Importance of Customer Data Protection
Introduction:
According to Carrie Hunt, the president and CEO of the Council of Better Business Bureaus claim that protecting your customer’s personal data against mishandling needs to be a top priority of every business that collects customer information. It is because customers needs to trust that their private, personal information is safe with a business before they can trust doing business with it. In the current business world, the highest probability of problems that can happen and causes significant effect is not just about confidentiality, but it is usually around the integrity and availability aspects. The PCI Security Standards Council (PCI SSC) defines a series of specific Data Security Standards (DSS) that are relevant to all merchants, regardless of income and credit card transaction volumes.
Description of the Risks:
According to Segovia (2018), risk is the potential of a given threat that exploits vulnerabilities of an assets and thereby cause harm to an organization. Basically, if there exist a threat and vulnerability, then there is a risk results in an impact. Impact in this case is the result of an information security incident, caused by a threat, which affects assets. Taylor et al (2008) claim that it is important to combine the potential impact and likelihood that the threat can be carried out when assessment of risk for any threat. Merchants who accept credit card and keep cardholder data, are facing a high risks regarding these data, and they must ensure their customers are transacting securely. Cardholder data refers to any information contained on a customer’s payment card (credit card number, cardholder name, expiration date and security code (CSC) as depicted by PCI Security Standards Council (2008). These data are always targeted by criminals, who actively seek ways to steal this information to commit fraud. Taylor et al (2008) claim that many cases of fraud related to client’s credit card information happen because a virtual door is left open for criminals. For example, browsing the Internet on a computer where sensitive data is stored is one way that could enables criminals to steal this information. Therefore, knowing the risks is a good way to prevent any careless mistakes. In case of merchants do not need to store any cardholder data, a stronger protection is provided automatically by having eliminated a key target for data thieves. However, in this case, the organization stores the cardholder data on the server to meet the needs of its business. So, the probability of risk and impact increase, consciously the responsibility of protecting the data become higher. Some of these risks are mentioned below:
Continue your journey with our comprehensive guide to Data Protection and Cybersecurity Strategies.
Keeping the default settings which usually is well-known and easy to guess, such as the default passwords for Operating Systems, Database Store Management systems, applications or other programs, make the probability of exploited it to compromise the systems high. Unrequired sensitive data, such as the magnetic strip or full contents of the chip, the PIN (personal identification number) or the CVN (card verification number). Additionally, storing the necessary data without encryption or storing the cryptographic keys unsecurely would make the data readable and usable by criminal hackers. Sensitive data if not encrypted during transmission over a public network such as the internet, wireless technologies (e.g. Bluetooth), makes these data readily available to malicious individuals. Furthermore, authentication protocols (for example, TLS, IPSEC, SSH, etc.) have vulnerabilities known to hackers, and they can exploit it for accessing information or even diverting the information flowing across the network, because of these protocols are not configured with their secure versions. Also, use a messaging platform such as emails, instant messengers for chat, excetra, to send unprotected PANs (Personal Account Numbers) or in plain text format, resulting the entire packets passing through the network can be monitored, and any information that is transmitted in clear text format can be seen. Antivirus mechanisms not running actively or disabled without formally authorized consciously, the server affected by malware (e.g. worms, viruses and Trojans), subject the server to be completely damaged or failed which impact the availability. Vendor-supplied security patches have not installed on all system components, or not deploy within a month of their release. Also, Web application firewall have not installed, web applications have not develop based on secure coding guidelines or custom application code has not checked to identify any coding vulnerabilities, which may allow criminals to access PAN and other cardholder data. Authorized accounts and user privileges can be exploited by an employee to gain access to a system if the access to cardholder data unlimited. This impact the confidentiality and integrity, which cause a lack of trust on the part of clients and impact the organization’s reputation. Access to system components and password policies for staff members and users are not controled. For example, enabling remote access accounts when not in use (24/7 access), or not using a multi-factor authentication solution such as token devices, smart cards, biometrics, public keys for all remote access sessions, passwords readable for all system components both in storage and during transmission without any cryptography.

