016) and Ward et al. (2010), the process might seem very easy but in really sense, factors such as time for deployment, projects and application compatibility as well as training the employees and the enterprise on the operation of the cloud has to be put into consideration. This is the very reason as to why there are companies which do management as well as migration process. The companies that include 2nd watch, 8k miles, Capgemini, Avaya, Deloitte, CloudReach, Infosys, and LogicWorks assist in migration and management process to organizations and individuals who wants to migrate basing their operations on cloud-based services.

Strategies to improve the effectiveness of cloud computing:
The users may face issue of theft and misuse of their data stored on cloud. In this way, it is essential for the users to use an appropriate strategy to improve the effectiveness and security of cloud computing process. In this way, Sun et al., (2012) have determined that the users must deploy multi-factor authentication instead of traditional password and username combination to protect their cloud account from hackers. Multi-factor authentication ensures that only authorized personnel is logging to cloud apps and accessing sensitive data. It is a cheapest technique of keeping data secure from the hackers. Along with this, Masud and Huang (2012) have stated that handing over user access rights not only assists to avoid an employee from unintentionally editing information that he or she isn't certified to access, but also protects them from hackers who have stolen an employee's credentials. Thus, the users can improve effectiveness of cloud computing account through managing their user access. According to Kuo (2011), data control is most recent object in cloud computing. Therefore, the users should optimize their storage environment to create data and assign data to right type of storage. They should also use WANOP to truly control flow of traffics among the distributed data center locations. As well as, load-balancing policies must be used to balance inside of data center and cloud. Along with this, Oliveira et al., (2014) have stated that the users should monitor the cloud computing in proper manner with use of authoritative management platform to create a proactive system to identify the issues in cloud. Modern cloud management platform can span different data locations, centers and workloads. Security issues has been a major factor in adoption of cloud based services. Despite research determining that security to data and information offered by cloud-based services is considerably higher compared to on-premises or other internal IT-infrastructure, slow migration to cloud-based services has been linked to higher cost of the security measures and technologies adopted by the services (Almorsy et al., 2016; Behl, and Behl, 2012). An investigation into cost-benefit analysis of information security technologies conducted by Zeng (2019) indicated that the benefits of implementing digital rights are limited by cost.
Chapter Summary:
From the analysis of literature review, it is summarized that cloud computing is a latest and better technology of securing the data. Cloud computing process have enabled the individuals as well as organizations to store their data in cloud form and access them at anytime and anywhere across the world. The cloud computing process has improved the efficiency of the organizations and well as users to manage their data in most effective manner. Thus, the cloud computing technique has improved the data management efficiency of the organizations with use of internet and other technological equipment. It is also analyzed that the On-premises, IaaS, PaaS and SaaS models have developed base for cloud computing technique and provided a cloud platform for the individuals and organizations to secure their data in most effective manner. It is also analyzed that there are four types of process model available in the cloud system i.e. On-premises, IaaS, PaaS and SaaS. These process models develop a base for the cloud computing process and enable the users to use cloud computing services in proper manner. In order to improve the effectiveness of cloud computing and improve security of cloud data the users must adopt multi-factor authentication process, authoritative management platform.
CHAPTER 3: IMPLEMENTATION- SYSTEMATIC MIGRATION MODEL
Cloud based migration strategy
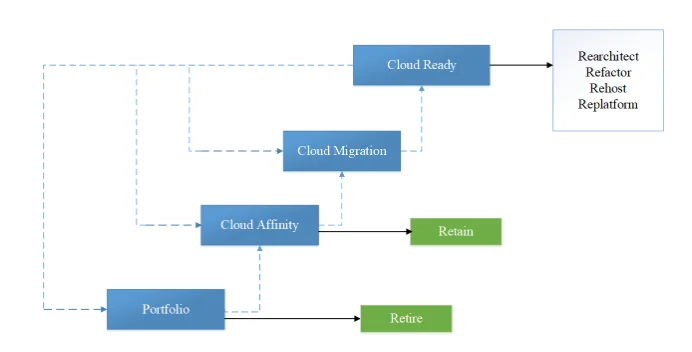
Before cloud migration key consideration factors include reliability of service providers, deployment method, time, and security. Building from the assertion given by Andrikopoulos et al. (2013), the digital transformation prioritised by organization to improve respective effectiveness and efficiency of operations and IT environment often end up being a challenging process. According to Zhao and Zhou (2014), for a successful migration, it demands an elaborate strategy and checklist for the process. In this case, the migration process was informed by assessment of risks involved. As such, a six-step approach is adopted that include risk identification, risk assessment, determination of migration strategy, evaluation of applications to migrate, create migration plan, and executing cloud migration. In essence, assessment that included identifying suitable applications for migration and determining best solutions for each applications gave a purview of successful migration (Figure 3.1). In this case, migration process involves transferring the applications, data, and database from on-premises to a cloud based services, as such, the services sought are infrastructure to host the applications, storage, and networking. Therefore, IaaS services deployed under combination of both private and public (hybrid) system.
