IPv6 Addressing Scheme Overview
Workshop 1
IPV6 addressing scheme in terms of their scope, structure and type.
The IPv6 addressing scheme denotes the numerical label that is essentially utilized in the identification of the network interface of either the network node, or the computer attached to IPv6 computer network. The IP addresses are fundamentally transmitted across the fields with the packet header indicating the source as well as destination of every network packet. It is worth noting that the IP address linked to the destination is utilized in making decisions regarding routing the IP packets especially to the rest of the networks (Kumar and Tomar 2020). Most of the IP addresses are essentially classified via primary addressing as well as routing methodologies that yield three fundamental schemes. The three include anycast addressing, unicast addressing and the multicast addressing.
Across all the schemes, it has to be recalled that IPv6 addresses constitute of 128 bits, which are essentially bisected for the purposes of developing a boundary between the host number and the network number. Subsequently, the 64-bits attached to the network number would still be divided into the subnet ID and the routing prefix. In the case of the Unicast structure or type of IPv6 addressing, attention is given to the global and link-local scope. This implies that the loopback address and the link-local address carry with them the link-local scope, which is essentially applied in the single network link thereby leaving the rest of the addresses globally routable (Goyal and Arora 2017). Therefore, packets with the destination or the source may not be routed to the separate scope. Unlike the unicast, the anycast structure or type of the IPv6 have most of the addresses that are synthetically identical and remain similar to the unicast addresses. The only difference lies with the administrative function. Finally, the multicast would have four least significant bits linked to the second address octet define the significant address scope.
How a EUI-64 address is constructed.
EUI-64, also known as Extended Unique Identifier, is essentially regarded as an approach in which the IPv6 host addresses can automatically be configured. In this context, the IPv6 device would make use of the MAC address, attached to the interface, for the purposes of generating the unique 64 bit interface ID. This would happen despite the fact that the interface ID is commonly 64 bit and the MAC address is essentially 48 bit (Abdullah 2019). The process begins by first separating the MAC address into two separate 24-bits with one side taking the Organizationally Unique Identifier, denoted as OUI, and the remaining side capturing the NIC specific. The next step considers the inversion of the seventh bit, which is identified as the local or the universal bit.
Workshop 2
Workshop Answers
Build the Network and Configure Basic Device Settings
Configure the host name as shown in the topology.
Configure the IPv4 addresses on the router as shown in the topology.
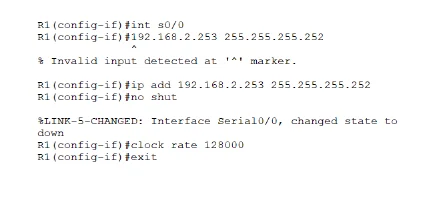
Set the DCE serial interfaces with a clock rate of 128000.
Clock rate:

Configure dynamic routing on the routers.
Configure RIPv2 for R1.
R1(config)# router rip
R1(config-router)# version 2
R1(config-router)# network 192.168.0.0
R1(config-router)# network 192.168.1.0
R1(config-router)# network 192.168.2.252
R1(config-router)# no auto-summary
Configure RIPv2 on R2.
RIP: R1
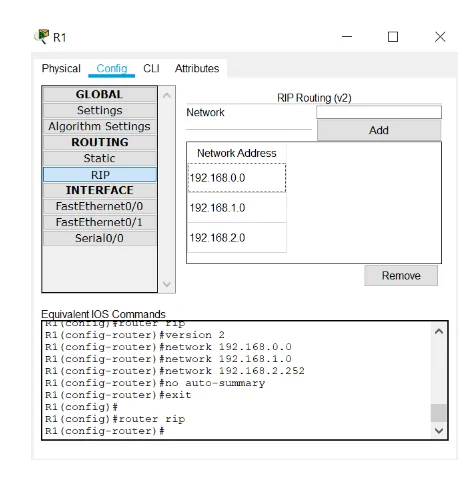

RIP: R1 configuration

Verify network connectivity between the routers.
If any pings between routers fail, correct the errors before proceeding to the next step. Use show ip route and show ip interface brief to locate possible issues.

Interface brief

Verify the host PCs are configured for DHCP.
Configure a DHCPv4 Server and a DHCP Relay Agent
To automatically assign address information on the network, you will configure R2 as a DHCPv4 server and R1 as a DHCP relay agent.
Configure DHCPv4 server settings on router R2.