Description of PCI-DSS Standard:
Payment Card Industry (PCI), was founded in the year 2006 with the purpose of making cardholder data security higher and more trusted depict BigCommerce (n.d). It is by setting certain measurement, which applies to all entities involved in (CHD) Cardholder data, (SAD) sensitive authentication data, and (PIC) payment card processing such as processors, merchants, acquirers, server provider and issuers. Also, compliance with these standards is obligatory. Moreover the following list as depicted by the Itgovernance (n.d) is the PCI standars;
Build and maintain a secure Networking and System. Protect Cardholders Data. Maintain a vulnerability management program. Implement strong access control measures. Regular monitor and test networks. Maintain an information Security policy.
These standards could be achieved by applying 12 requirements which will be discussed in detail later in the report. ISO/IEC 27001:2013 requirements are set to be generic so that it applies to all organizations, regardless of type, size or nature, therefore it is not mandatory for a company. ISO/IEC 27001 (2013) gives a clear overview of how to establish, implement, and maintain the requirements, and how to continually improve the information security management system within the context of the organization. In addition, it includes the requirements for the assessment and treatment of information security risks tailored to the needs of the organization. According to Segovia (2018), there are several similarities between both standards, for example the continuous improvement of ISO 27001, that is, the best general security controls of ISO 27002, and the best security controls regarding credit cards in PCI-DSS.” Another example of ISO/IEC 27001 according to Marsella (2018) could be Cryptography and Communications security which are related to requirement 4 of PCI-DSS). Lastly, PIC-DSS and ISO/IEC are very important since they protect the users information and help to minimize the risks asserted by PCI Security Standards Council (2008). For example, storing unneeded sensitive data such as the PIN card، is dangerous since hackers could try to steal this information, therefore having these standards is a good way to protect it.
Meeting the Requirements:
First of all ccording to Whitelegg (2014), requirement 6 which is develop and maintain secure systems and applications was the first requirement to be be run, and this is because it could help to decide which Ubuntu is more safer to continue the rest of the requirement with. Therefore, vulnerability scanner from tenable networks Nessus has been used to test Ubuntu VMs: ubuntu 1 and ubuntu 10, to know which one has minimal weaknesses and vulnerabilities. The Nessus scanner has shown that Ubuntu 1 has more vulnerability with more than one critical vulnerability as it is shown in (Figure 1). Where as (Figure 2) shows Ubuntu10 with less vulnerability, which are only info, which shows that Ubuntu 10 is safer. Therefore, Ubuntu 10 has been chosen to store the payment card data instead of Ubuntu 1.
In order to make this server more secure several approaches have been taken. First, software update need to be checked to verify that benefit from the latest security patches has obtained (Figure 3). Also, any pre-installed game applications have been omitted. These games should not be installed in the server, because it could open up new points of vulnerability which can be exploited by a threat, which impact the information assurance.
Secondly, to promote security, compliance with the 12 requirements of Payment Card Industry Data Security Standard (PCI DSS) is vital as emphasized in the PCI Security Standards Council (2008). The requirements and the approach which have taken to meeting these requirements for Ubuntu 10, are meant to reduce the vulnerabilities and protect cardholder data are illustrated below:
1- For maintain a secure network, requirement 2 is considered as follows:
Requirement 2: Does not use vendor-supplied defaults for system passwords and other security parameters.
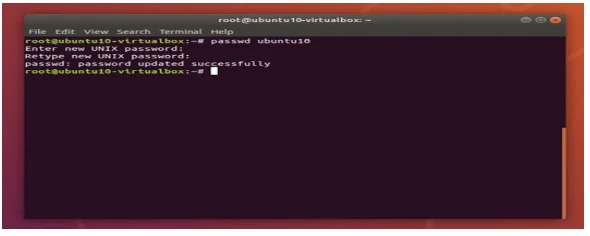
Default password are often used by malicious individuals both external and internal, also default settings to compromise the system, These default passwords and settings are well known by hacker communities, therefore meeting requirement 2 increases the security and make the system less vulnerable (PCI DSS Compliance2, n.d). Note that Ubuntu10 has a default password which is ubuntu1 and to meet requirement 2 this password needed to be changed to a more secure setting.In that case, the password has been changed to “Abdullah@887”. Changing this password will leave the system with less vulnerable to attacks.