Stage 1: Risk Identification and Assessment
For instance, categorising risks into levels; low, medium, and high as listed below:
CAT 1: Risk-Low- P2V/V2V re-host/lift and shift/App Re-install
CAT 2: Risk-Medium- Version upgrade/ architecture changes
CAT 3- Risk-High- OS and middleware change before modernisation
The risk identification encompasses assessing the risk involved in migrating to cloud-based services. Before adopting the cloud-services, such risk factors as unclear cloud strategy. It is worth noting that adopting unclear strategy ultimately leads to fail and possibly loss of data. Beforehand, such factors as strategy assessing with it clear or not, compatibility with existing architecture, risk of data loss, wasted cost, unwanted latency, and lack of control and visibility. Risk of migration goes beyond having a losing data and applications but also include security measures needed, offered, and available as well as cost of the security measures.
Stage 2: Migration Strategy
Migration strategy involves assessing the maturity of the technology available. After establishing maturity of network, it is essential to outline a plan that incorporates financial needs and implications as well as operational benefits. The developed roadmap encompasses capacity of the system and operating platform. Moreover, planning includes setting performance indicators CPU usage, responses time, memory usage, and availability.
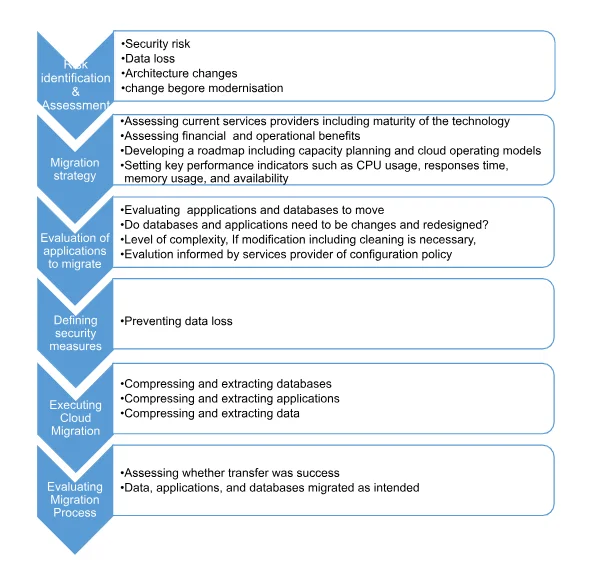
Stage 3: Evaluation of Applications and Databases to Migrate
Evaluation of the applications and migration strategy encompassed assessing architecture, assessing current services providers including maturity of the technology, and evaluating whether databases and applications need to be redesigned before migration. In addition to evaluating the level of complexity of modification and redesigning the process, other key factors to be considered include assessing configuration policy.
Stage 4: Security Measures
The security measures covered assessing design cloud platform is it was secure, scalable, extensible, manageable, and craft–gain agility and cost savings that optimises cloud virtues in relation of offered security measures. Adopting comprehensive migration strategy built around capability to transfer applications to secure and reliable cloud platforms while focusing on optimization and quality of services boosted success rate of migration.
Stage 5: Executing Cloud Migration
The execution part involves actual transferring the data, applications, and databases to cloud-based platforms. The process involved compressing the data, applications, and databases then extracting once successful transferred to the cloud.