On R2, you will configure a DHCP address pool for each of the R1 LANs. Use the pool name R1G0 for the G0/0 LAN and R1G1 for the G0/1 LAN. You will also configure the addresses to be excluded from the address pools. Best practice dictates that excluded addresses be configured first, to guarantee that they are not accidentally leased to other devices.
Exclude the first 9 addresses in each R1 LAN starting with .1. All other addresses should be available in the DHCP address pool. Make sure that each DHCP address pool includes a default gateway.
On PC-A or PC-B, open commands prompt and enter the ipconfig /all command. Did either of the host PCs receive an IP address from the DHCP server? Why?
No. Due to the fact that the DHCP server is not configured
Configure R1 as a DHCP relay agent.
Configure IP helper addresses on R1 to forward all DHCP requests to the R2 DHCP server.
On the lines below, write the commands necessary to configure R1 as a DHCP relay agent for the R1 LANs.
FastEthernet0 Connection:(default port)
Connection-specific DNS Suffix..:
Physical Address................: 000A.F347.3CCD
Link-local IPv6 Address.........: FE80::20A:F3FF:FE47:3CCD
IP Address......................: 192.168.0.3
Subnet Mask.....................: 255.255.255.0
Default Gateway.................: 192.168.0.254
DNS Servers.....................: 192.168.0.1
DHCP Servers....................: 192.168.0.1
DHCPv6 IAID.....................: 21780
DHCPv6 Client DUID..............: 00-01-00-01-28-94-C7-9A-00-0A-F3-47-3C-CD
Bluetooth Connection:
Connection-specific DNS Suffix..:
Physical Address................: 0060.2FE7.A372
Link-local IPv6 Address.........: FE80::260:2FFF:FEE7:A372
IP Address......................: 0.0.0.0
Subnet Mask.....................: 0.0.0.0
Default Gateway.................: 0.0.0.0
DNS Servers.....................: 0.0.0.0
DHCP Servers....................: 0.0.0.0
DHCPv6 Client DUID..............: 00-01-00-01-28-94-C7-9A-00-0A-F3-47-3C-CD

Verify DHCP services and address leases on R2.
On R2, enter the show ip dhcp binding command to view DHCP address leases.
Portfolio task - Along with the IP addresses that were leased, what other piece of useful client identification information is in the output?
__ R2>enable
R2#show ip dhcp binding
IP address Client-ID/ Lease expiration Type
Hardware address
192.168.1.10 000B.BE84.7001 -- Automatic
192.168.0.10 000C.CF35.27D9 -- Automatic R2#________________________________________________________________________________
On R2, enter the show ip dhcp pool command to view the DHCP pool settings.
Portfolio task - In the output of the show ip dhcp pool command, what does the current index refer to?
The current index refers to total addresses as well as leased addresses
Portfolio Task – What is a DHCP relay agent and why is it needed?
The DHCP relay agent is regarded as a host that would forward the DHCP packets between the servers and the clients. The agents are therefore needed for the purposes of forwarding requests as well as replies between the servers and clients.
Demonstrate this to your tutor that it works and have a mark recorded.
Follow the same procedure as above and configure DHCPv4 for the network with the topology shown below and with the following requirements
R1 should serve as the DCHP server for the 100.1.1.0/24 network
R2 should serve as the DHCP server for the 200.2.2.0/24 network
The first 5 addresses in the pools should be excluded

On PC-A and PC-B, issue the ipconfig /all command to verify that the PCs have received IP address information from the DHCP server on R2. Paste a copy of the IP configurations below
First, R1 needs to be configured as follows

Workshop 3
Why may our switch have an IP address, given that switches make their switching decisions based on MAC addresses?
The switch is essentially assigned the IP address for the purposes of allowing IP communication across the two devices. The IP address also gives room for the management of the switch over the given network and even makes use of the most fundamental protocols like SNMP. It is worth noting that the IP address would be configured based on the logical interface, which is denoted as the VLAN or the management domain. Commonly, default VLAN 1 would act as the switch for the NIC before connecting to the LAN and send the IP packets. The IP_ADDRESS SUBNET_MASK would serve as the interface subcommand. The VLAN 1 interface would be assigned the “no shutdown” subcommand while the ip_default-gateway ensures that the configuration command is able to configure to the necessary default gateway. It should essentially be noted that VLANs would rarely have an IP that is essentially assigned as it is the way with servers and computers (Gowda et al. 2012). However, VLANs would have networks assigned to them as far as the connectivity of the subnets is put into consideration. Perhaps, the application of IP-based switches at Layer 2 plays a fundamental role of eliminating the scaling problem because the collisions would be filtered.