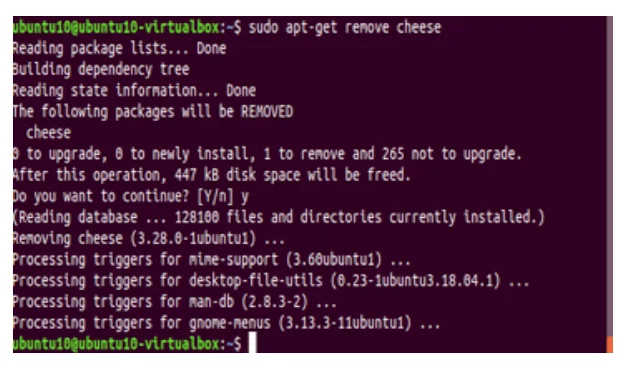
Secondly, all unnecessary default accounts has been deleted, so that the system become more secure.

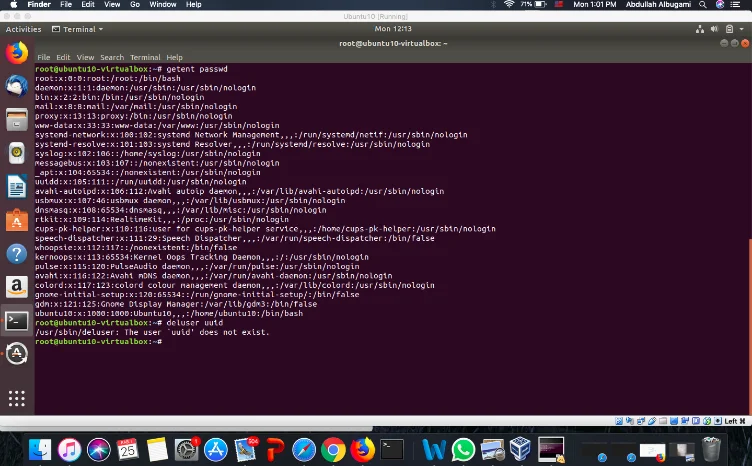
According to Boelen (2016), Linux Standard Base Core Specification, Generic Part, website, the system only requires root, bin, and daemon, any other are optional users. Therefore, an articule Refspecs.linux-foundation (n.d) depict that all the unnecessary accounts exting are deleted so that hackers can not have access through them. Lastly, to ensure the network security is strong, the network security will be provided to professionals who will manage it, to make it as secure as possible (PCI DSS Compliance2, n.d).
2- For protect cardholder data, requirements 3 and 4, which both focus on this area of data security is considered as follows:
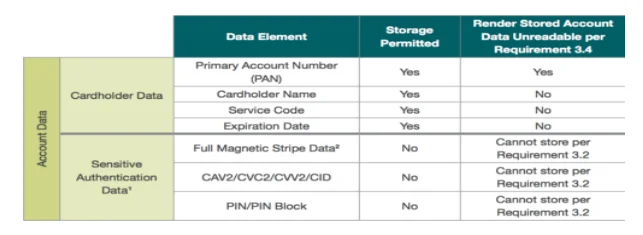
Requirement 3 is divided into six-sub requirements, all about safeguarding stored cardholder data. The content of these sub requirements has summarized in next lines. Cardholder data should not be stored unless definite necessities to meet the needs of the business.While sensitive authentication data such as the magnetic stripe, full contents of the chip, the PIN (personal identification number) or the CVN (card verification number) must never be stored after authorization even if encrypted as figured out by Semafone (n.d). As sensitive data is very important to malicious individuals, they can use it to make counterfeit payment card and create fraudulent transactions.
(Figure 10) illustrates which data are permitted to storage and which data must be protected, (Figure 11) shows the type of data on payment card.