Stage 6: Evaluating Migration Process
The evaluation stage encompasses assessing whether the whole process of migration was a success. It involves reviewing the goals, whether they were met, satisfaction level of meeting the objectives, are such measures as security and services offered as expected. In relation to service providers, the findings above found the migration process provided by the Amazon cloud service provider to be the best and effective than any other cloud service provider as it has different specified data migration provision for discrete sets of the data to be migrated in the cloud. Systematic migration model is basically used to migrate functional units of the organization as a whole. This means that the entire module, (databases, applications and the associated data) is moved to the cloud. In cloud-native era, putting up structure platforms that end-to-end industrialised, agile, and affordable as well as secure. For example, let's consider verifying a credit card through a shopping cart application. In the past, a virtual machine could load a credit card verification module to establish a network connection and call it, and then shut down instances that charge an hour. With fewer servers, one is able to call this function, and the cloud provider will take care of the rest and bill the resources that have been used in just a few milliseconds. This is a general cloud migration model where the entire functional unit or units of the organization are moved to cloud services systematically. The applications and other resources are not changed just like in shift and lift model; only their location is changed. In essence, this model is just re-hosting the applications and data. However, unlike in lift and shift model where everything is re-hosted, this model only re-hosts selected applications and databases that make a functional unit and not the entire data center. For instance, the organization can choose to re-host finance, marketing and human resources modules alone depending on their complexity. This general migration model involves moving a duplicate copy of the data in categories. The data and applications are categorized depending on priority on which to be moved first and then compressed to a single file. The purpose to compressing is to ensure only related databases and applications are migrated. If the migration is done before compressing, it is possible to include other data that do not relate to the ones being moved. It is also possible to leave behind key applications or databases from the group being migrated. Moving compressed applications is also easier and timely and more secure at the same time. In this model, all the databases and applications will be divided into smaller chunks and compressed individually. In this context, every individual file will be checked and migrated to the cloud provider, during this migration any other error occurred will be rectified. The original applications and databases will remain on premise. Once all the necessary resources have been moved and extracted, the connection link is shifted from the local server to the set cloud server.
Advantages
During the migration, the operation of the organization is not affected since only a duplicate of the resources and data is migrated.
The model does not require a lot of planning because there is no code alteration.
Because the databases and applications are compressed before they are migrated, it is less likely to leave some of the databases and applications.
This migration model is relatively cheaper compared to refactoring and re-platforming.
This migration model is 100 % error free, because we will be able inspect and analyze all the applications and databases files before migrating to the cloud.
This model gives us the scope to identify any errors after the migration which enables us to evaluate and fix the errors.

Disadvantages
The applications are compressed before they are moved and have to be extracted once in the cloud.
It requires technical skills in order to compress and extract the resources during the migration.
The fact that the categories are moved in shifts takes more time.
Compared to other models this model is bit slow.
Despite the fact that the model has a number of disadvantages, it is still the most appropriate migration model. This is because it is done in a more secure environment and only performed to individual functional units. This makes it more affordable to use cloud services and no risky to the organization. Unlike other models which migrate various applications and databases or the entire data center to the clouds, this model only moves a duplicate of the resources. This makes it more secure as the original resources and applications will be in place even if an error occurs during the migration. An error occurring during the migration does not affect the other resources since the migration of databases and applications is done separately. Migrating the data and applications in bits allows one to gain experience in the process. This means the following bit will be moved faster and with fewer errors. The organization only shifts to use the resources in the cloud once they have been deployed and tested to work efficiently.
CHAPTER 4: CONCLUSION
Conclusion
From the analysis of literature review and case study of AWS, it is concluded that cloud migration is an effective and attractive process through which the individuals as well as the organizations make transmission of data applications and other business elements to the cloud computing environment. It is a latest technological advancement for management of data in safe and secure manner. It is observed that the main cloud migrations are like lift and shift, shift to Software-as-a-Service (SaaS), application refactoring and replatforming. Each of the cloud migration has a different way of performing and discrete strategies to carry out the task. Migration of data to cloud allows and facilitates the organizations to grow of their business. Cloud migration of data and resources has developed flexibility in business operations. Major cloud service providers are AWS, Microsoft, Google, and IBM. The benefits of cloud computing has encourages the individuals as well as the organizations to migrate their data and applications on cloud. From the analysis of research findings, it is summarized that AWS is most reliable and adopted cloud computing platform. It’s a largely accepted cloud platform with offering of fully featured services from the Data centers internationally. AWS comprises an assortment of platform as a service (PaaS), infrastructure as a service (IaaS) and packaged software as a service (SaaS) offerings. AWS has benefited to several large companies from considerable cost saving in their IT operations, improvements in business algidity, productivity and operational flexibility. AWS has comprised to move workloads from a hosting facility, on-premises environment and other public cloud. AWS has enabled the users to migrate their workloads such as websites, applications, storage, database, virtual or physical servers and whole data centers on cloud. The services offered by AWS such as storage, compute, database, networking, analytics, developer tools, mobile, IoT, management tools, enterprise and security applications has improved the performance of the organizations to manage their business operations in more productive manner.