The transmissions would end up being governed by the broadcast domain and the behavior of the engaged switches in a given network (Gowda et al. 2012). Commonly, the broadcast domain would end up defining the significant area within which the broadcast frame is likely to propagate. For instance, when an ARP request is shared by PC-C, then this would result into a broadcast frame that would end up propagating through the concerned switches to the routers available in the network. In most circumstances, most of the requests in the network would utilize the broadcast frame that would be received at switch 1. In essence, the frames are likely to be extended to all available directions while the rest of the switches would end up following suit (Basso et al. 2019). VLANs would largely work in a way deemed close to the Layer 3 IP-based network. In the end, the available nodes found on the 192.168.1.0 network need to proceed to the router in the course of communicating with the ones found on the network 192.168.2.0 regardless of the fact that all the devices may be attached to the same switch.
Assigning the IP address and configuration of the switches to a range of the VLANs is thought to essentially reduce the required size of every broadcast domain. This means that the magnitude of the overhead traffic is likely to be lower thereby reducing the bandwidth competition for the available data traffic. It is worth noting that a node in a network is more likely to experience a lesser broadcast traffic. In such instances, the switch in the network would exhibit the forwarding behavior, which is fundamentally based on the available MAC address that is commonly stored in what is referred to as the source address table (Gowda et al. 2012). This means that a number of rules would be followed in the process.
Why is VLAN trunking used?
The understanding of VLAN trunking is equally important to the fundamental use of trunking in the VLAN configurations. In networking, a trunk is simply a single channel attached to the communication known for allowing a range of entities on one end to essentially correspond with the appropriate entity noted at the other end. In most cases, it would be referred to as a link known for carrying a range of the signals thereby paving way for efficient network access across two significant nodes. Trunking is a term applied with reference to telecommunications while denoting a connection of the switching centers while fostering the creation of the multiple signal links (Rahmanzi et al. 2020). VLAN trunking is deemed important to most of the VLAN configurations due to its capacity of extending the VLAN across the available network. Upon implementation of the multiple VLANs in the network, most of the trunk links are important in ensuring that a good range of the VLAN signals remain appropriately segregated for each signal for them to reach the intended destination (Prasad et al. 2016). Therefore, the key purpose of having the VLAN trunking in the network shown is to essentially pave way for the movement of the necessary traffic to separate parts of the entire network said to be configured as VLAN. This function is said to be more effective due to the fact that a range of the VLANs can easily be configured on a given single port.
When the system has several VLANs on a given port, this means that the system would establish a way of differentiating them as well as the routing signals. It is worth noting that the VLAN trunking port would always make use of the identifying tags in marking the frames as they make a passage between the switches. Notably, the most noticeable trunking protocol that can be utilized in the network is the IEEE 802.1Q as it adds a significant tag to the considerable Ethernet frame that would ultimately pass through as it marks its inclination to a more specific VLAN (Rahmanzi et al. 2020). Apparently, the tag, which has the MAC address with it, helps in routing the Ethernet frame to be linked to the appropriate endpoint before passing across the necessary trunked link. It should be noted that the IEEE 802. 1Q is essentially regarded as one of the open standard protocols especially when the equipment or the device is utilized by a number of vendors. In this case, the VLAN Trunking protocol would be deemed significant in the configuration of the new VLAN on the available VTP server (Prasad et al. 2016). This means that the VTP would ensure that there is an even and automatic distribution to the switches thereby attracting a reduction of the configuration time.
However, maintenance on the VLAN trunking is said to be a necessary process in which the considerable switch-forward tables are expected to be updated especially when the network experiences the topology changes (Prasad et al. 2016). The tables need to be refreshed for the purposes of paving way for the emergence of the new changes and the clearance of the old forwarding frames. In the process, one is likely to encounter both the asymmetrical and the symmetrical trunking as far as the transmission of packets is put into consideration.