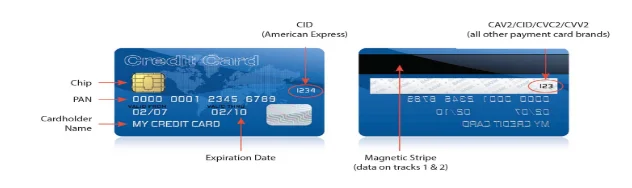
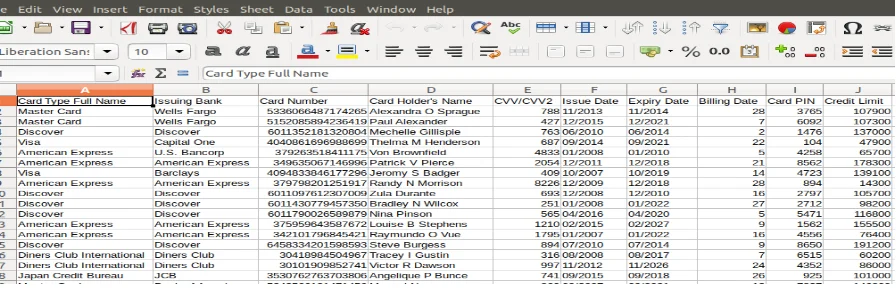
Additionally, Personal Account Number (PAN) have to masked when display of Personal on payment card receipts, computer screen, faxes, etc takes place. The maximum number of digits that should be displayed are the first six and last four digits needed. Special circumstances are provided to authorized people with a legitimate business whose need to see more than this if necessary. Also, the stored PAN must be unreadable anywhere it is stored by using techniques such as encryption, truncation or hashing. Meeting this requirement according to BigCommerce (n.d) helps to preserving the cardholder data securely. As these data is very important to malicious individuals, they can use it to make counterfeit payment card and create fraudulent transactions. All payment card data are provided in form of ‘.csv file’. However, this file stores a sensitive authentication data, which inconsistent with the requirement 2(Figure 11). Therefore, the file is amended to protect cardholder data by deleting any sensitive data (CVV/CVV2, Card PIN), and unassay data (Issue Date, Credit Limit, Expiry Date). Now, the file just stores the permeated cardholder data (PAN, Card holder name) (Figure 12).
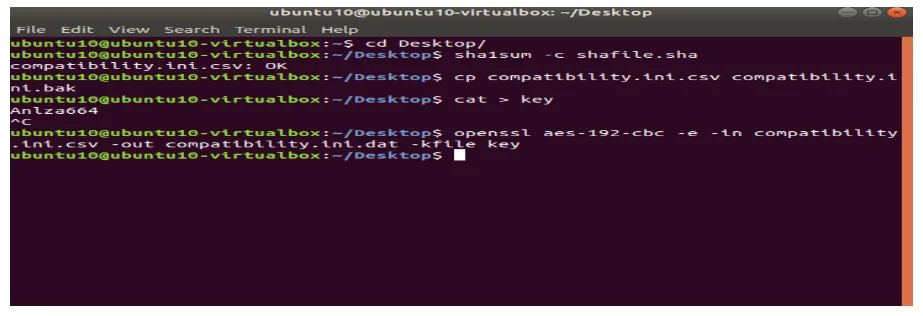

Requirement 4: Encrypt transmission of cardholder data across open, public networks.