Recommendations
Based on research findings, it is recommended that the users should analyze their needs properly before use and selection of a cloud service provider. The analysis of needs will enable the users to select an appropriate cloud service provider. Experts should also be utilized in determining the best migration model to use when the organization is shifting from using local server to using cloud servers. During this process, it is important to only move relevant applications and data. This will help in reducing the costs of using the cloud services. However, the company should always keep a copy of the original applications or data before the migration. This will be very useful in case an error occurs during the migration. Apart from this, the users should follow all of the instructions and security measures to secure their data and information on cloud computing. As well as, the users should deploy multi-factor authentication instead of traditional password and username combination for protection their cloud account from hackers.
Research limitations and future implications:
The research study mainly focuses on AWS cloud migration so that it research do not provide information about other cloud services. In addition, the research study is conducted on secondary data or case study, which may restrict to reliability of the research outcomes. In order to improve the reliability of research outcomes and significance of the research primary data can also be considered in the research process for collection of more reliable data. In addition, the feasibility of research study can be improved through proper discussion of other cloud services (Microsoft Azure, Google Cloud, Amazon Web Services, and IBM Cloud).
Reference
- Ahmad, A., and Babar, M. A. (2014) A framework for architecture-driven migration of legacy systems to cloud-enabled software, In Proceedings of the WICSA 2014 Companion Volume (pp. 1-8).
- Alharthi, A., Wills, G., Alassafi, M., Walters, R. and Alzahrani, A., 2017. Critical success factors for cloud migration in higher education institutions: a conceptual framework. Int. J. Intell. Comput. Res.(IJICR), 8(1), pp.817-825.
- Aljabre, A., 2012. Cloud computing for increased business value. International Journal of Business and social science, 3(1).
- Almorsy, M., Grundy, J. and Müller, I., 2016. An analysis of the cloud computing security problem. arXiv preprint arXiv:1609.01107.
- Andrikopoulos, V., Strauch, S. and Leymann, F., 2013. Decision support for application migration to the cloud. Proceedings of CLOSER, 13, pp.149-155.
- Armbrust, M., Fox, A., Griffith, R., Joseph, A.D., Katz, R., Konwinski, A., Lee, G., Patterson, D., Rabkin, A., Stoica, I. and Zaharia, M., 2010. A view of cloud computing. Communications of the ACM, 53(4), pp.50-58.
- Arora, I. and Gupta, A., 2012. Cloud databases: a paradigm shift in databases. International Journal of Computer Science Issues (IJCSI), 9(4), p.77.
- Balalaie, A., Heydarnoori, A., and Jamshidi, P. (2016) Microservices architecture enables devops: Migration to a cloud-native architecture, Ieee Software, 33(3), pp. 42-52.
- Behl, A. and Behl, K., 2012, October. An analysis of cloud computing security issues. In 2012 world congress on information and communication technologies (pp. 109-114). IEEE.
- Bhardwaj, S., Jain, L. and Jain, S., 2010. Cloud computing: A study of infrastructure as a service (IAAS). International Journal of engineering and information Technology, 2(1), pp.60-63.
- Bhoyar, R., and Chopde, N. (2013) Cloud computing: Service models, types, database and issues, International Journal of Advanced Research in Computer Science and Software Engineering, 3(3).
- Chang, S.E., Chiu, K.M. and Chiao, Y.C., 2015, July. Cloud migration: Planning guidelines and execution framework. In 2015 Seventh International Conference on Ubiquitous and Future Networks (pp. 814-819). IEEE.