What is ‘router on a stick’ and how does it differ from the vlan exercise configuration you have undertook is this workshop
“A router on a stick”, sometimes referred to as the one-armed router, is simply a router that has with it a single logical or physical connection or link to the network. A “router on a stick” largely supports the forward traffic that prevails between the local hosts found on different logical routing domains, or designed to provide for the routing table distribution, relay and administration. This kind of routers is commonly known for performing the appropriate traffic forwarding commonly implemented on the VLANs. Notably, they would make use of the one Ethernet network interface believed to be part of the virtual LANs (Durres 2019). In this context, the VLAN is said to be in a capacity of giving room to a range of the virtual LANs to fundamentally coexist on a similar physical LAN. The implication is that two significant machines can be linked to a common switch and still fail in sending the Ethernet frames to one another despite crossing over the same wires. In a more specific scenario, the Router-on-a-stick (ROAS) may be understood as a significant feature known for allowing the network to route the packets to the relevant subnets said to be associated to the VLANs believed to be connected to router 802.1Q trunk (Prasad et al. 2016). ROAS would commonly make use of the router VLAN trunking configuration in giving the router the necessary logical interface that can be associated to the VLAN.
There is a big difference between the VLAN configuration used in this case, and the router-on-a-stick. First, the VLAN configuration used in the context, or the Inter VLAN Routing, is essentially denoted as the process used in making separate VLANs communicates with one another without consideration the location of the VLANs (Prasad et al. 2016). On the other hand, Router-on-a-stick (ROAS) utilizes the router’s interface in dividing it into necessary sub-interfaces that would end up acting as the default gateways to the VLANs. In this case, the ROAS would serve as the technique applied in the implementation of the inter VLAN routing with the help of a physical router connected to the appropriate switches.
Secondly, the VLAN configuration in this context, would allow a layer -3 device or the router to facilitate communication across different VLANs. This implies that the moment a host is essentially separated with the help of the VLAN, and then the member hosts having the same VLAN would be allowed to communicate with one another (Durres 2019). However, the ROAS is different in the sense that it would call for a physical link bearing a trunk logical interface. Apparently, the VLAN members, or the member hosts, would be allowed to configure with the help of the sub-interface address which would also behave as a default gateway. The ROAS only allows for a single router physical interface. This is different from the VLAN configuration which takes advantage of the packets that would end up arriving on the router via an interface.
Workshop 4
1) What are the advantages and disadvantages of setting the warning level to a high value?
Setting higher values in a Syslog is advantageous in terms of minimizing traffic. Secondly, higher values allow the Syslog to make use of less important network in the course of generating the Syslog traffic attached to critical events (Vaarandi et al. 2018). However, higher warning values in Syslog may have their drawbacks as well. Notably, a critical error may never be send when the system is offline.
2) With respect to NTP server what is meant by the stratum level? Why is it important to have the timestamping?
The NTP stratum level denotes the hierarchy of the time servers across the NTP network. When the stratum level ranges from 0-15; this indicates the distance of the device to the significant reference clock. When the stratum is zero, this means that the device has a direct connection to the GPS antenna (Lin 2018). On the other hand, timestamps are regarded as important in the sense that they always keep a record of when details, data or information is created, exchanged or even deleted online.
3) What are the strengths and weaknesses of logging events in the computing and networking environment?
Most of the users of the networking environment find it necessary to make use of the logging events. One of the key advantages of the logging events is the unified storage (Lin 2018). Based on this advantage, the system takes advantage of centralized logging, standardized log data and time saving. The second advantage is system monitoring and alerts. The logging events have an access to a pool of the log management tools known for providing the customizable real-time alerts which enable one to react the soonest (Li et al. 2018). Other areas of strength include improved security, data analytics, and log file parsing as well as better troubleshooting. Despite enjoying a range of the areas of strength, logging events still face security challenges.
Workshop 5
What is a tunnel used for?
In studying networks and the routing protocols, tunnels play the most fundamental role. Tunnels are known for providing the means of transport for the protocols that do necessarily need the underlying network infrastructure. These means are primordially implemented at the time when the network or the crossed network is lacking the appropriate protocol support that is being transported. The same protocol may not be in a position in performing the dissemination of the packet as result of lack of necessary information linked to the routing mechanism. Under general terms, tunnels would be regarded as a platform known for connecting the remote and physically separated sites in a given existing network (Yu et al. 2017). This is dubbed as routing over a given public infrastructure like the Internet. In the described context, tunnels would be engaged in creating the VPN connection across two or more remote sites. This means that a fresh header would be utilized in the encapsulation of the packets that are destined for the remote private networks.