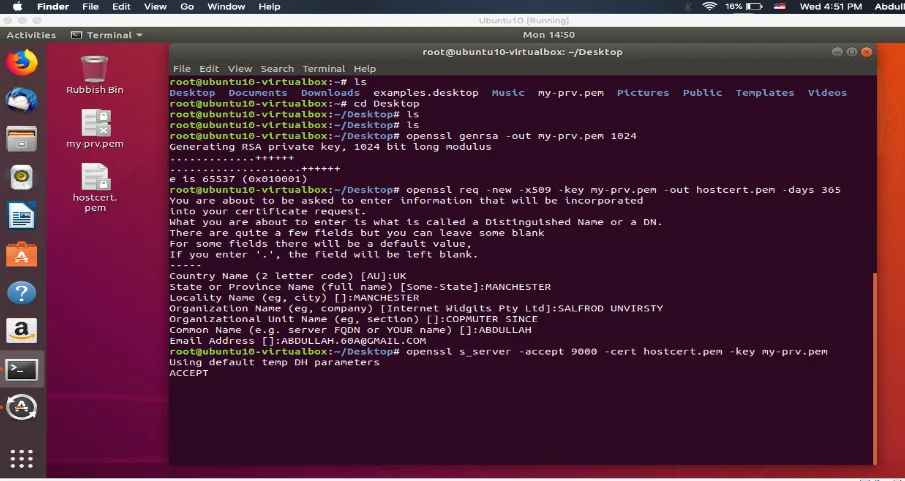
Malicious individuals can easily access sensitive information during transmission over networks if not encrypted accrding to an acticle PCI DSS Compliance4 (n.d). Therefore, all the sensitive information must be encrypted. To allow a secured connection between a server and a client, TLS will be demonstrated
First a private key has been created.
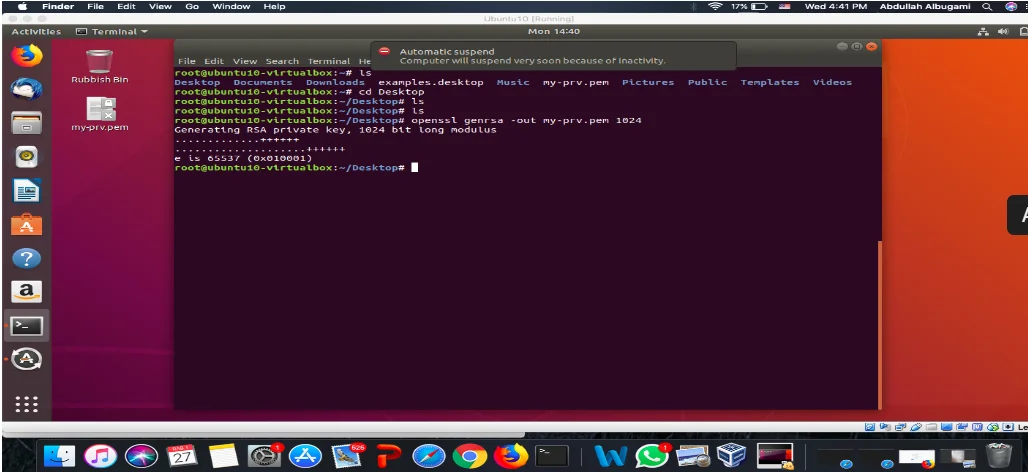
Second a certificate has been created.

Lastly a test server.
3- For maintain a vulnerability management program, requirements 5 and 6 has taken into account as follows:
Requirement 5: Use and regularly update anti-virus software or programs
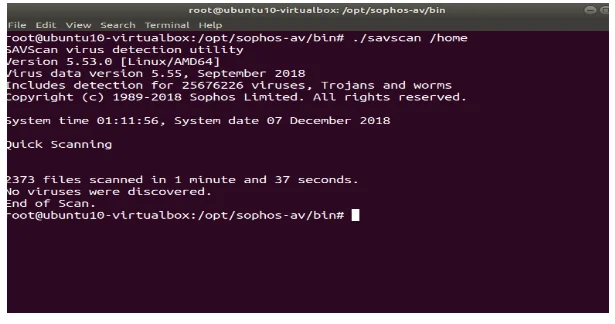
An article PCI DSS Compliance5 (n.d) depict that finding vulnerabilities continuously in an organization’s payment card system, is a critical process to protect the system against malware threats. Malware such as Trojans, worms, spyware, rootkits, adware, excetra, penetrate the network via storage hardware, employees’ e-mail and any another internet usage. Therefore, according to Sonmez (n.d) in a blog depict that anti-virus software must be installed on all systems affected by malware to protect it from any threats. Additionally, as new threats and viruses emerge continuously, the software must be actively updated on frequent occasions. The update process can prevent any malware entities from attack and exploit the system to obtains the important data. To meet this requirement, Sophos Anti-Virus has installed (Figure 20). This software disallowing harmful software to be downloaded, detects and cleans up viruses (Trojans, worms, spyware, adware), and updates regularly.