- Cito, J., Leitner, P., Fritz, T., and Gall, H. C. (2015) The making of cloud applications: An empirical study on software development for the cloud, In Proceedings of the 2015 10th Joint Meeting on Foundations of Software Engineering (pp. 393-403).
- Dillon, T., Wu, C. and Chang, E., 2010, April. Cloud computing: issues and challenges. In 2010 24th IEEE international conference on advanced information networking and applications (pp. 27-33). Ieee.
- Freet, D., Agrawal, R., John, S., and Walker, J. J. (2015) Cloud forensics challenges from a service model standpoint: IaaS, PaaS and SaaS, In Proceedings of the 7th International Conference on Management of computational and collective intElligence in Digital EcoSystems (pp. 148-155).
- Hsu, P.F., Ray, S. and Li-Hsieh, Y.Y., 2014. Examining cloud computing adoption intention, pricing mechanism, and deployment model. International Journal of Information Management, 34(4), pp.474-488.
- IBM, 2018. IBM Services Cloud Modernization And Migration For IBM Cloud Private (ICP). IBM Services. IBM.
- Kachele, S., Spann, C., Hauck, F. J., and Domaschka, J. (2013) Beyond IaaS and PaaS: An extended cloud taxonomy for computation, storage and networking, In 2013 IEEE/ACM 6th International Conference on Utility and Cloud Computing (pp. 75-82). IEEE.
- Kotas, C., Naughton, T. and Imam, N., 2018, January. A comparison of Amazon Web Services and Microsoft Azure cloud platforms for high performance computing. In 2018 IEEE International Conference on Consumer Electronics (ICCE) (pp. 1-4). IEEE.
- Lim, K. S. S., and Hong, S. Y. (2010) Development of an effective double-moment cloud microphysics scheme with prognostic cloud condensation nuclei (CCN) for weather and climate models, Monthly weather review, 138(5), pp. 1587-1612.
- Madhyastha, T. M., Koh, N., Day, T. K., Hernández-Fernández, M., Kelley, A., Peterson, D. J., and Grabowski, T. J. (2017) Running neuroimaging applications on amazon web services: how, when, and at what cost?, Frontiers in neuroinformatics, 11, pp. 63-69.
- Mohammed, F., Ibrahim, O. and Ithnin, N., 2016. Factors influencing cloud computing adoption for e-government implementation in developing countries. Journal of Systems and Information Technology.
- Pahl, C., and Xiong, H. (2013) Migration to PaaS clouds-migration process and architectural concerns, In 2013 IEEE 7th International Symposium on the Maintenance and Evolution of Service-Oriented and Cloud-Based Systems (pp. 86-91). IEEE.
- Philip, J. and Shah, D., 2019. Implementing signature recognition system as SaaS on microsoft azure cloud. In Data Management, Analytics and Innovation (pp. 479-488). Springer, Singapore.
- Rani, D., and Ranjan, R. K. (2014) A comparative study of SaaS, PaaS and IaaS in cloud computing, International Journal of Advanced Research in Computer Science and Software Engineering, 4(6).
- Sala-Zarate, M., and Colombo-Mendoza, L. (2012) Cloud computing: a review of PAAS, IAAS, SAAS services and providers, Lámpsakos, (7), pp. 47-57.
- Sun, D. W., Chang, G. R., Gao, S., Jin, L. Z., and Wang, X. W. (2012) Modeling a dynamic data replication strategy to increase system availability in cloud computing environments, Journal of computer science and technology, 27(2), pp. 256-272.
- Ward, C., Aravamudan, N., Bhattacharya, K., Cheng, K., Filepp, R., Kearney, R., Peterson, B., Shwartz, L. and Young, C.C., 2010, July. Workload migration into clouds challenges, experiences, opportunities. In 2010 IEEE 3rd International Conference on Cloud Computing (pp. 164-171). IEEE.
- Zeng, W., 2019. A methodology for cost‐benefit analysis of information security technologies. Concurrency and Computation: Practice and Experience, 31(7), p.e5004.
- 24/7 Customer Support
- 100% Customer Satisfaction
- No Privacy Violation
- Quick Services
- Subject Experts