The operational principle of tunnels revolves around creation of the virtual network over a given underlay network for the purposes of facilitating a logical interface, which is known for emulating direct physical link that would establish a connection between two significant sites. It is worth noting that a tunnel interface would proceed by encapsulating the relevant traffic with an intention of crossing the network with the help of the intermediate protocol (Ogudo 2019). The latter is commonly encapsulated inside the transport protocol known for passing via underlying infrastructure. The tunneling process would also end up encapsulating the data packets attached to one protocol before transporting the same packets that would remain unchanged over the foreign network. Different from encapsulation, it is believed that tunneling would give room for the same-layer protocol or the lower-layer protocol, which can be conducted via the same tunnel.
Moreover, a tunnel interface is essentially regarded as the virtual interface which would appear in three major components. The first component is the transport protocol, which is known for carrying the encapsulated protocol. Secondly, the carrier protocol is engaged in the encapsulating process as it happens with STUN, GRE, MPLS and L2TP. Lastly, the passenger protocol is the protocol that needs to be encapsulated and these include the IPX, AppleTalk and CLNS. Some of the protocols that have attracted the attention of the network developers include the Generic Routing Encapsulation, denoted as the GRE, which can essentially be defined in the RFC 2784. The GRE is known to be a carrier protocol, which can be used in a range of the underlying transport protocols. GRE has the capacity of carrying with it many passenger protocols (Ogudo 2019). On the other hand, the Block Serial Tunnel, also denoted as BSTUN, is known for enabling support for the devices in the light of Bisync data-link protocol. The protocol would allow the enterprises to ferry the Bisync traffic over the significant network known for supporting the multiprotocol traffic and the Systems Network Architecture. Therefore, this type of a tunnel would end up eliminating the essence of separating the Bisync facilities. Another tunnel is the Connectionless Network Service, denoted as CLNS protocol. This presents a standard for the relevant network layer linked to the OSI model.
It should be noted that the IP traffic can still be ferried or transported over the CLNS as it is with the Data Communications Channel of the SONET Ring. Furthermore, the IP introduced over the CTunnel would be a virtual interface that would only bolster the possible interactions with the CLNS networks. The Unidirectional Link Routing, or the UDLR tunnels, is known for facilitating the necessary mechanisms that would allow the involved router to essentially emulate the convenient bidirectional link for the purposes of enabling the routing process for the multicast and the unicast packets, which would be transported over the physical unidirectional interface. Notable examples would be attached to the broadcast satellite link (Yu et al. 2017). Tunneling, or tunnels, is believed to be significant in a number of ways and in different situations. Tunnels can be appropriate in connecting the discontinuous sub-networks and even allow the virtual private networks in the Wide Area Network. Tunneling can still enable most of the multiprotocol local networks across the single protocol backbone, as well as facilitate the workarounds for a range of the networks with the help of the protocols.
How would you make it secure?
Tunnels need to be secure in most cases. Under common circumstances, the tunneling scheme is essentially designed for the purposes of meeting the characteristics of the policy tools. The latter is known for mapping the situational awareness before picking on appropriate tools that would make sure that the network under consideration is secure. In a network, all the nodes will follow the appropriate security policy said to dictate the kind of the response the system would give to the network threats and conditions at the same time. In the process of ensuring that the tunnels remain more secure and entrusted, two significant approaches have been considered to fulfill the condition (Glazemakers et al. 2018). The first one is the use of VPN in forming what is referred to as the VPN tunneling. The latter describes the significant process in which data is appropriately and securely transported from one component, network or device to the next one with the support of the non-secure environment, which is believed to have no compromised privacy.
VPN tunneling means protection of data through the process of repackaging for it to take a different form. It is worth noting that VPN tunneling has to deploy significant concepts referred to data encryption and encapsulating for the purposes of ensuring that data is safely transmitted over the given traffic. This means that encapsulation would end up insulating the significant data packet from the rest of the data taking the same channel in the same network. In essence, encryption would simply make the available data unreadable or invisible to even the criminals and even the surveillance agents. It should be noted that a range of the VPNs would make use of the gateways in providing the needful remote access due to the fact a user would end up logging on the private network (Jahan et al. 2017). The VPN tunneling technology is equally supported by other three technologies which include the IPsec, L2TP and PPTP. The Point-to-point tunneling protocol, also denoted as PPTP, is believed to be one of the widely used, oldest and fastest tunneling protocols to have ever been used.