savscan (the command-line scanner used in Sophos Anti-Virus) has run as test for “home directory” and the result was no virus discovered (Figure 21).
4- For implement strong access control measures, requirements 7, 8 and 9 which are dealing with this area of data security has considered as follows:
Requirement 7: Restrict access to cardholder data by business need-to-know
The concept of 'need to know' is very important to limit the access to cardholder data. Users should only be given the minimum amount of privileges which are necessary to perform their required tasks (least privilege). Also the default setting should be set to “deny all” unless specifically allowed depict article PCI DSS Compliance7 (n.d). This is because unlimited access to data and unnecessary privileges result in increasing the attack opportunities, where attacks mostly come from within the organization. There are various technologies can be used for performing access control, for example, group policies, account restrictions and access control lists.
Requirement 8: Assign a unique ID to each person with computer access
Before enabling users to access to system components or cardholder data, Wilder (2017) claim that it is essential to assign a unique identification (ID) to each individual instead of sharing one ID. Authentication helps to hold each user accountable for their actions. Passwords and other authentication methods could be exploited by attacker If there are no security implemented at the point of entry, during transmission, or while in storage outlined in the the article PCI DSS Compliance8 (n.d). Therefore, both of identify and authenticate function help to protect the system components. Moreover, any changes to the ID such as modification, addition and deletion should be controlled in order to verify of all accounts that access a system. Lastly, it is important to check all accounts and note any inactive user accounts within 90 days and act to remove it or disable it. Hackers can easily access and make changes on these accounts without being noticeable for a long time.

Requirement 9:Restrict physical access to cardholder data
Requirement 9 state that any physical access to cardholder data are restricted by anyone who is physically present on the entity’s premises, unless the person was authorised, and this requirement is taken care of by a professional security team. An acticle edited by Solarwindsmsp (n.d), affirms that the security team must ensure there is appropriate use of facility entry controls, also give each users a unique ID, and a visitor log with physical token will be used to identifies visitors as researched and exemplified in PCI DSS Compliance9 (n.d). Furthermore the security team will physically secure all media, and destroy it when it is no longer needed for business or legal reasons. This is really important to ensure that the data stored is safe and no one can easily physically access it.
5- For regularly monitor and test networks, requirements 10 and 11 are applied :
Requirement 10: Track and monitor all access to network resources and cardholder data.
Requirement 10 state that tracking and monitoring all access to network resources and cardholder data is needed. It could be achieved by a security network team which will take care of the network, and this is important since it could help to prevent, detect, and minimize the impact of data compromise according to the article PCI DSS Compliance10 (n.d). Also having system activity logs help to determine the cause of the compromise, without it, it is very difficult and could be impossible to do so.
Furthermore, the server provider need to have the following requirement;
firewall IDS/IPS FIM Anti-virus Physical access control Logical access control Audit logging mechanisms. Segmentation controls ( if used).
Requirement 11: researchers and hackers tend to discover vulnerabilities and there is different method to do so as shown in requirement 6. Needless to say, systems should frequently be tested and updated to ensure security control to reflect a changing environment. Another common example which could be used for regular testing is Black-box testing asserted in the article PCI DSS Compliance11 (n.d). Lastly, the network is expected from the security network team to do a PAN test after every 3 months to ensure the network is safe.
Conclusions and recommendations:
The PCI standards are defined and managed by the Security Standards Council (SSC), while compliance to them is enforced by the credit card companies.
References
Taylor A., Alexander D., Finch A., and Sutton D. 2008. Information Security Management Principles. An ISEB Certificate. Second Edition. Publisher; The British Computer Society. pp. 1-31
- 24/7 Customer Support
- 100% Customer Satisfaction
- No Privacy Violation
- Quick Services
- Subject Experts



