Penetration Testing: Unveiling Security Weaknesses and Mitigation Strategies
(MacKenzie, 2012) Describes a penetration test or as informally known as a pen test, as a form of an attack that is purposely injected into on a computer system that essentially scans the computer system and looks for any security weaknesses, potentially gaining access to the network's features and data. The penetration test process typically identifies the target systems and a particular goal after which it reviews available information and hence undertakes various means to attain the set goal. The goals of a penetration test is said to vary depending on the type of activity approved for any given engagement with the primary purpose that is mainly focused on finding vulnerabilities that could be exploited by a nefarious actor, and as a result informs the client of those vulnerabilities and recommends necessary mitigation strategies, (Hunt, 2012).
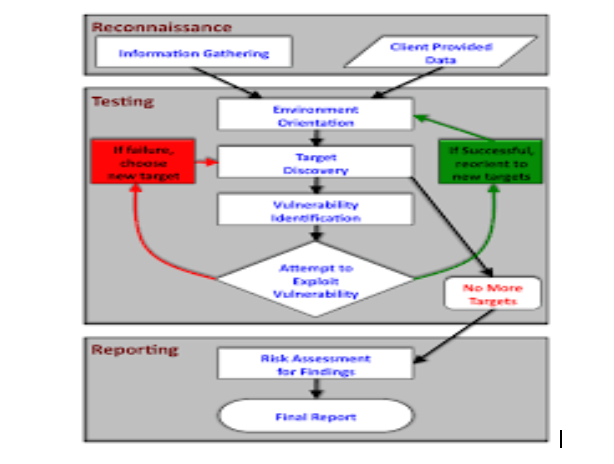
Based on a report by (Hunt, 2012), a penetration test target can be either a white box, implying that it provides background and system information; or black box, indicating that it only provides basic or no information at all except the company name for instance. Necessarily, a penetration test helps determine whether a system is vulnerable to attack, whether the defenses of a system are sufficient, and which defenses (if any) are susceptible. The process of penetration testing involves a sequence of activities as shown below:
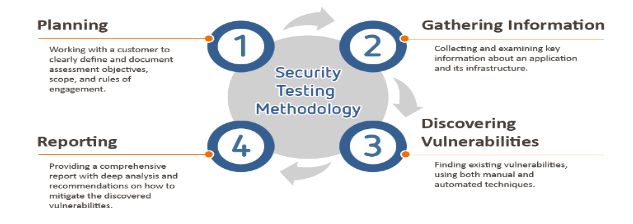 This form of test applies a six basic attack sequence steps to determine vulnerabilities. These measures include; finding an exploitable vulnerability, designing an offense around it, testing the attack, seizing a line in use, entering the attack and finally exploiting the entry for information recovery as seen in the diagram below, (Stephen Northcutt, 2006). For students seeking data analysis dissertation help, understanding these processes is crucial for evaluating system vulnerabilities and implementing effective security measures.
This form of test applies a six basic attack sequence steps to determine vulnerabilities. These measures include; finding an exploitable vulnerability, designing an offense around it, testing the attack, seizing a line in use, entering the attack and finally exploiting the entry for information recovery as seen in the diagram below, (Stephen Northcutt, 2006). For students seeking data analysis dissertation help, understanding these processes is crucial for evaluating system vulnerabilities and implementing effective security measures. 
Security, especially in small and medium enterprises, is an essential factor. Based on a report on SME security by the GFI Software’s (2009), it was noted that most IT safety in a company assume that all that is necessary for securing a system is install anti-virus and anti-spam software. However, this software often fails to realize the different internal threats that could pose a risk to their businesses, (Darmanin). However, what such security measures fail to take
note is that in some instances, threats come from the same people they are being protected for. This security software is usually installed to protect the employee’s information from leakage and safeguard their work. Nevertheless, based on evidence from this GFI report, in some cases, the employees themselves tend to be the threat. Disgruntled employees, for instance, those facing redundancy, might decide to seek ‘revenge' on the company in a case where they might be under dismissal.
They tend to take their revenge at times by stealing confidential data and in a worst case possibly passing it on to a competitor. Some of this information can be sensitive, and such information in the wrong hands could lead to a company's downfall. This SME Security Report, conducted by GFI Software in February 2009 across IT decision-makers in UK SMEs, showed that among basics of IT security 96% are installed anti-viruses, 85% installed anti-spam software and 92% assign user passwords. Only about 45% of respondents had established preventive measures protecting their systems against portable storage devices which this disgruntled users can use to copy data off the company's network, (Darmanin, 2009).
In the case of NVQ, such threat where employees tend to expose company information intentionally can be quite likely. This is primarily due to the ignorance is seen from the management. The administration of this firm seems to have zero knowledge regarding any necessary security measure nor does she care about it much. She believes that that the work of the IT security personnel who are also part of the employees and hence part of the threat. This can be depicted from the words of the managing directors when she is suggested on the possibility of the company considering to pay for a security company to conduct a Pentest on NVQ. Her reply is entirely ignorant; “Security is a technical issue, and that is why she employed her there is no need to waste more management time on yet more meetings!”
With such ignorance and lack of adequate security measures, the NVQ system might be prone to other threats such as hackers who are over time evolving with the evolution of technology, (MacKenzie, 2012). Nevertheless, with the application of pen test in the NVQ firm, it enhances security eliminating any form of security threat in the system. This is necessarily by identify the various vulnerabilities and risks that the system might be prone to and testing how much this vulnerabilities and risks might affect the system. Penetration testing unlike other security measures exploits these vulnerabilities and can determine whether unauthorized access, illegal transfer of data or other malicious activities are possible, (MacKenzie, 2012). It helps prevent intentional leaks of evidence from vengeful employees by checking every activity carried out in any portable device being attached to the system.
This form of security measure as well provides control over the various processes around the networks and applications. It detects any malicious activities occurring from both outside the network trying to come in (external testing) or from inside the network. With penetration testing hence, NVQ would be assured of a secure system with quite minimal chances of attacks or failure, (Darmanin, 2009). In conclusion, based on the above review, the managing director of NVQ in her statement; “Security is a technical issue, and that is why she employed her there is no need to waste more management time on yet more meetings!” was quite wrong as the NVQ firm would do much better with a pen test. This would assure the company of absolute security and that its data and secrets are safe from both inside and outside threats. Thereby, to maintain security for data and

information, the NVQ managing director should allow for another company to join in and conduct pen testing on NVQ systems. As reported by (Stephen Northcutt, 2006), pen testers such as the CORE IMPACT are quite fast and can do scanning, penetration, clean up and reporting at more than double the speed the humans can hence saving quality time and providing essential and high-quality security measure for the company.
Take a deeper dive into Numeracy, Data and IT with our additional resources.
References
Darmanin, J., 2009. UK SMEs underestimate danger posed by their employees. London, UK:
GFI TechTalk.
Hunt, E., 2012. Computer Penetration Programs and the Implications for Cyberwar. IEEE Annals of the History of Computing, Volume Vol. 3, p. p. 34.
MacKenzie, D. a. G. P., 2012. Penetration Testing. New York, NY: McGraw-Hill.
Stephen Northcutt, J. S. D. S. R. R. S. a. S. M., 2006. Penetration Testing: Assessing Your Overall Security Before Attackers Do. London, UK: Core Impact.
- 24/7 Customer Support
- 100% Customer Satisfaction
- No Privacy Violation
- Quick Services
- Subject Experts