However, it has the lowest level of encryption and therefore gain relevance in numerous applications in which speed is the priority over the security concerns. The Layer 2 Tunneling Protocol, also denoted as L2TP, never provides the confidentiality of data by itself but ends up relying on a separate protocol that would help in wrapping the entire data. Perhaps, this would attract two significant layers of encryption deemed enough in protecting the data that passes through the tunnel. Common cases would find it more appropriate in using both the IPsec and L2TP at the same time (Jahan et al. 2017). However, it is believed that double encapsulation process would end up making the duo slower especially when compared to the PPTP. The duo can still encounter the bypassing restrictions due to the fact that they commonly make use of the fixed ports, which can easily be detected by the VPN blocking software. Despite some of the drawbacks in attaining the necessary security standards, it is good to note that there are different types of VPNs that would be applied alongside the tunneling process.
The first one is the NordVPN, which can provide the required stability and speed at the same time. The privacy served by the platform is believed to be safeguarding via implementation of the strict no-logs policy and kill switch. Other platforms include the ExpressVPN and the CyberGhost, the privateVPN and the HamaVPN. The second means used by tunnels in attaining the desirable security level is making use of the GRE. The Generic Routing Encapsulation (GRE) is known for making it workable in encapsulating the datagram, which needs to be transmitted to another available network layer protocol. While there are other methods that can be used in ensuring that there is data transmission encryption, GRE is said to have only facilitated the low overhead tunnel. The encapsulation format directed to GRE is essentially defined in either the RFC1702 or RFC1701. This can still be utilized in supporting different routing protocols that cannot be limited to the IGRP, OSPF and RIS.
Workshop 6
What is a loopback address and why is it used?
A loopback address is essentially regarded as the special IP address 127.0.0.1 commonly reserved by the InterNIC for the meaningful testing of the network cards. In essence, the IP address significantly corresponds to the relevant software loopback interface attached to the network card. It should be noted that neither physical connection nor hardware is engaged in the network. Loopback address paves way for the application of the most reliable technique in testing the working status or the functionality of the Ethernet card as well as the relevant drivers and the software in absence of the physical network. This gives chance to the IT professionals in testing the IP software without considering the corrupted the drivers (Deisinger et al. 2019). Such tests can be conducted with the help of the loopback address such as the TCP/IP utility ping. It is good to note that data packets identified on the loopback address can be re-routed back to the significant originating node without a necessary engagement of the modification or alteration process. The check tests are commonly extended to the validation of the connected physical network with the attention given to the working mechanisms of the installed TCP/IP stack.
The available data packet would not abandon the host system and would obviously be sent back to the relevant source application. While focusing on the IP or network based applications, tests are normally introduced on the virtual network interface card. The actions of the latter are essentially added to the available physical network card thereby giving room for the users to work on the tests of an application using an instant server or client provided on the same machine. This kind of the ability is driven to the transmission network that rarely needs an access to the physical network (Gardner et al. 2017). Most of the developers have agreed on IPv4 127.0.0.1 as the most convenient loopback address that can ever be used. In addition, the loopback address has been linked to the SRX 210 Services Gateway. Based on this, it is said that the address would ensure that the working component or the significant device in the network is able to serve an IP address that finds the significant use in the management of the applications. This means that the loopback address needs to be available to all the hosts said to be making attempts of routing the packets to the available device.
Again, the loopback address needs to be active and should therefore reside on the available interface. While setting up a loopback address, one has to ensure that the engaged device is able to receive the necessary packets said to be addressed to the loopback address. Other applications of the loopback address are seen with the Network Time Protocol (NTP), the Remote Authentication Dial-In-User Service (RADIUS) as well as the Terminal Access Controller Access Control System plus (TACACS+). The Internet Protocol would still specify the loopback network having an IP address denoted as 127.0.0.0/8. This means that the IP implementations would end up supporting the concerned loopback interface which can effectively represent the significant loopback facility (Deisinger et al. 2019). Any traffic that would be sent by the computer program would be addressed to the same device or the computer. A network device, in any network, would also include what is referred to as the Internal Loopback Address, which is denoted as 1o0.16384. This would be utilized in denoting a logical unit that is numbered as 16384. This kind of the loopback interface would be utilized in identifying the device as well as determine whether it is online or not.

What is an Autonomous system and what role does BGP have in their use?
In most networks or internet, it is obvious that one would interact with the Autonomous System (AS) and the fundamental role of the Border Gateway Protocol (BGP). Notably, the Autonomous System is regarded as the collection of the IP routing prefixes based on the control of the network operators, who work in charge of the single administrative domain or entity. The latter is said to present the most common and explicitly defined routing rules or policy attached to the internet. The Autonomous System is essentially denoted as the routing domain which is assigned the Autonomous System Number, believed to be a globally unique number (Ahmed et al. 2019). In some cases, and based on the constitution of the ASN, an Autonomous System would simply point at the collection of routers that bear prefixes as well as the routing polices served under the same administrative control.
Most of the developers point at a company, network service provider, a department, a division or even a representative group within a group of companies. The system is believed to represent connected groups or the blocks of the IP addresses, which are denoted as the IP prefixes. It is worth noting that an IP prefix denotes a group of the IP addresses that are essentially expressed in terms of the CIDR form which takes the bits or the address like 128.6.0.0/16. It should further be noted that routers in a given AS system would make the significant use of the Interior Gateway Protocol, denoted as IGP, known for handling the routing across the nodes found inside the system (Witono and Yazid 2020). Some of the most common gateway protocols found on the interior side of the system are not limited to the EIGRP, IS-IS, RIP and OSPF. Apart from the meaning of the Autonomous System in the network, it is also recommendable to understand the role of BGP. By definition, the Border Gateway Protocol, denoted as BGP, is essentially a standardized gateway protocol that is fundamentally designed for exchanging the routing, as well as reachability of information within the Autonomous Systems in an internet.
It is worth noting BGP is categorized as the path vector routing protocol engaged in the routing decisions associated to the rule-sets, the network policies and the paths said to have been configured by an administrator. The evident role of BGP in an autonomous system is grounded on routing with the application inclined to what is referred to as the Internal BGP. The BGP neighbors, known as peers, are essentially established on the basis of the manual configuration across the routers that would end up creating the TCP session especially on port 179. In case of a BGP speaker, it would end up sending the 19-byte keep-alive messages in every sixty seconds for the purposes of maintaining the connection. Across all common routing protocols, it is believed that BGP stands out more unique due to its fundamental use of the TCP denoted s the transport protocol (Ahmed et al. 2019). The Internal BGP normally occurs then the BGP is running across the two peers found in the Autonomous System.
The University of Wolverhampton main site has an AS number, what is it?
The University of Wolverhampton, in this context plays the fundamental role of the network operator. The understanding of the AS Number is first based on the definition of an Autonomous System, which takes into account a group of the IP address network said to be managed by common network operators. Notably, every AS is essentially linked to a more specific number which stands out as the AS identifier known for playing a fundamental role, in terms of exchanging the external routing information. Some of the sampled exterior routing protocols include the BGP, which is significantly utilized in exchanging the routing details (Patel et al. 2018). Based on this, ASN would easily be denoted as the globally unique identifier said to define a group of the IP prefixes that are controlled by the network operators, in maintaining a single routing policy that is clearly defined.
The ASN gives room for the AS in exchanging the routing information with the rest of the autonomous systems. Most of the network operators would be in need of the ASNs for the purposes of regulating the routing process across the networks. The common types of the ASNs include the private and the public ASN. The private ASN can essentially be used in the system for the purposes of running the communication with the help of the BGP in the presence of another provider. On the other hand, the public ASN cannot be delinked from the exchange of information through the internet. Most of the network operators would still encounter different formats of ASN (Yacobi-Keller et al. 2019). First, a 2-byte ASN is largely regarded as the 16-bit number type that has the capacity of providing from 0 to 65535 ASNs. However, it is worth noting that the Internet Assigned Numbers Authority, denoted as IANA, is said to have aside 1023 for the purposes of facilitating the private use. The second fundamental format is the 4-byte ASN, which is the 32-bit number ASN type known for providing up to 4294967296 ASNs.
Notably, IANA is said to have reserved the several ASNs, which include the ones that range from 4200000000 to around 4294967294 for the purposes of addressing the private uses. Explicit details regarding the working mechanism of ASN further makes it easier to understand the meaning and the need to have the numbers in the network. First, when an AS calls for the internet connection, or sometimes a connection that would be attached to the separate network, then the system would need the BGP that would take advantage of the manual configuration (Yacobi-Keller et al. 2019). Perhaps, one of such configurations covers the identification of the AS engaged in forming the connection. Obtaining an ASN demands the involvement of the American Registry, or any other registered registry, attached to the Internet Numbers. One of the most fundamental conditions is that the concerned party would be required to have a multi-homed site or the unique routing policy.
References
Abdullah, S.A., 2019. SEUI-64, bits an IPv6 addressing strategy to mitigate reconnaissance attacks. Engineering Science and Technology, an International Journal, 22(2), pp.667- 672.
Ahmed, R.F., Khan, A. and Rizwan, M., 2019. Collection Of Autonomous System Level Topology Using Looking Glass Servers. Pakistan Journal of Science, 71(4), p.69.
Basso, C., Damon, P. and Schmitt, J.B., International Business Machines Corp, 2019. Method for using an IP address-based routing protocol in an ATM environment. U.S. Patent 5,673,263.
Deisinger, M.V. and Bergerson, R.L., Unisys Corp, 2019. Systems and methods for configuring an IPv4 process without associating the IPv4 process with an IP loopback address. U.S. Patent 10,454,881.
Durres, A., 2019. How Can Configure Five Different Networks/Vlans With One Port Of Router. European Journal of Engineering and Technology Vol, 7(6).
Gardner, J. and Mlodzik, E.A., Sprint Communications Co LP, 2017. Domain name system (DNS) query response providing loop-back internet protocol (IP) address to non- activated mobile communication device. U.S. Patent 9,686,226.
Glazemakers, K. and Allansson, P.J., Cryptzone North America Inc, 2018. Multi-tunneling virtual network adapter. U.S. Patent 9,906,497.
Gowda, N.P.N., Sastry, S., Sankar, R., Haltore, K., Basavaiah, M., Merchant, S. and Iyer, S.P., Cisco Technology Inc, 2012. Distributed IP gateway based on sharing a MAC address and IP address concurrently between a first network switching device and a second network switching device. U.S. Patent 8,166,187.
Goyal, V. and Arora, G., 2017. Implementation of enhanced interior gateway routing protocol (EIGRP) in IPv6 network. Research Journal of Advanced Engineering and Science, 2(1), pp.90-95.
Jahan, S., Rahman, M.S. and Saha, S., 2017, January. Application specific tunneling protocol selection for Virtual Private Networks. In 2017 International Conference on Networking, Systems and Security (NSysS) (pp. 39-44). IEEE.
Kumar, G. and Tomar, P., 2020. IPv6 Addressing Scheme with a Secured Duplicate Address Detection. IETE Journal of Research, pp.1-8.
Li, T., Ma, J. and Sun, C., 2018. Dlog: diagnosing router events with syslogs for anomaly detection. The Journal of Supercomputing, 74(2), pp.845-867.
Ogudo, K.A., 2019, August. Analyzing Generic Routing Encapsulation (GRE) and IP Security (IPSec) Tunneling Protocols for Secured Communication over Public Networks. In 2019 International Conference on Advances in Big Data, Computing and Data Communication Systems (icABCD) (pp. 1-9). IEEE.
Patel, K., Snijders, J. and Housley, R., 2018. A Profile for Autonomous System Provider Authorization draft-azimov-sidrops-aspa-profile-01.
Prasad, N.H., Reddy, B.K., Amarnath, B. and Puthanial, M., 2016. Intervlan Routing and Various Configurations on Vlan in a Network using Cisco Packet Tracer. International Journal for Innovative Research in Science and Technology, 2(11), pp.749-758.
Prasad, N.H., Reddy, B.K., Amarnath, B. and Puthanial, M., 2016. Intervlan Routing and Various Configurations on Vlan in a Network using Cisco Packet Tracer. International Journal for Innovative Research in Science and Technology, 2(11), pp.749-758.
Rahmanzi, M.Z., Fitri, I. and Aningsih, A., 2020. Load Balancing Performance in Etherchannel Technology Using the VLAN Trunking Protocol (VTP) Method. Jurnal Mantik, 3(4, Feb), pp.540-547.
Vaarandi, R., Blumbergs, B. and Kont, M., 2018, April. An unsupervised framework for detecting anomalous messages from syslog log files. In NOMS 2018-2018 IEEE/IFIP Network Operations and Management Symposium (pp. 1-6). IEEE.
Witono, T. and Yazid, S., 2020. Portrait of Indonesia’s Internet Topology at the Autonomous System Level. In Computational Science and Technology (pp. 237-246). Springer, Singapore.
Yacobi-Keller, U., Savin, E., Fabian, B. and Ermakova, T., 2019. Towards geographical analysis of the autonomous system network. International Journal of Networking and Virtual Organisations, 21(3), pp.379-397.
Yu, B., Smith, L. and Threefoot, M., Infoblox Inc, 2017. Behavior analysis based DNS tunneling detection and classification framework for network security. U.S. Patent 9,794,229.
- 24/7 Customer Support
- 100% Customer Satisfaction
- No Privacy Violation
- Quick Services
- Subject Experts



